Semi-supervised SQL (Structured Query Language) injection attack detection method based on few abnormal tags
A technology for injecting attack and detection methods, applied in the field of information security, can solve problems such as detection performance degradation, achieve stable detection performance, meet the needs of actual scenarios, and enhance model detection capabilities and generalization capabilities.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
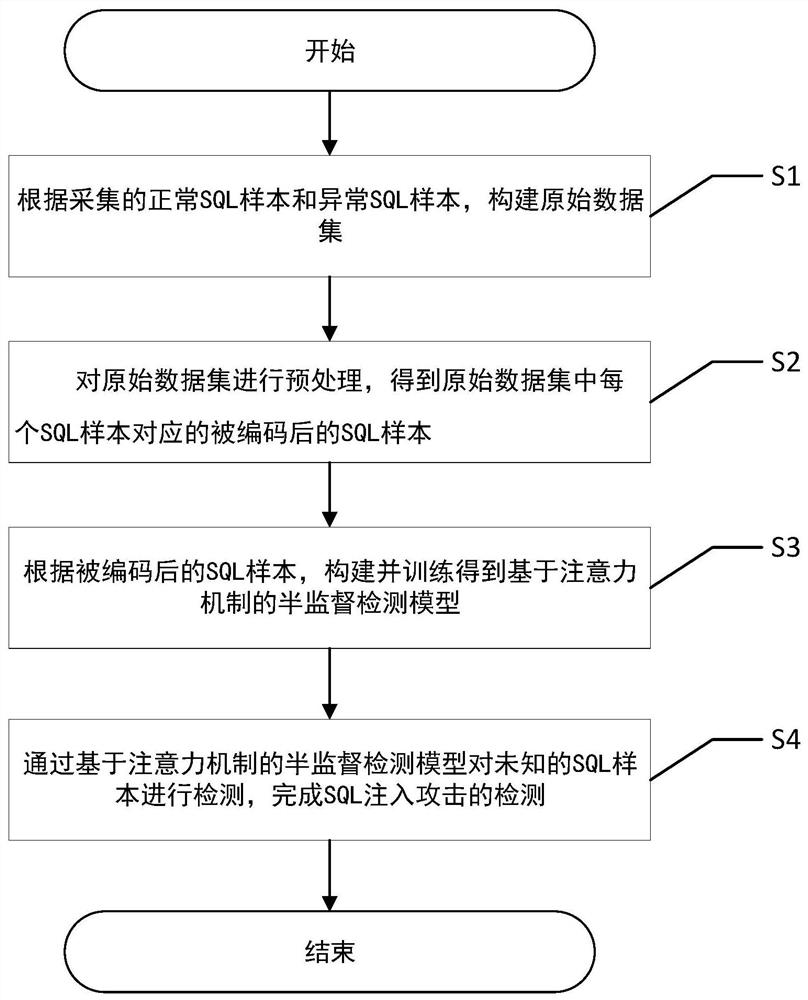
[0067] Such as figure 1 As shown, a semi-supervised SQL injection attack detection method based on a small number of abnormal labels includes the following steps:
[0068] S1. Construct an original data set according to collected normal SQL samples and abnormal SQL samples;
[0069] S2. Preprocessing the original data set to obtain an encoded SQL sample corresponding to each SQL sample in the original data set;
[0070] S3. According to the encoded SQL sample, construct and train a semi-supervised detection model based on the attention mechanism;
[0071] S4. The unknown SQL sample is detected through the semi-supervised detection model based on the attention mechanism, and the detection of the SQL injection attack is completed.
[0072] In this embodiment, in order to solve the problems that the traditional SQL injection attack detection framework adopts syntax analysis, word embedding code may hide key features of SQL injection and introduce noise, etc., the present invent...
Embodiment 2
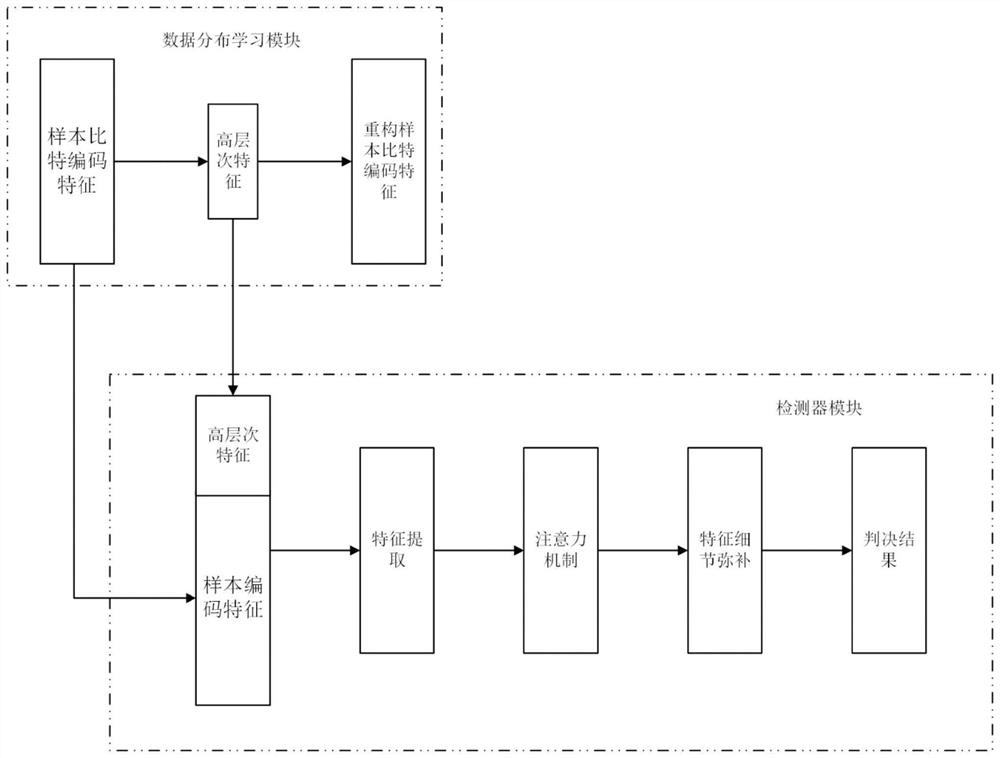
[0087] The attention mechanism-based semi-supervised detection model generated in step S3 of Embodiment 1 includes a data distribution learning module and a detector module connected to each other.
[0088] In this example, if figure 2 As shown, the data distribution learning module uses a model based on data distribution learning to provide the detector module with high-level features such as the central tendency and degree of dispersion of sample features; and the detector module fuses the high-level features and sample encoding features provided by the data distribution learning module As an input, the feature extraction sub-module and the attention sub-module are used to effectively extract and focus on the features, and then judge whether the SQL sample contains SQL injection attacks.
[0089] In this embodiment, the data distribution learning module is implemented using the auxiliary deep generative model proposed in "Auxiliary deep generative models", which enhances th...
Embodiment 3
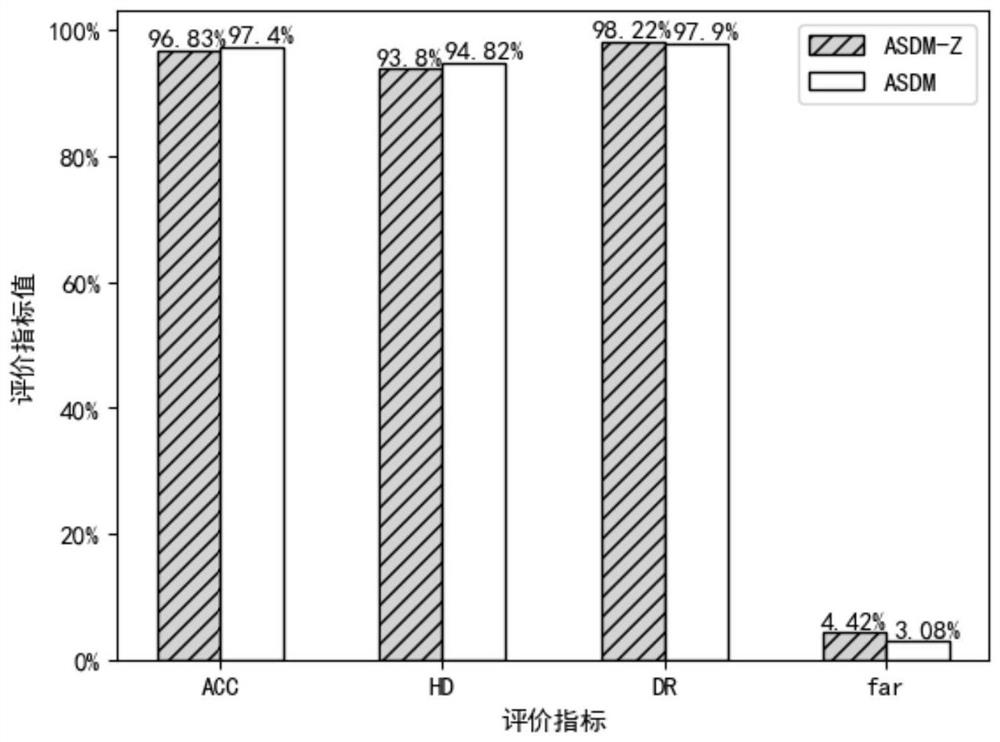
[0121] For the semi-supervised detection model based on the attention mechanism in Example 2, the experimental results of the ablation experiment are used.
[0122] The detection effect of the model is improved by introducing high-level information such as the central trend of the sample feature, the degree of dispersion, and the attention sub-module. In order to verify the influence of the two factors on the performance of the model, ablation experiments are carried out.
[0123] In order to evaluate the influence of introducing sample feature central tendency and discrete degree information on model performance, the method of the present invention is compared with the influence of introducing sample feature posterior distribution information on model performance. Experimental results such as image 3 As shown, ASDM is the method of the present invention, and ASDM-Z is the method of introducing the posterior distribution of sample features; using high-level features such as t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com