Hardware implementation device of SM3 algorithm
A hardware implementation and algorithm technology, applied in the field of information security, can solve the problems of large hardware area and high cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
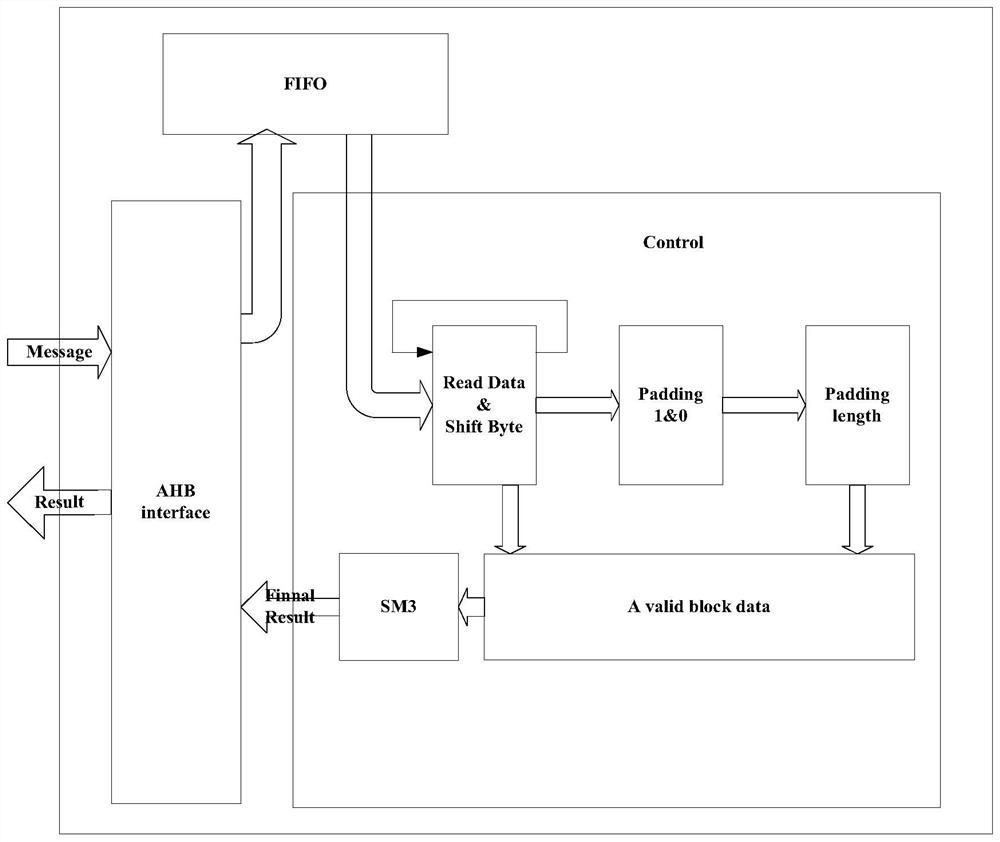
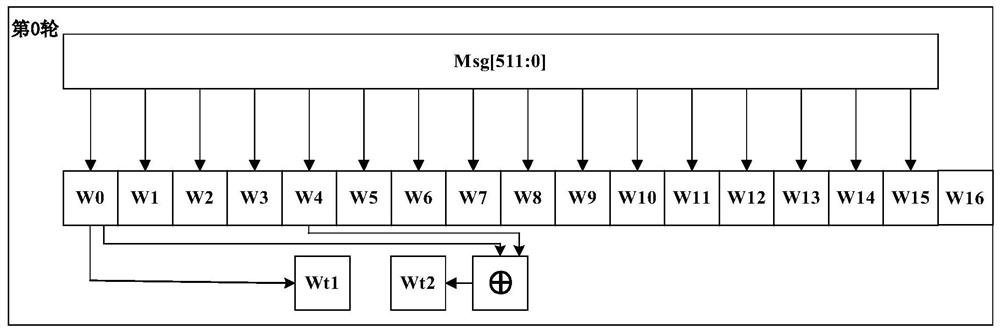
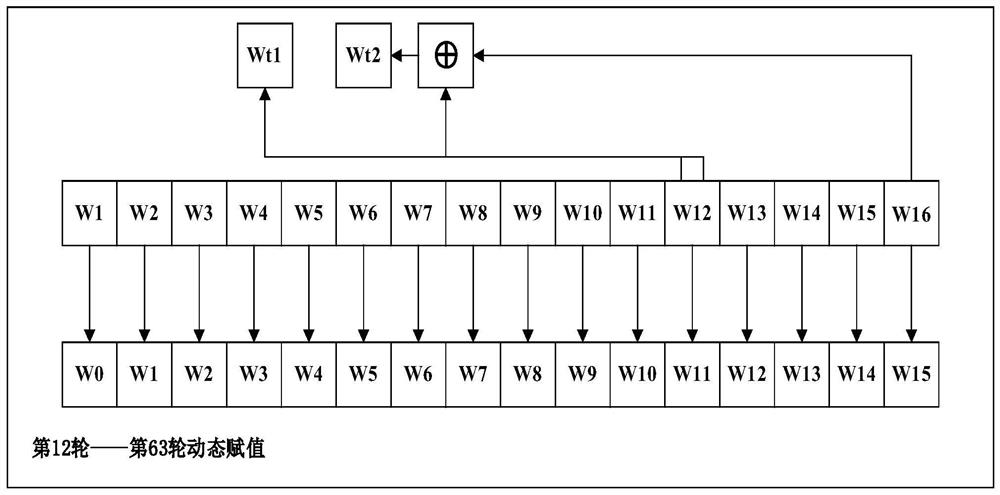
[0037] The main idea of the present invention is that the device adopts 16 basic message word registers and 3 dynamic message word registers, based on the characteristics of the SM3 algorithm itself: in the calculation of 64 rounds, in the calculation of the 0th round to the 11th round, The 16 basic message word registers are not reassigned. Starting from the 12th round of calculation, the 16 basic message word registers are dynamically assigned. The present invention can realize the SM3 algorithm by using 19 registers, which greatly reduces the hardware based on the SM3 algorithm. area.
[0038] The hardware implementation device of SM3 algorithm, such as figure 1 As shown, it includes an interface module (AHB interface) for receiving the original message data (Message) and outputting the encrypted result (Result), which allows the SM3 module to be mounted on the AHB bus, and the SM3 module can be accessed through the AHB bus;
[0039] Also includes: FIFO storage module fo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com