Java code obfuscation method and system, computer equipment and storage medium
A code obfuscation and computer program technology, applied in the computer field, to achieve high configurability, security, and enhanced security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
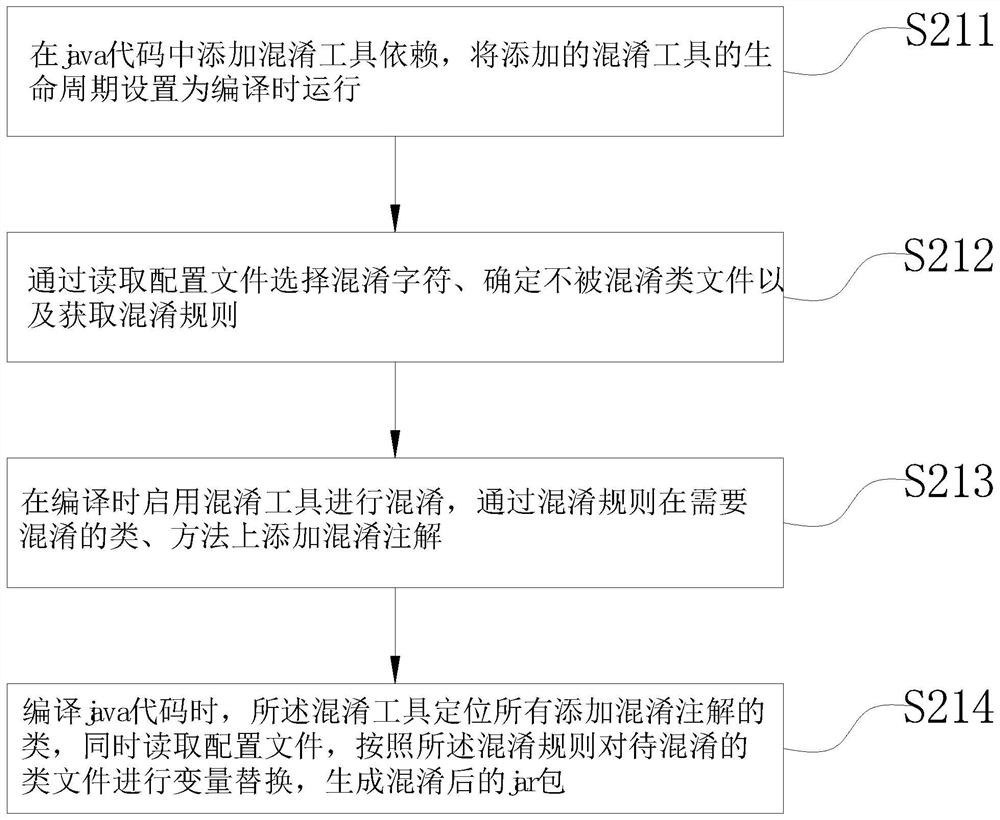
[0039] The present embodiment provides a method for obfuscating java code, which is applied to obfuscate the compiled jar package and the java code in the compilation process, and the method includes the following steps:
[0040] Step 1. Obtain the file to be obfuscated.
[0041] In this embodiment, the file to be confused is a jar package or java code in the compilation stage.
[0042] Step 2, judging the type of the file to be obfuscated, obfuscating the file to be obfuscated, and generating an obfuscated jar package.
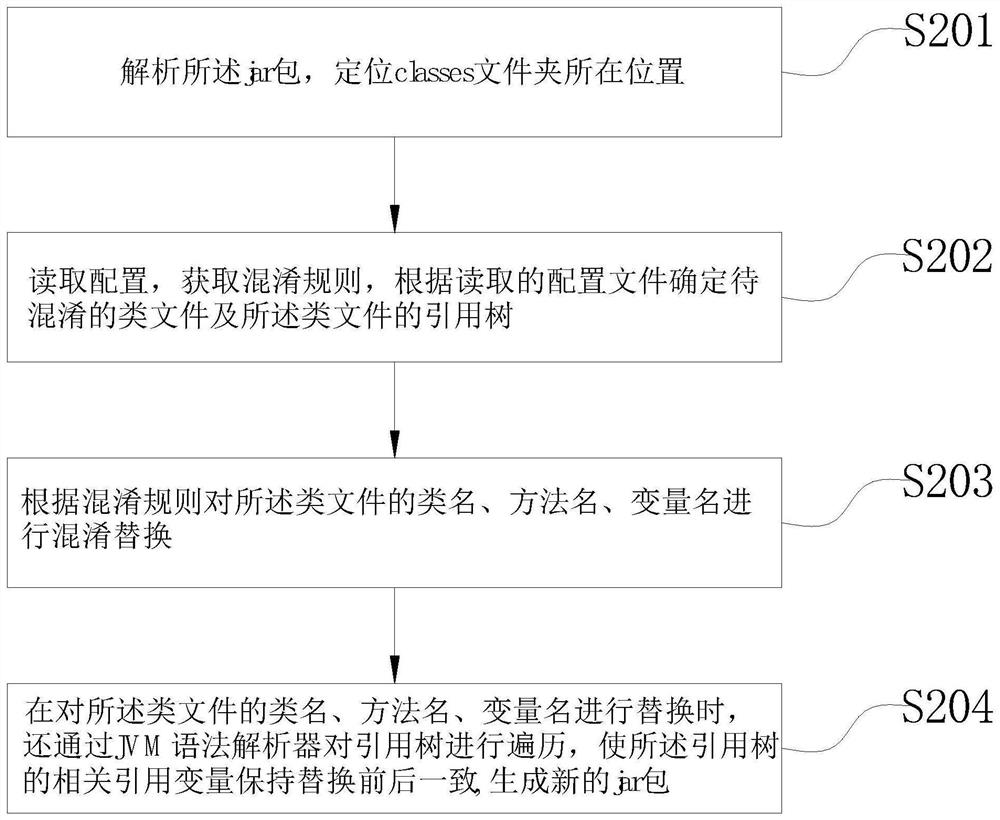
[0043] figure 1 It is a flowchart of jar package obfuscation and encryption in the java code obfuscation method according to an embodiment of the present invention. Such as figure 1 As shown, when the file to be obfuscated is a jar package, the jar package obfuscation encryption method includes:
[0044]S201, parsing the jar package, and locating the location of the classes folder;
[0045] S202. Read the configuration, obtain obfuscation rules, and dete...
Embodiment 2
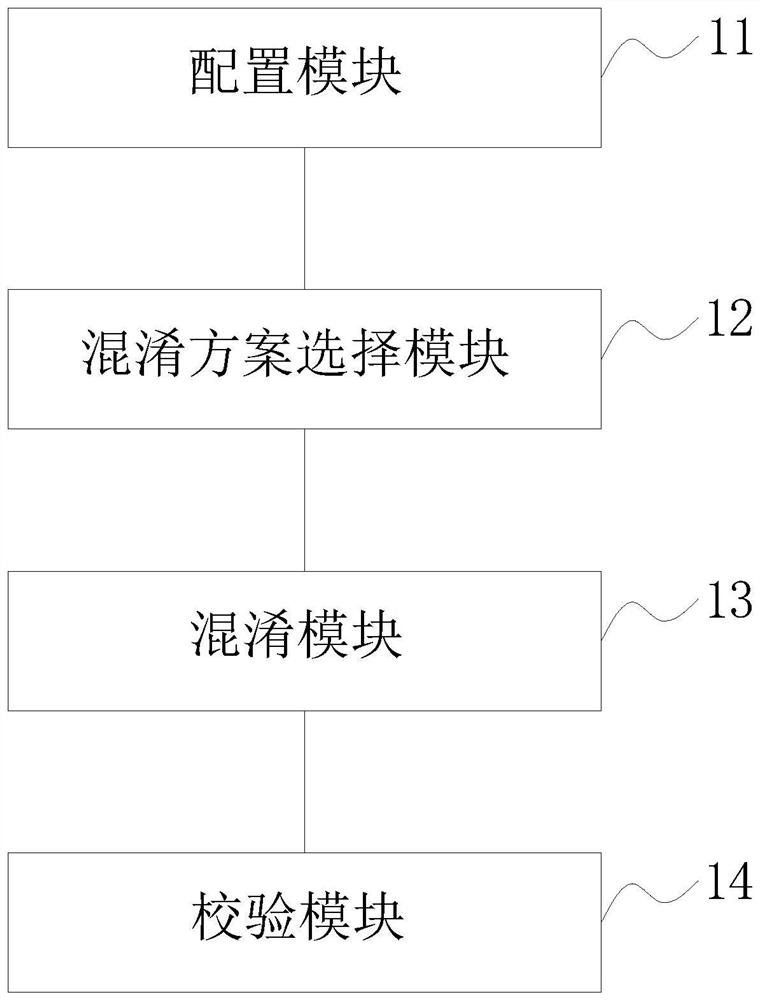
[0058] Such as image 3 As shown, a kind of java code obfuscation system is provided in the present embodiment, the java code obfuscation system adopts the aforementioned java code obfuscation method to obfuscate the jar package after code compilation and the java code in the compiling process; the java code obfuscation The system includes a configuration module 11 , an obfuscation scheme selection module 12 , an obfuscation module 13 and a verification module 14 .
[0059] In this embodiment, the configuration module 11 is configured to read a configuration file, which includes configured character pair classes, methods, and fields. The obfuscation scheme selection module 12 is used to select obfuscated characters, determine non-obfuscated files and obtain obfuscation rules according to the read configuration file.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com