An ontology dependency closure set generation method and device based on privacy degree association, equipment and a storage medium
A privacy and ontology technology, applied in the field of information processing, can solve the problems of hierarchical data dependence on structure description, without considering semantic dependence, etc., to avoid the inefficiency of path description and query, and to achieve the effect of high information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
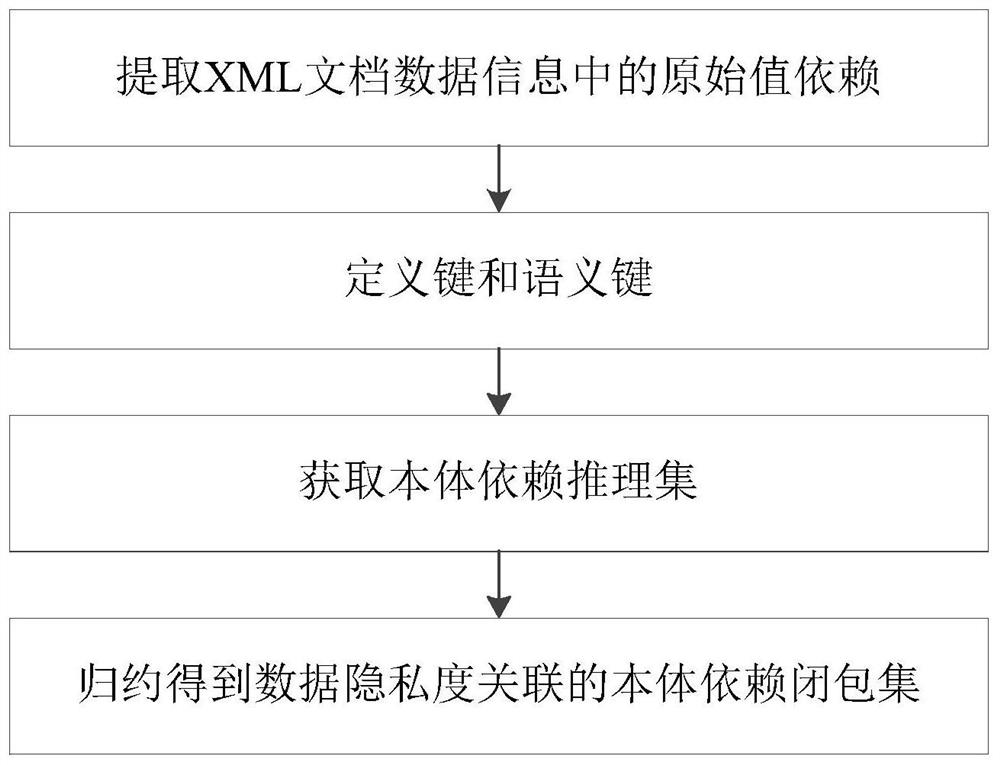
[0031] Taking school course selection as an example, such as figure 1 As shown, a method for generating ontology-dependent closure sets based on privacy-related associations is provided, including the following steps:
[0032] Step 1. Use the DTD abstract syntax tree structured model to extract the original value dependencies in the XML document data information; specifically: use the DTD abstract syntax tree to describe the XML document, and define value-based XML function dependencies and multi-value dependencies based on the XPath path.
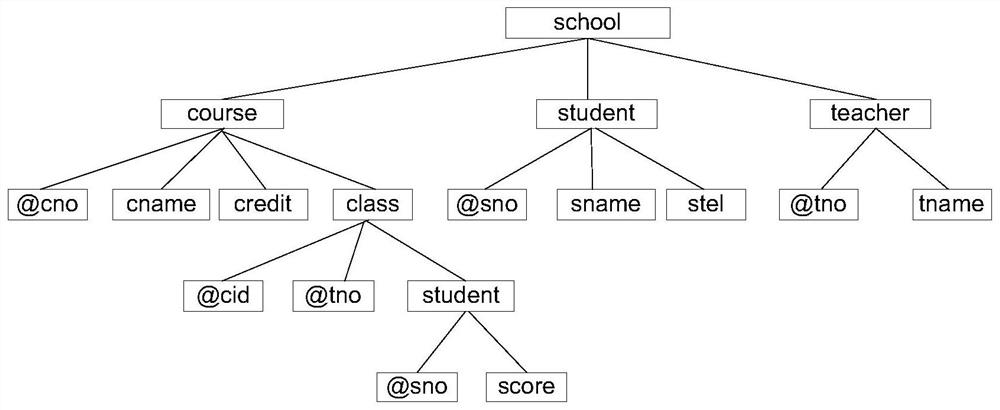
[0033] Such as figure 2 As shown, the functional dependency FD of DTD (Document Type Definition, full name document type definition) can be formalized as:
[0034] A student's student number uniquely identifies a student
[0035] ([school.student.@sno]→school.student)
[0036] A student's student number uniquely identifies a student's name
[0037] ([school.course.student.@sno]→school.course.student.sname)
[0038] The course n...
Embodiment 2
[0114] This embodiment provides a device for generating an ontology-dependent closure set based on privacy degree association, the device comprising:
[0115] Original value dependency acquisition module: use the DTD abstract syntax tree structured model to extract the original value dependency in XML document data information;
[0116] Key and semantic key definition module: define key and semantic key dependently through the original value in XML document data information;
[0117] Ontology dependency reasoning set acquisition module: define semantic dependency and semantic reasoning according to the primary key of the semantic subject in the semantic key, and associate the ontology dependency set formed by the original value dependency set to obtain the ontology dependency reasoning set;
[0118] Ontology dependent closure set acquisition module: take the semantic subject primary key in the semantic key as the equivalence class, divide the ontology dependent inference set a...
Embodiment 3
[0120] This embodiment provides an ontology dependent closure set generation device based on privacy degree association, including a processor and a storage medium;
[0121] The storage medium is used to store instructions;
[0122] The processor is configured to operate according to the instructions to execute the steps of the method according to the embodiment.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com