Communication link encryption system and encryption method suitable for unmanned aerial vehicle
An encryption system and communication link technology, which is applied in the field of UAV communication control, can solve the problems of time-consuming encryption, inapplicability, and increased link complexity, and achieve the effect of high decryption accuracy and simple link
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
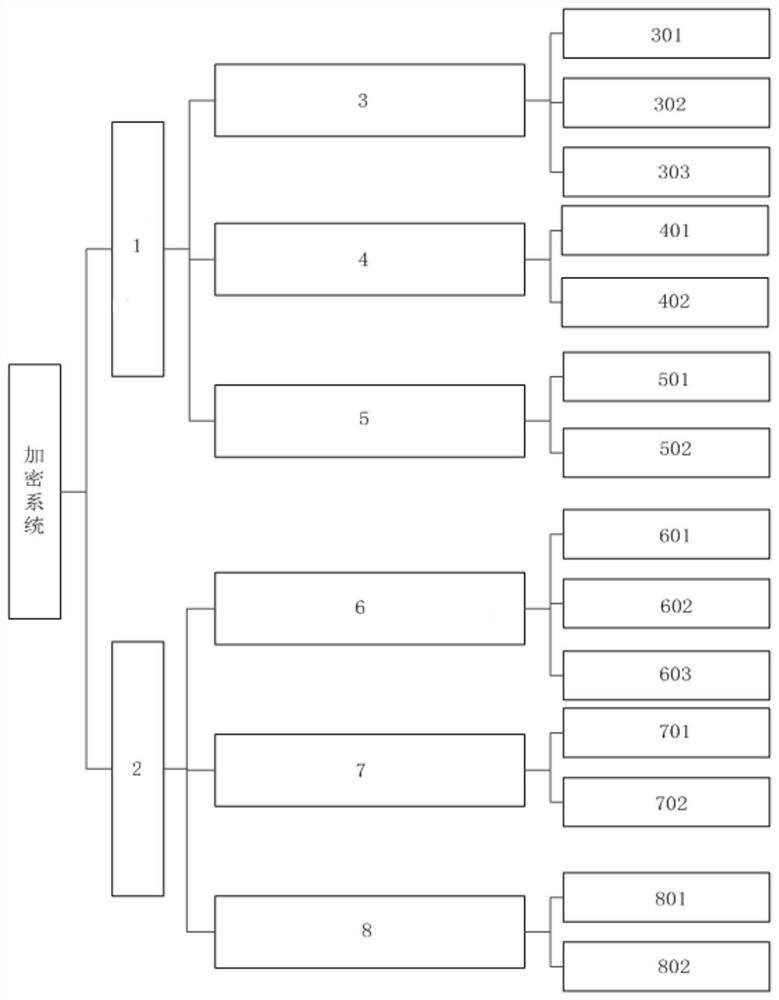
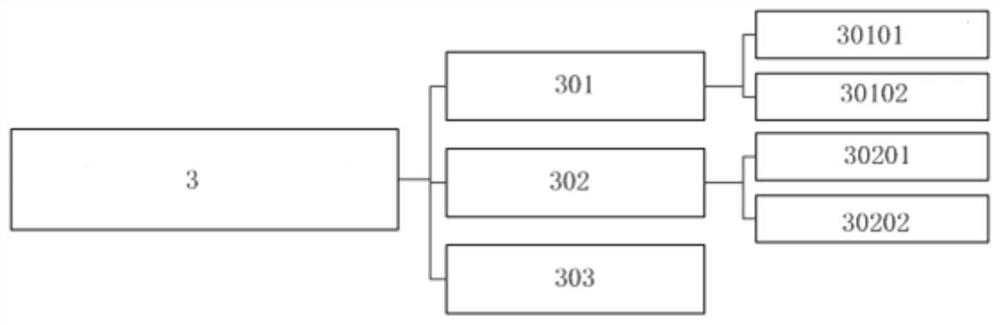
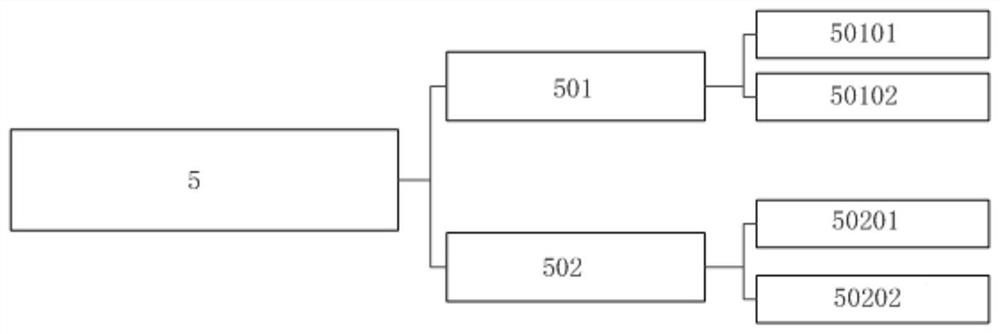
[0077] figure 1 A general block diagram of a communication link encryption system suitable for drones according to an embodiment of the present invention is shown. figure 2 It shows a block diagram of a UAV-side data transmission module of a communication link encryption system suitable for UAVs according to an embodiment of the present invention. image 3 A block diagram of an encryption module at the UAV side of a communication link encryption system suitable for UAVs according to an embodiment of the present invention is shown. Figure 4 A block diagram of a data transmission module at the ground end of a communication link encryption system suitable for unmanned aerial vehicles is shown according to an embodiment of the present invention. Figure 5 It shows a block diagram of a ground-end encryption module of a communication link encryption system suitable for UAVs according to an embodiment of the present invention.
[0078] combine figure 1 , figure 2 , image 3 ,...
Embodiment 2
[0088] Image 6 A flow chart of a communication link encryption method suitable for drones according to an embodiment of the present invention is shown. Figure 7 It shows another flow chart of the communication link encryption method suitable for drones according to an embodiment of the present invention.
[0089] to combine Image 6 with Figure 7 As shown, the communication link encryption method suitable for unmanned aerial vehicles utilizes the above-mentioned communication link encryption system applicable to unmanned aerial vehicles, including:
[0090] Step 1: The UAV-side encryption system and the ground-side device-side encryption system determine the keys, and read the keys connected between the devices in the UAV-side key database and the ground-side key database respectively;
[0091] Step 2: The encryption system of the ground terminal equipment receives the ground terminal plaintext sent by other ground terminal equipment, encrypts the ground terminal plainte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com