Computational ghost imaging image encryption method based on chaotic mapping and DNA coding
A technology of chaotic mapping and encryption method, which is applied to secure communication, image communication, and key distribution through chaotic signals, which can solve problems such as system security defects and large amount of key data, so as to increase the system key space and improve reconstruction quality, the effect of making up for the linearity vulnerability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] The present invention will be further described below in conjunction with the accompanying drawings, and a specific implementation example of the present invention will be described.
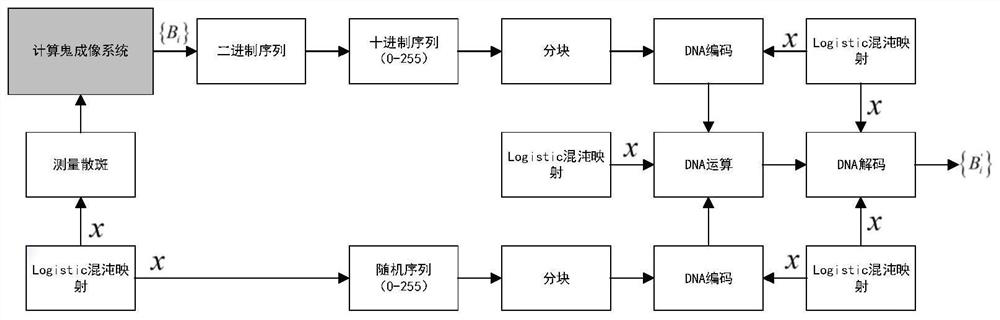
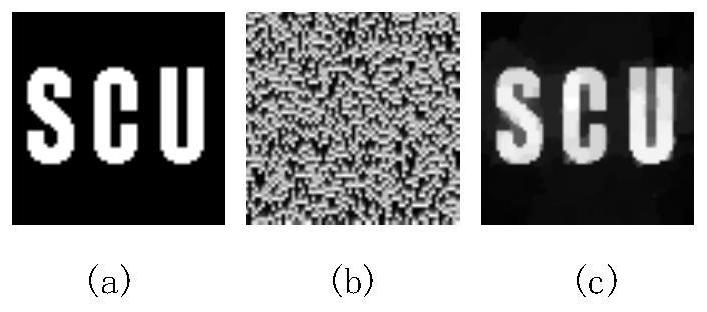
[0052] In this example, a binary image with a size of 64×64 is used as the original target image, such as image 3 As shown in (a), the encryption result is obtained through the computational ghost imaging image encryption system based on chaotic mapping and DNA coding, namely figure 2 {B' in i}.
[0053] The entire encryption process can be implemented as follows:
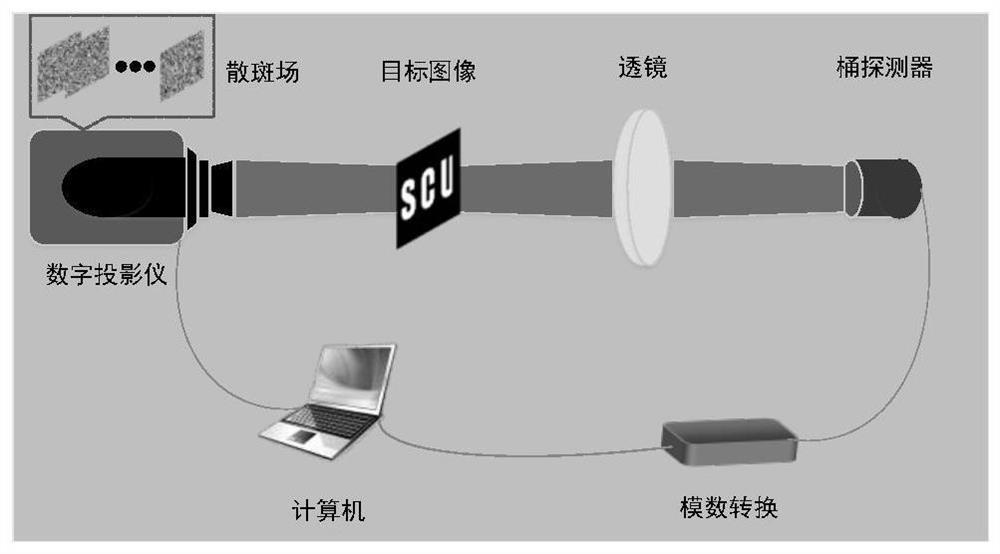
[0054] (1) Pass the target image through figure 1 The shown computational ghost imaging system is encrypted to obtain a series of decimal real numbers {B i}. Among them, the measured speckle of the computational ghost imaging encryption system is generated by the Logistics chaotic map, such as image 3 As shown in (b), the system parameters and initial values of the Logistic chaotic map are 3.9999 and 0.3196, respect...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com