Hard disk encryption equipment and encryption use method
A technology of hard disk encryption and data encryption key, which is applied in the directions of digital data authentication, digital data protection, program control devices, etc., can solve the problems of unprotected data, complicated operation, etc. safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
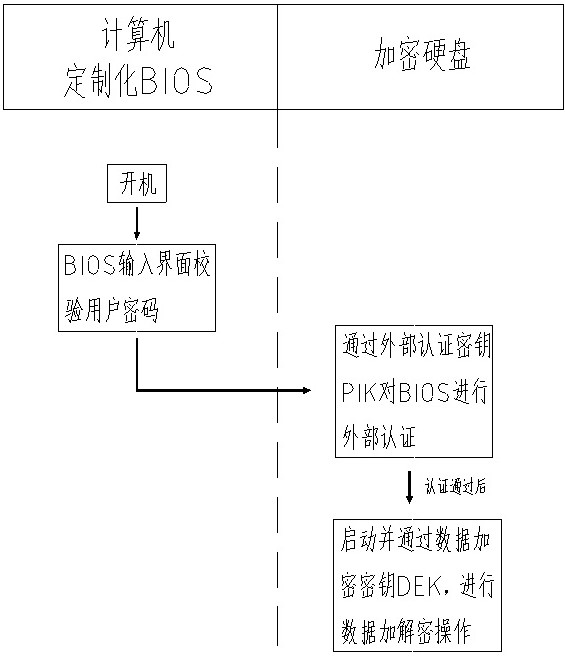
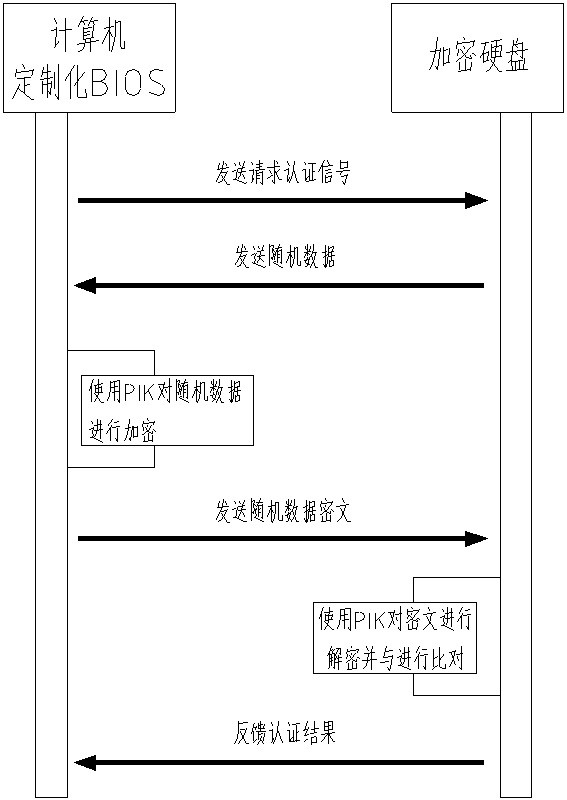
[0011] Example: such as figure 1 , figure 2 As shown, a hard disk encryption device includes an encrypted hard disk and a customized BIOS. The customized BIOS is installed in a computer as software, and the customized BIOS can verify user passwords and passwords on its BIOS input interface after the computer is turned on. It is the power-on password set by the user in the BIOS. This process does not require the participation of the encrypted hard disk; the encrypted hard disk is connected to the connection port of the computer through a data transmission wire, so as to realize data transmission between them, and the encrypted hard disk and the inside of the customized BIOS Two sets of keys are stored, one of which is an external authentication key PIK, and the other is a data encryption key DEK. The external authentication key PIK can compare and authenticate the identity of the encrypted hard disk and the customized BIOS; The data encryption key DEK can encrypt the data in ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com