A dynamic encryption and decryption-based Android application reinforcing method
A technology for application programs and encrypted data, applied in the field of information security, can solve the problems of reducing program operation efficiency, reinforcement is easy to be broken through, compression or encryption is difficult to resist external attacks, etc., and achieves the effect of protecting the encrypted results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
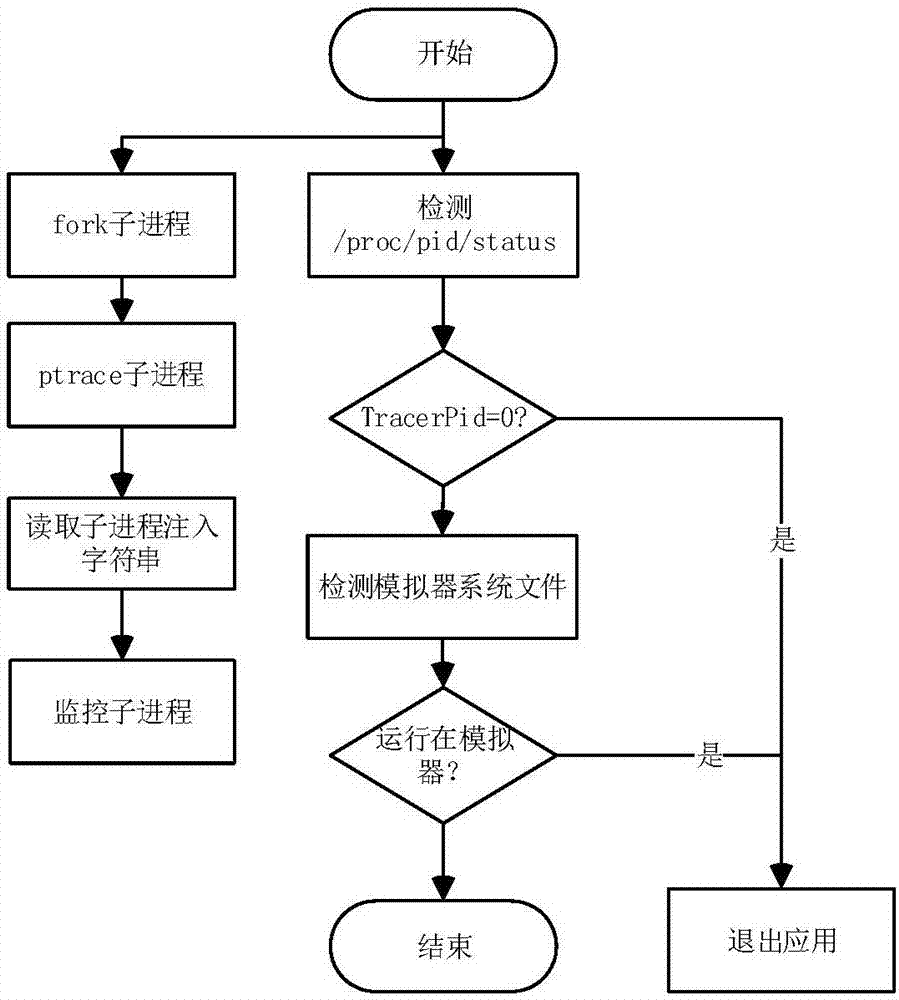
[0022] In order to better illustrate the purpose and advantages of the present invention, the implementation of the method of the present invention will be further described in detail below in conjunction with examples.
[0023] The specific process is:
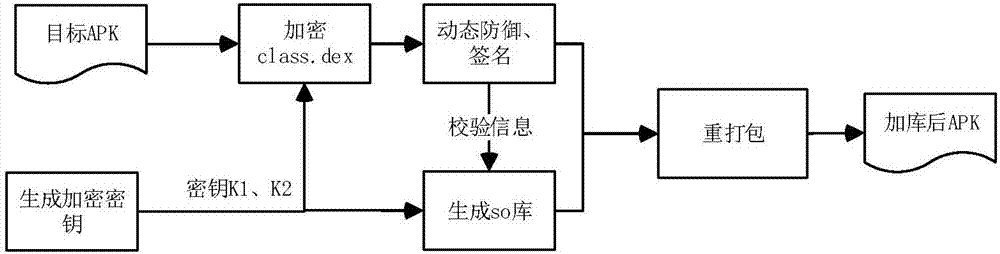
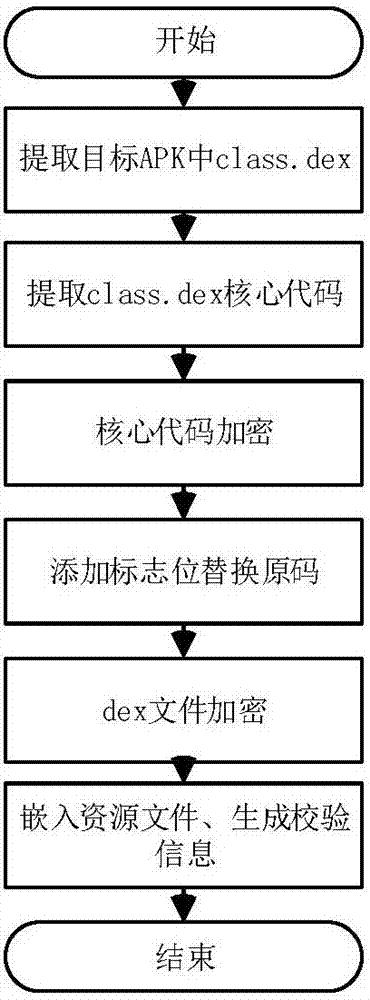
[0024] Step 1, key code encryption.
[0025] Step 1.1, extracting the classes.dex file in the compressed APK file of the Android application.
[0026] Step 1.2, locate the core code. The core code part includes: program Activity, Service life cycle code, program login and other codes involving keys and verification, and program core algorithm code. Extract each section of core code separately.
[0027] Step 1.3, use the key K1 to perform AES encryption on each key code.
[0028] In step 1.4, add the start and end identification bits to each encrypted code, replace the original code, and recalculate the length and check value of the dex file.
[0029] Step 2, dex file encryption.
[0030] Step 2.1, use the key K2 to encry...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com