4G and 5G air interface attack detection method based on signal and signaling fingerprint
An attack detection and fingerprinting technology, applied in the field of network security, can solve problems such as high hardware requirements, difficult daily implementation and deployment, and affecting normal communication of users, and achieve the effect of simple deployment, low cost, and easy deployment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] Preferred examples of the present invention will be described in detail below in conjunction with the accompanying drawings.
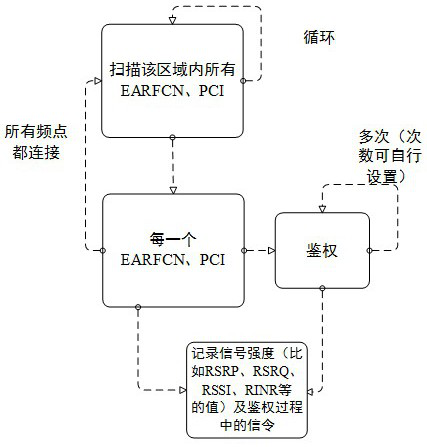
[0020] The attack detection process of the present invention is as follows figure 1 As shown, it includes.
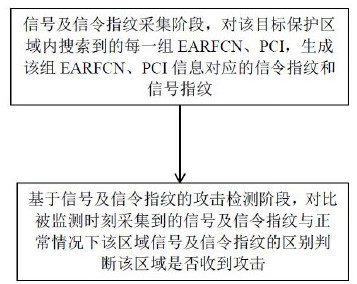
[0021] 1. The signal and signaling fingerprint collection stage is as follows: figure 2 shown.
[0022] 1) Search for EARFCN and PCI in each protected area; EARFCN (E-UTRA Absolute Radio Frequency Channel Number) is the center frequency of the carrier, which uniquely identifies the frequency range of an LTE system; PCI (Physical Cell Identifier) is the physical cell identifier , the two parameters of PCI and EARFCN together uniquely determine a frequency point.
[0023] 2) In a protected area, initiate a specific number of authentication requests for each searched EARFCN and PCI within a fixed time interval, and obtain authentication signaling and signal strength parameters (for example, RSRP, RSRQ, RSSI , RINR, etc.) in this way, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com