Virtual node and honeypot combined trapping attack method, device and system
A technology of virtual nodes and honeypots, which is applied in transmission systems, digital transmission systems, secure communication devices, etc. It can solve the problems of malicious network protocol attacks, random attack behaviors of attackers, and inability to support services, so as to achieve real and trapping of virtual nodes The effective effect of the attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
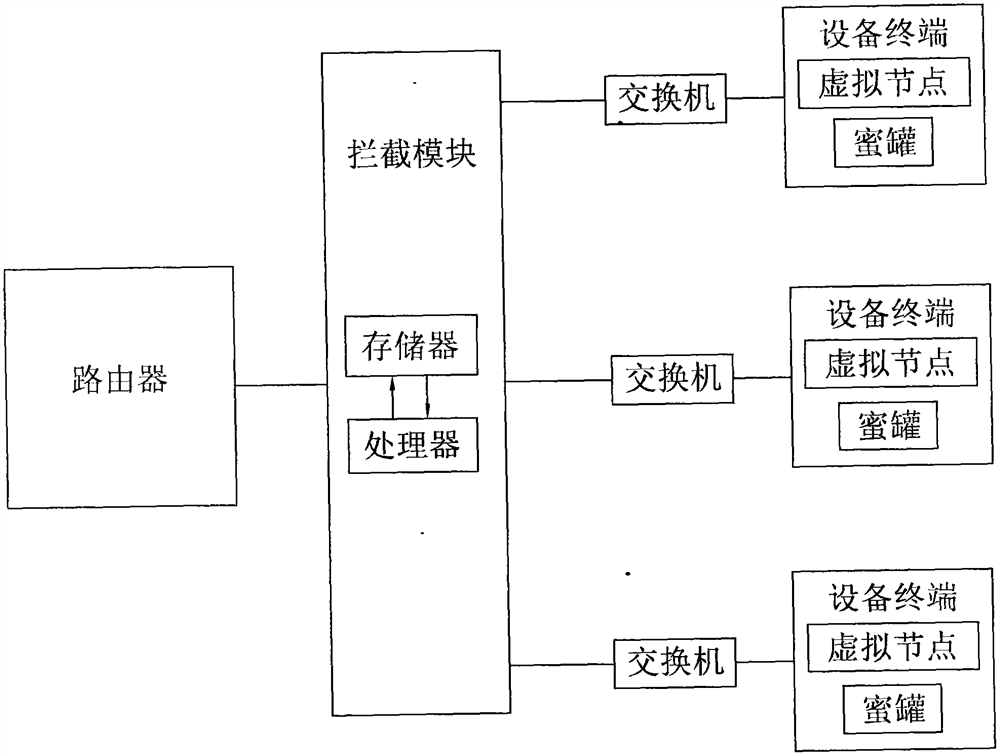
[0059] Reference Figure 1 , a trap attack system combined with a virtual node and honeypot, including: routers, switches, interception modules and multiple device terminals,
[0060] Routers are used to forward packets;
[0061] The switch is connected to the router for forwarding packets;
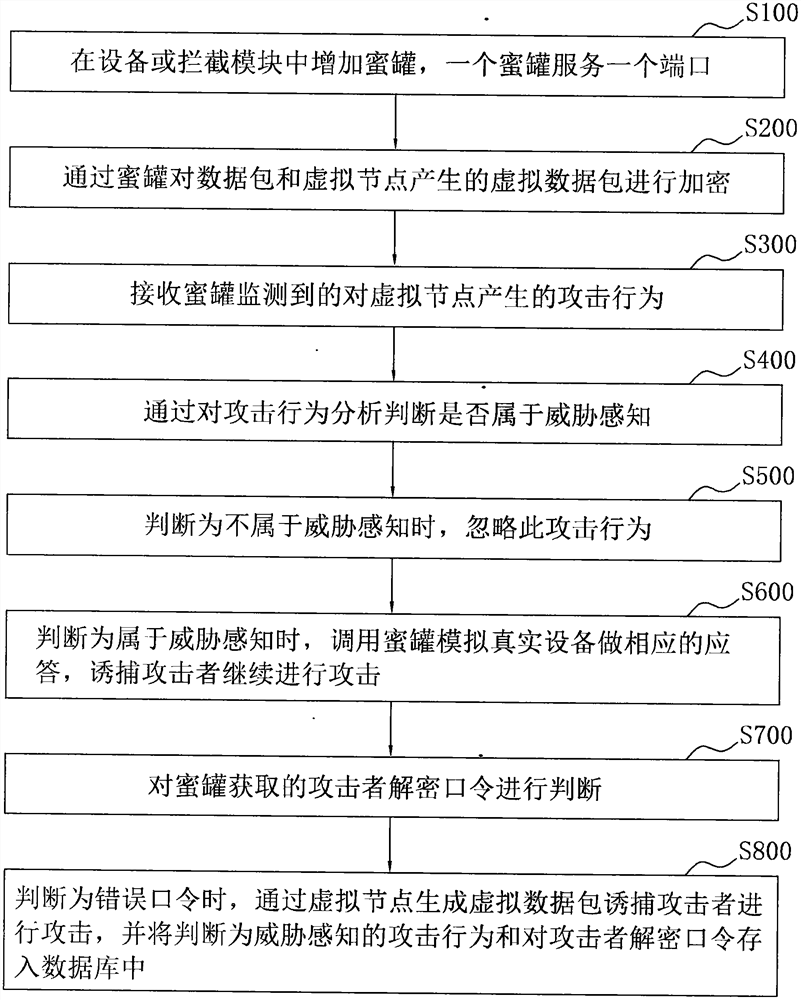
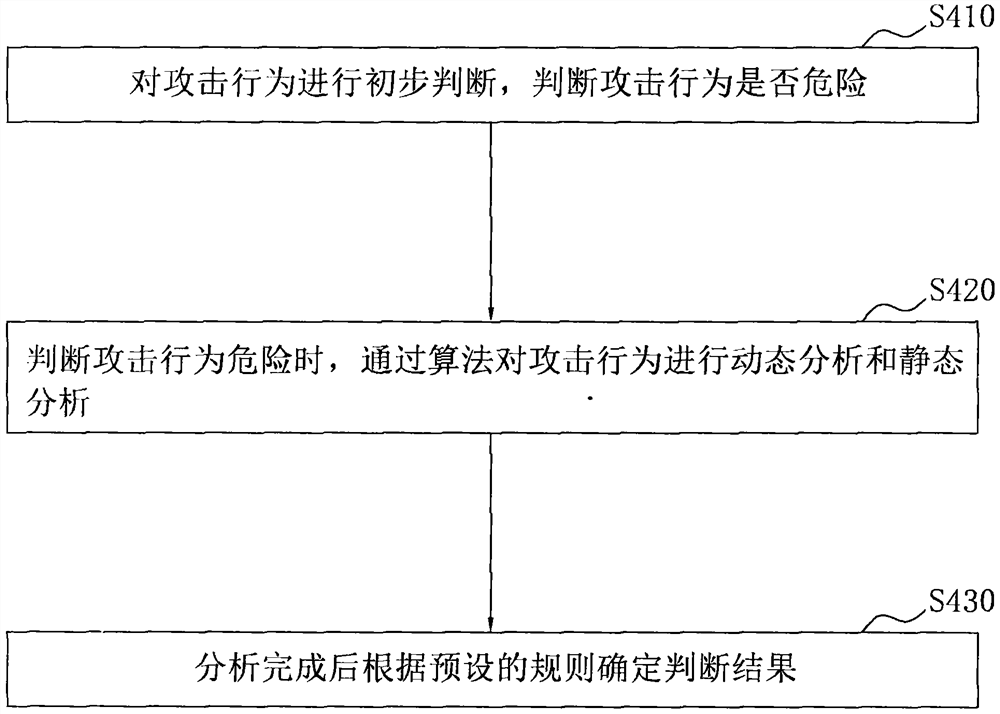
[0062] The interception module, set between the router and the switch, is used to modify the source address of the packets crawled by the interception module, and the source address of the packet is mainly to confuse the real packet with the virtual packet; it is used to judge the attack behavior, as well as the threat perception attack behavior and the decrypted password of the attacker to store. The interception module is set up with a trap attack device combined with a virtual node and a honeypot, including a memory and a processor, and the memory stores the judgment program of the attack behavior, the threat perception attack behavior and the judgment of the attacker's decryption password...
Embodiment 2
[0097] The difference from Example 1 is that the fake node is provided on the interception module, the interception module is provided with a honeypot, the honeypot is used to monitor the attack behavior, and the acquisition of the attacker's decryption password. This situation is more suitable for the setting of virtual nodes on the device terminal, for example, there are many PC ends distributed in different areas, because all device terminals and router connections need to go through the interception module, so all the fake nodes are set in the interception module, which facilitates the construction of the entire virtual network and the deployment of honeypots on the false nodes.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com