Hardware resource embezzlement detection method and device, storage medium and equipment
A technology of hardware resources and detection methods, applied in the protection of internal/peripheral computer components, etc., can solve the problems of inability to detect abnormal embezzlement of hardware resources, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0027] According to an embodiment of the present invention, an embodiment of a method for detecting embezzlement of hardware resources is provided. It should be noted that the steps shown in the flowcharts of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions, Also, although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
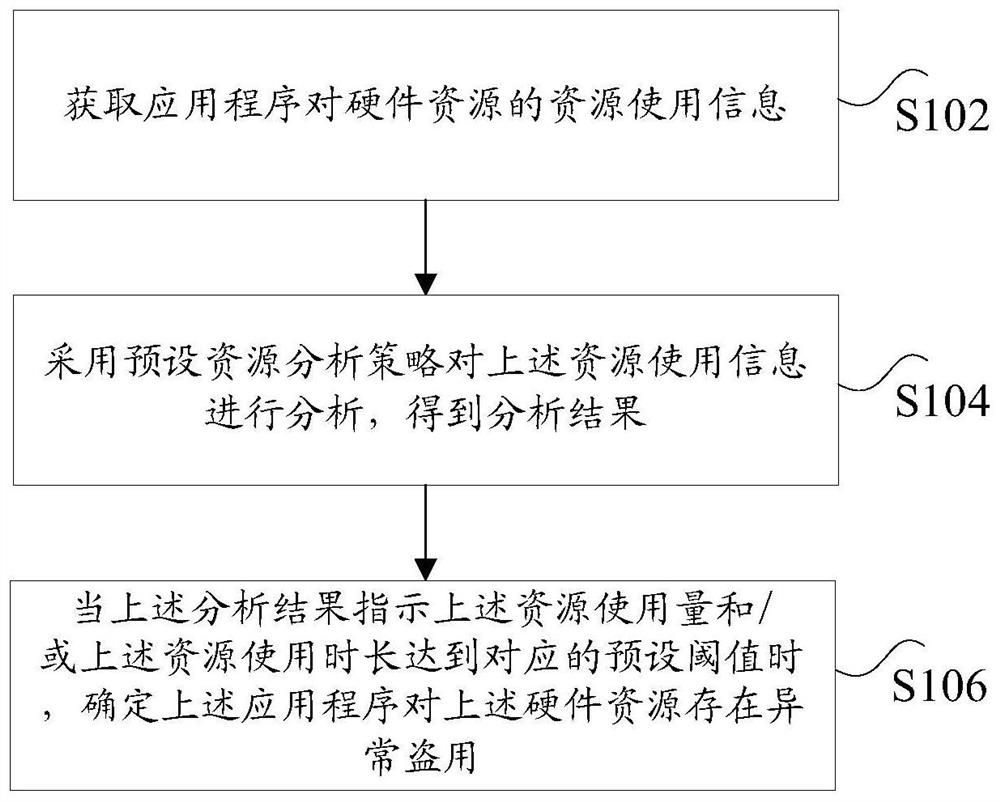
[0028] figure 1 is a flow chart of a method for detecting embezzlement of hardware resources according to an embodiment of the present invention, such as figure 1 As shown, the method includes the following steps:
[0029] Step S102, acquiring the resource usage information of the hardware resource by the application program, wherein the resource usage information includes: resource usage amount and resource usage duration;
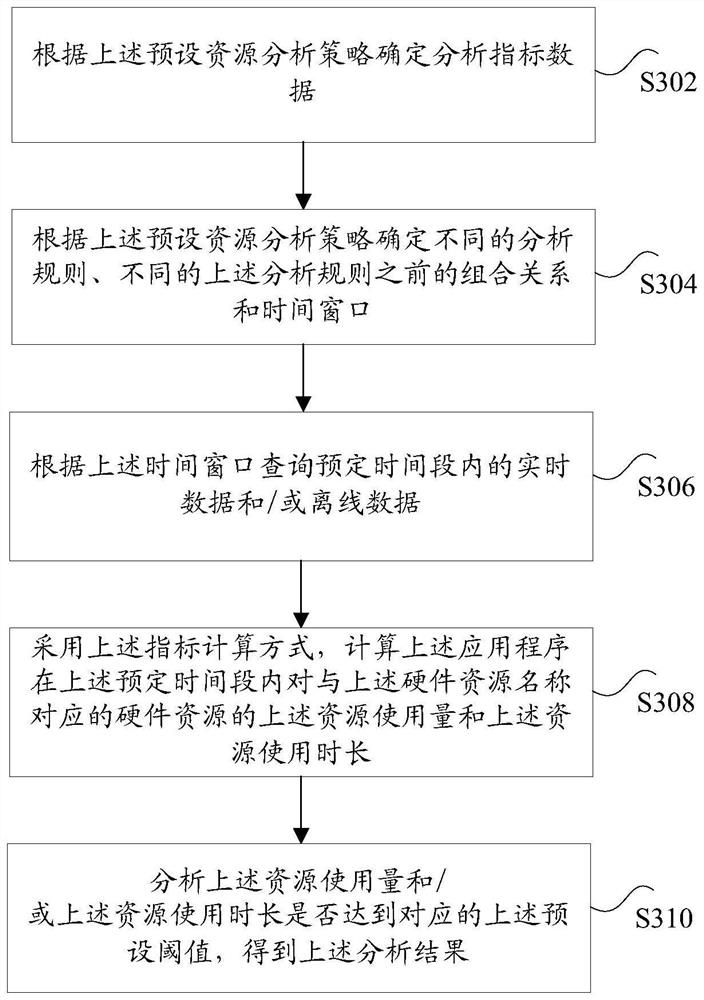
[0030] Step S104, using a preset resource analysis strat...
Embodiment 2
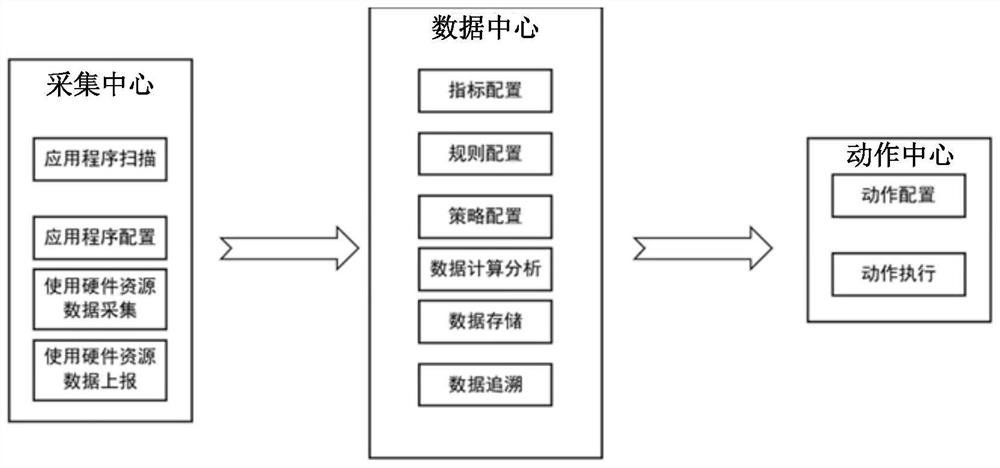
[0067] According to an embodiment of the present invention, an embodiment of a device for implementing the above method for detecting embezzlement of hardware resources is also provided, Figure 4 is a schematic structural diagram of a device for detecting embezzlement of hardware resources according to an embodiment of the present invention, as shown in Figure 4 As shown, the above-mentioned device includes: an acquisition module 40, an analysis module 42 and a determination module 44, wherein:
[0068] An acquisition module 40, configured to acquire resource usage information of hardware resources by applications, wherein the resource usage information includes: resource usage and resource usage duration;
[0069] An analysis module 42, configured to analyze the above-mentioned resource usage information by adopting a preset resource analysis strategy, and obtain an analysis result;
[0070] The determining module 44 is configured to determine that the above-mentioned applic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com