Method and system for interfering network scanner
A network scanning and operating system technology, applied in the field of network attack and defense, can solve the problem that network scanners cannot forge the type of operating system in a targeted manner
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
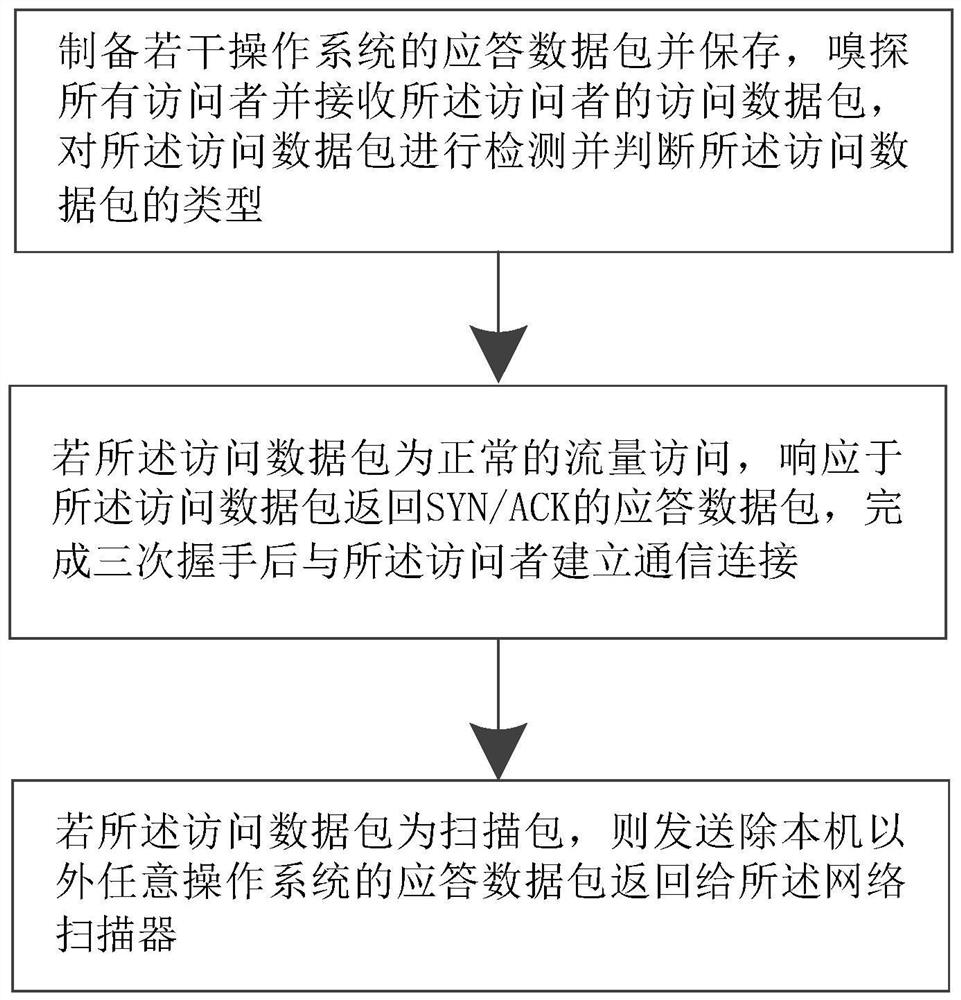
[0040] Such as figure 1 As shown, the present embodiment includes a method for interfering with a network scanner, comprising the following steps: preparing and storing response data packets of several operating systems, sniffing all visitors and receiving access data packets of visitors, and performing an operation on the access data packets Detect and judge the type of access data packets.
[0041] If the access data packet is a normal traffic access, a SYN / ACK response packet is returned in response to the access data packet, and a communication connection is established with the visitor after completing the three-way handshake. If the access data packet is a scan packet, send a response packet of any operating system other than the local machine back to the network scanner.
[0042] Specifically, in normal network services, both the attacker and the normal visitor directly access the service port, and the attacker's network scanner can directly determine the specific info...
Embodiment 2
[0062] This embodiment includes a system for interfering with a network scanner, including: a storage unit, which stores response data packets of several operating systems. The judging unit is configured to sniff all the visitors and receive the access data packets of the visitors, detect the access data packets and judge the type of the access data packets.
[0063] The first communication unit is configured to return a response data packet of SYN / ACK in response to the access data packet, and establish a communication connection with the visitor after completing the three-way handshake. The second communication unit is used to send the response data packet of any operating system except the local machine back to the network scanner.
[0064] For relevant information, please refer to part of the description of Embodiment 1.
Embodiment 3
[0066] An electronic device includes a memory and a processor, the memory is used to store one or more computer instructions, wherein the one or more computer instructions are executed by the processor to implement the above method for interfering with a network scanner.
[0067] Those skilled in the art can clearly understand that for the convenience and brevity of the description, the specific working process of the electronic device described above can refer to the corresponding process in the foregoing method embodiment, which will not be repeated here.
[0068] A computer-readable storage medium. Computer instructions are stored on the computer-readable storage medium. When the computer instructions are executed by a processor, the steps of the method in Embodiment 1 are implemented.
[0069] Those skilled in the art should understand that the embodiments of the present invention may be provided as methods, apparatuses, or computer program products. Accordingly, the prese...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com