Embedded device safe starting scheme design method based on formalized verification
A formal verification, embedded device technology, applied in the formal field, can solve problems such as system security threats, primary stage, ignore logic defects, etc., to achieve the effect of solving threats and fast threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
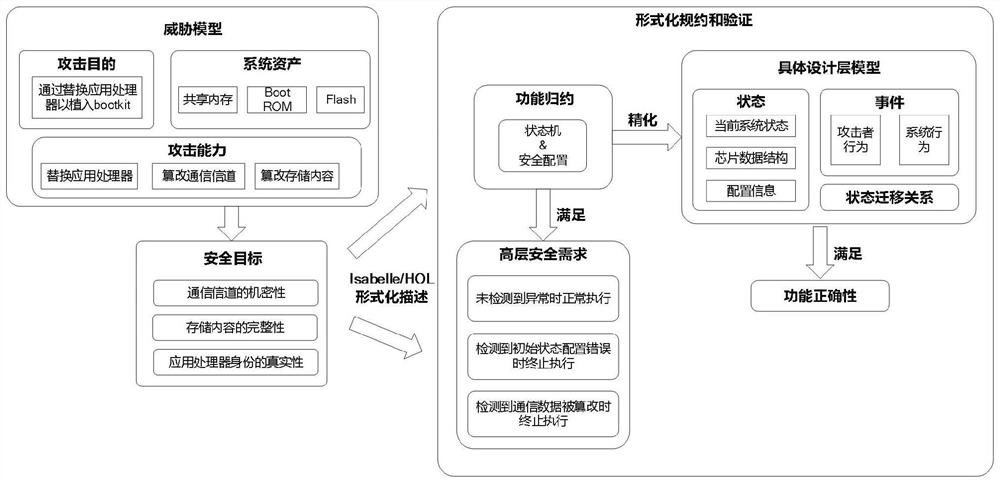
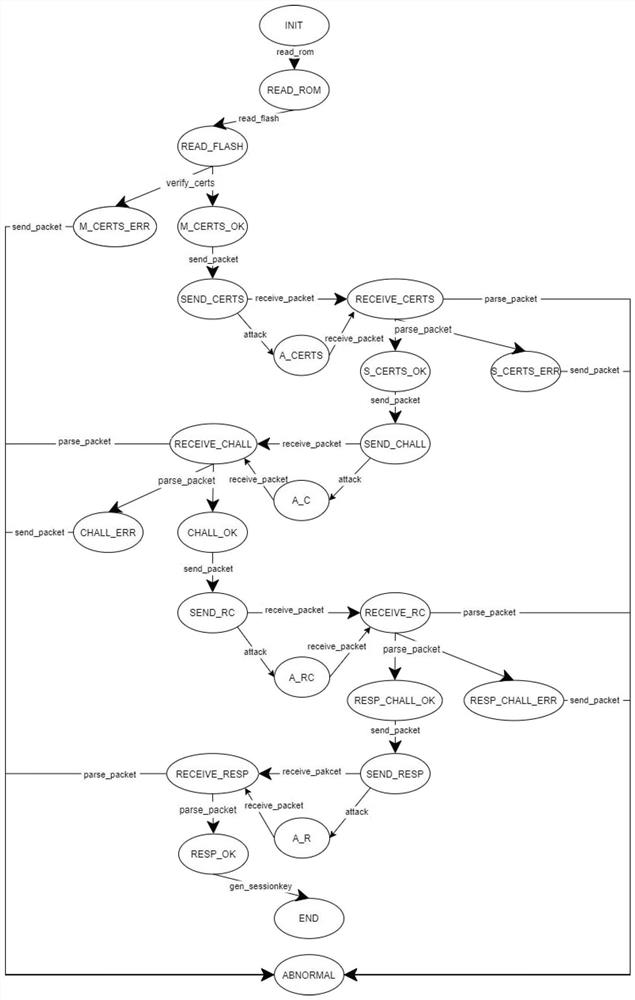
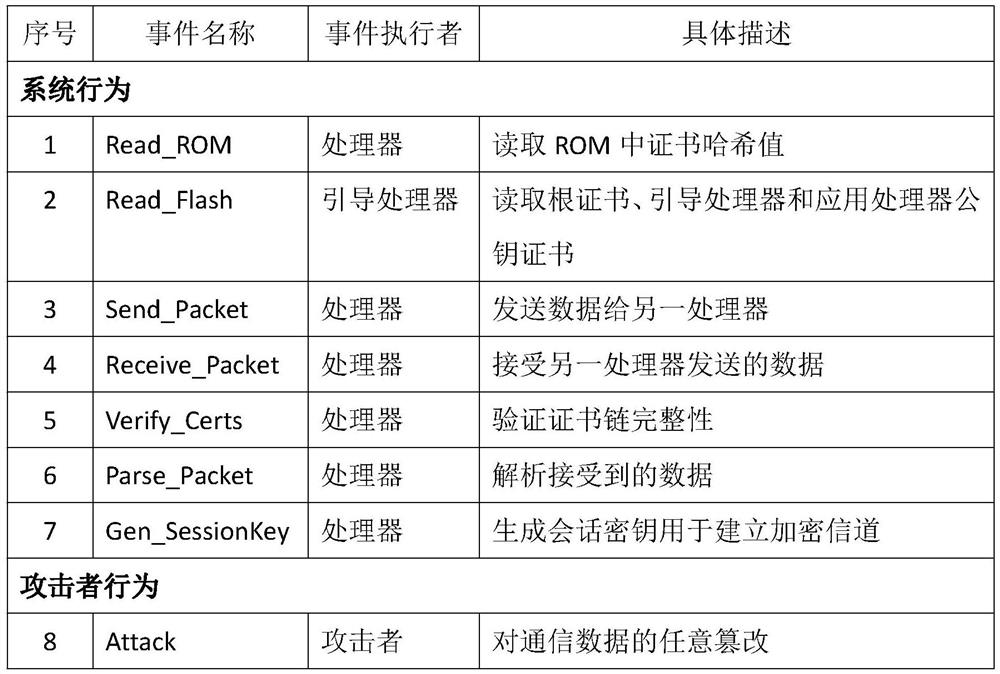
[0029] The invention discloses a method for designing a safe startup scheme of an embedded device based on formal verification. Symmetric multiprocessing (SMP) is a computer architecture in which multiple cores in a single processor have a single shared memory space. In a device with this architecture, the bootstrap process is completed by the bootstrap processor, and other processors are used as application processors (Application Processor), which are in a dormant state during the boot phase, and wait for the bootstrap processor to complete the secure boot process Then wake up the application processor. In order to make the purpose and effect of the present invention clearer, the design process of the identity authentication scheme for the application processor during the startup process of the SMP system equipment will be taken as an example, and the specific implementation of the present invention will be described in detail according to the accompanying drawings and prefe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com