Intelligent voice product privacy invasion detection method based on energy consumption
A technology of intelligent voice and detection method, which is applied in voice analysis, instrumentation, electrical digital data processing, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
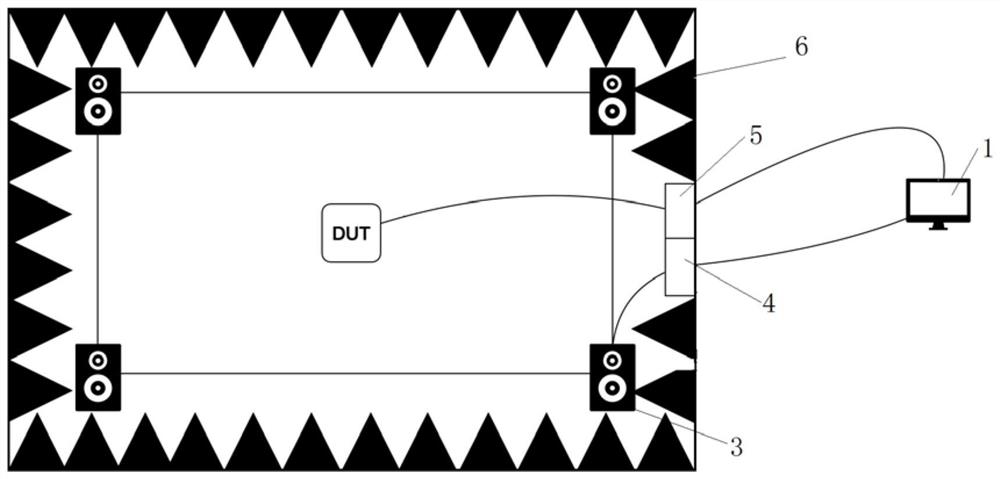
[0026] Taking Tmall Elf Cube 2 as an example, the method for detecting privacy violations of intelligent voice products based on energy consumption of the present invention will be further described in detail.
[0027] Step (1): Connect the smart voice product (DUT) to be tested, that is, Tmall Genie Fangtang 2, to the energy consumption detection device, manually control it to work in each state, record the energy consumption map in each state, Especially the standby state, recording state, network transmission state and the coexistence of two or more of them.
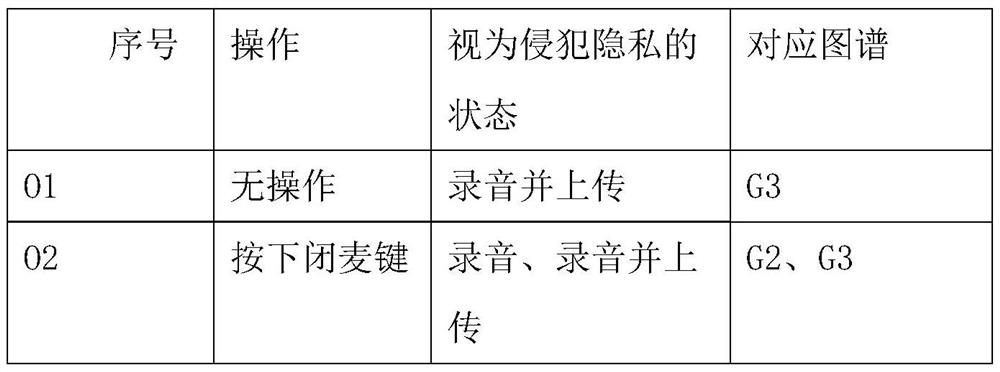
[0028] Specifically, such as turning off other alarm clocks and device pairing functions of Tmall Elf Cube 2, connecting the power supply part to the energy detection device, recording the spectrum in the standby state, the spectrum in the recording state, recording and uploading the state after successful wake-up Maps, etc., if their map numbers are G1, G2, G3, etc. respectively. The standby state here refers to the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com