Efficient certificateless authenticated key agreement method and system without bilinear pairing operation
A technology of authenticated key agreement and bilinear pairing, which is applied in the field of authenticated key agreement to achieve the effect of improving anti-jamming attack, improving reliability, and low overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
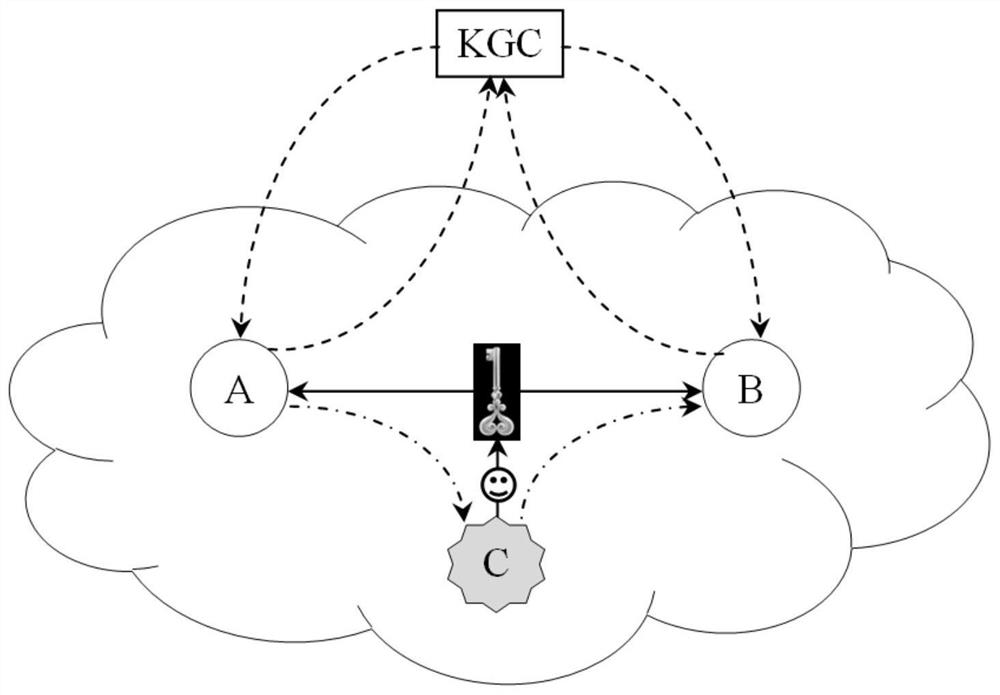
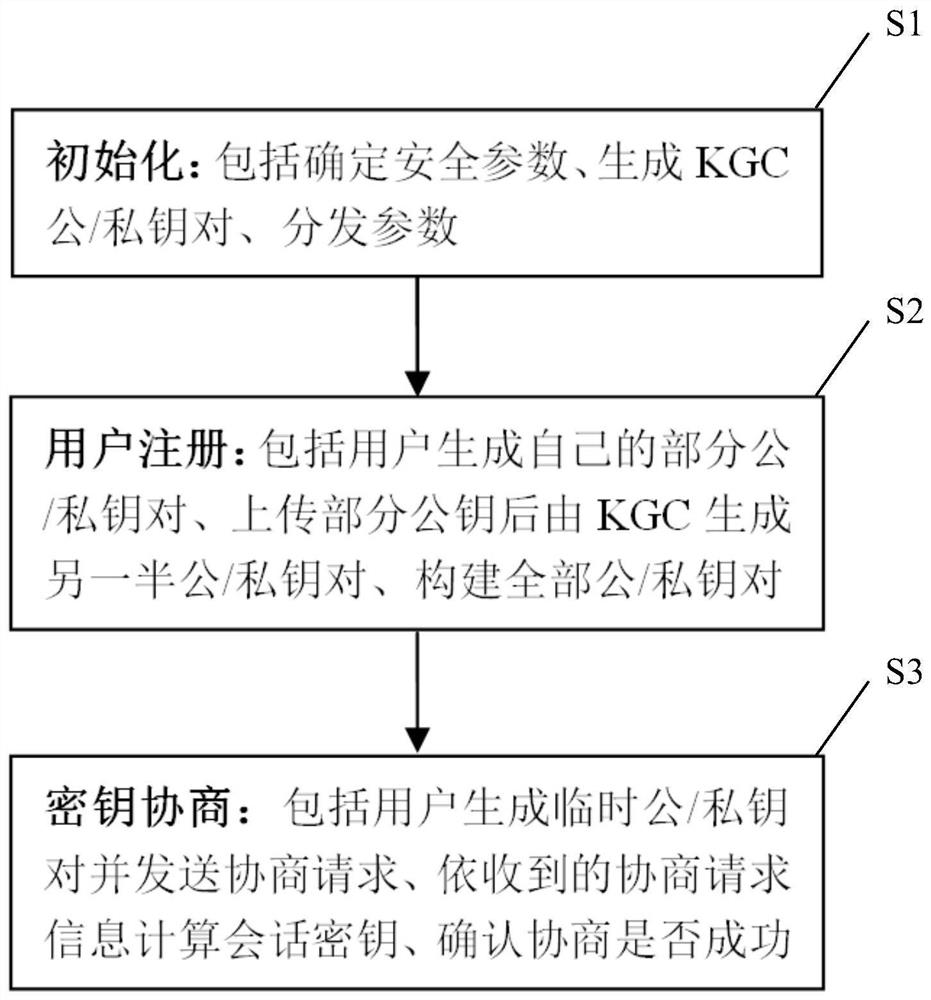
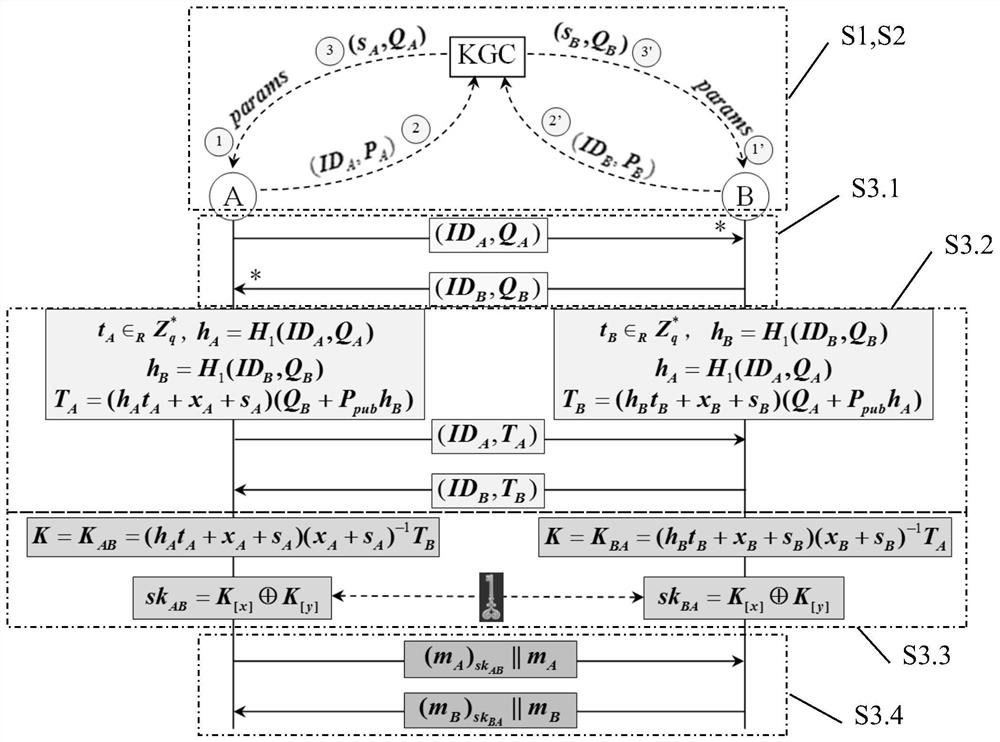
[0055] The present invention is mainly based on the non-certificate authentication / self-authentication public key mechanism, and proposes a session key negotiation method for realizing two-party authentication based on difficult problems. This method fully considers the perfect forward security, prevents counterfeiting attacks, KCI attacks, replay attacks and other problems in the negotiation process, and uses the symmetric key confirmation stage after negotiation to ensure the reliability of the negotiation. Compared with previous schemes, the negotiation of the session key authenticated by the present invention is safer and more reliable, and the negotiation process is more efficient.
[0056] Firstly, the technical terms involved in this embodiment are defined as follows:
[0057] User: a legal session entity, the participant of a session in the network, or the message sender / receiver of a communication, which may be a process, a computer, a mobile terminal or a sensor node...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com