Perimeter intrusion detection method
An intrusion detection and perimeter technology, applied in neural learning methods, biological neural network models, probabilistic networks, etc., can solve the problem of high false alarm rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
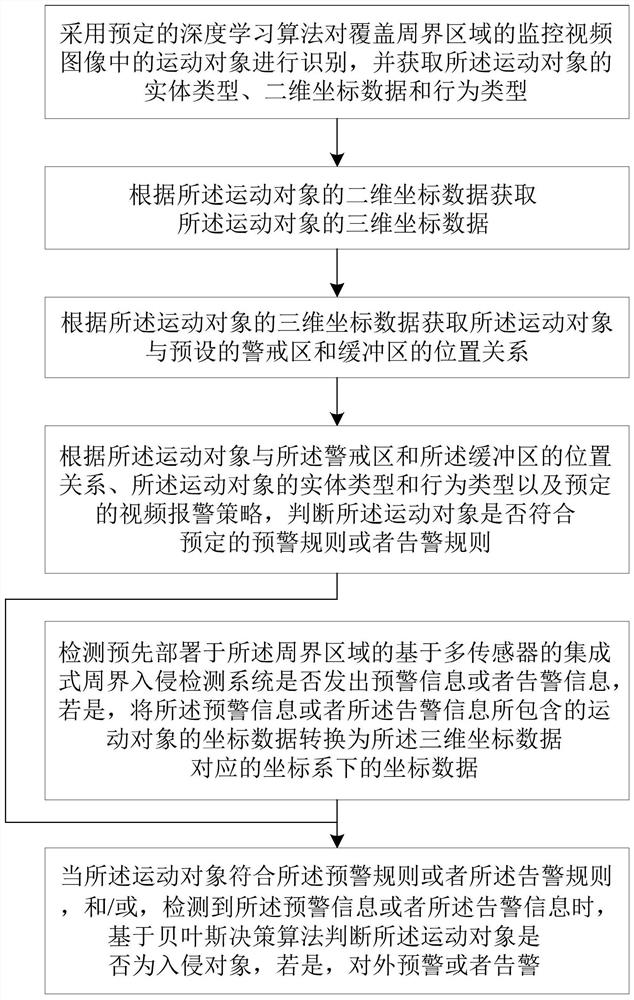
[0047] Example: figure 1 A flow chart showing the implementation of the perimeter intrusion detection method according to the embodiment of the present invention is shown.
[0048] refer to figure 1 , the perimeter intrusion detection method of the embodiment of the present invention includes the following steps:
[0049] Using a predetermined deep learning algorithm to identify the moving object in the surveillance video image covering the perimeter area, and acquire the entity type, two-dimensional coordinate data and behavior type of the moving object;
[0050] Acquiring three-dimensional coordinate data of the moving object according to the two-dimensional coordinate data of the moving object;
[0051] Acquiring the positional relationship between the moving object and the preset warning zone and buffer zone according to the three-dimensional coordinate data of the moving object;
[0052] According to the positional relationship between the moving object, the warning area...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com