Reflection-guided Java deserialization call chain mining method and system
A technology of deserialization and call chaining, which is applied in the direction of program control devices, platform integrity maintenance, and execution examples, etc. It can solve the problems of difficulty in meeting the requirements of call chain mining accuracy and efficiency, large labor costs, and high false alarm rate of call graphs. problem, to achieve the effect of improving test efficiency and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
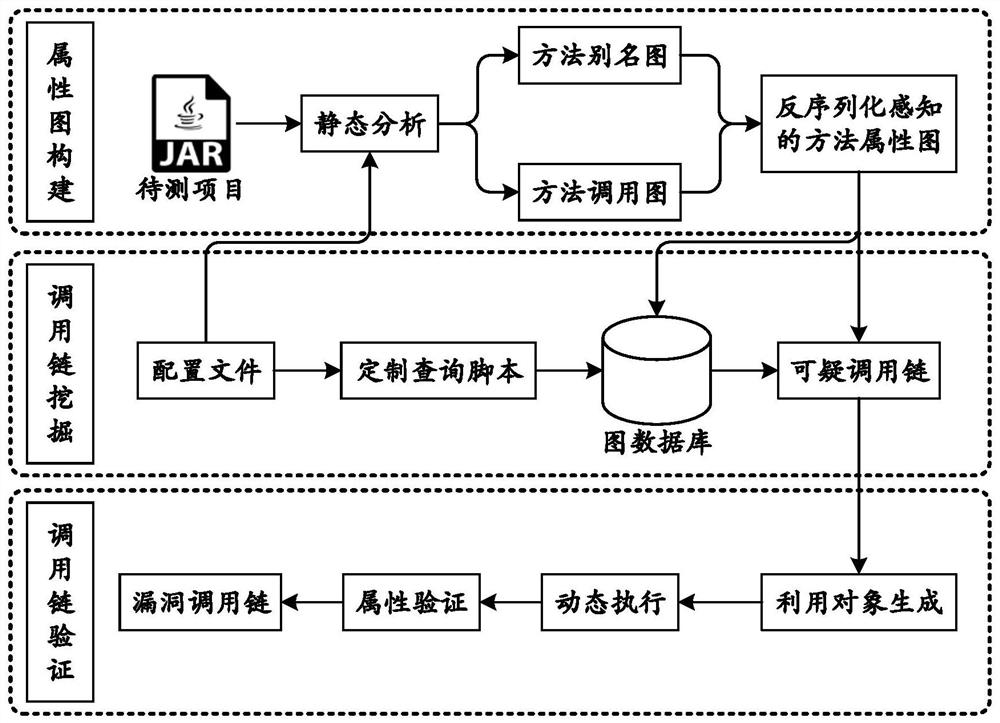
[0041] see figure 1 and figure 2 As shown, a reflection-guided Java deserialization call chain mining method provided by the present invention includes the following steps:
[0042] 1) Perform static analysis on the items to be detected, and build a method attribute graph for deserialization awareness;
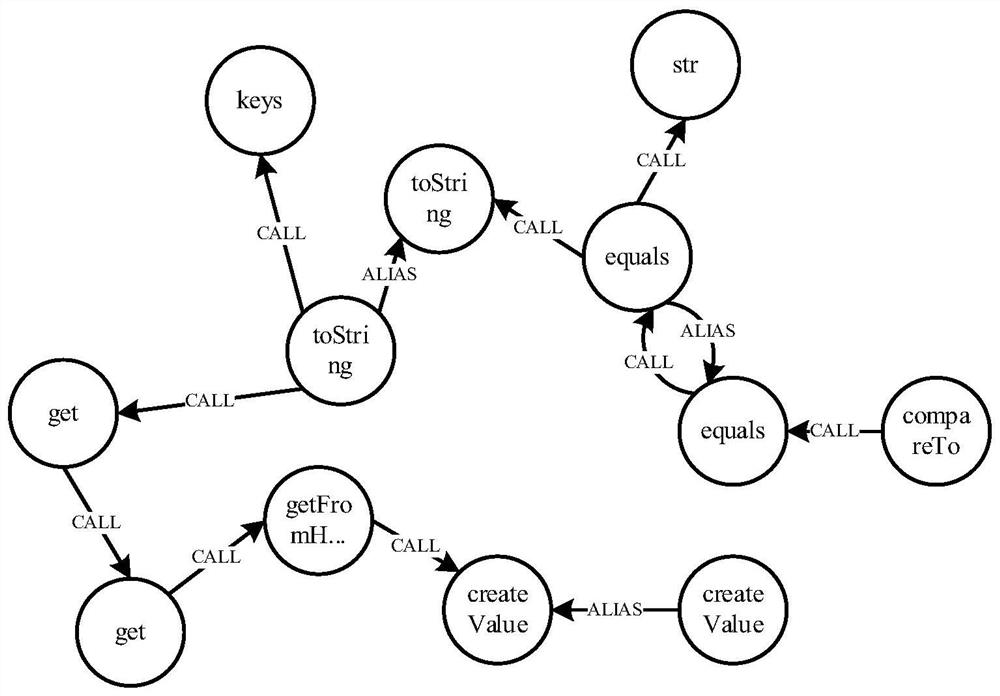
[0043] 1.1) Soot, an analysis tool based on Java static programs, performs pointer analysis and call relationship analysis on the JAR / WAR / CLASS files of the project to be tested, and constructs a method alias graph and a method call graph;
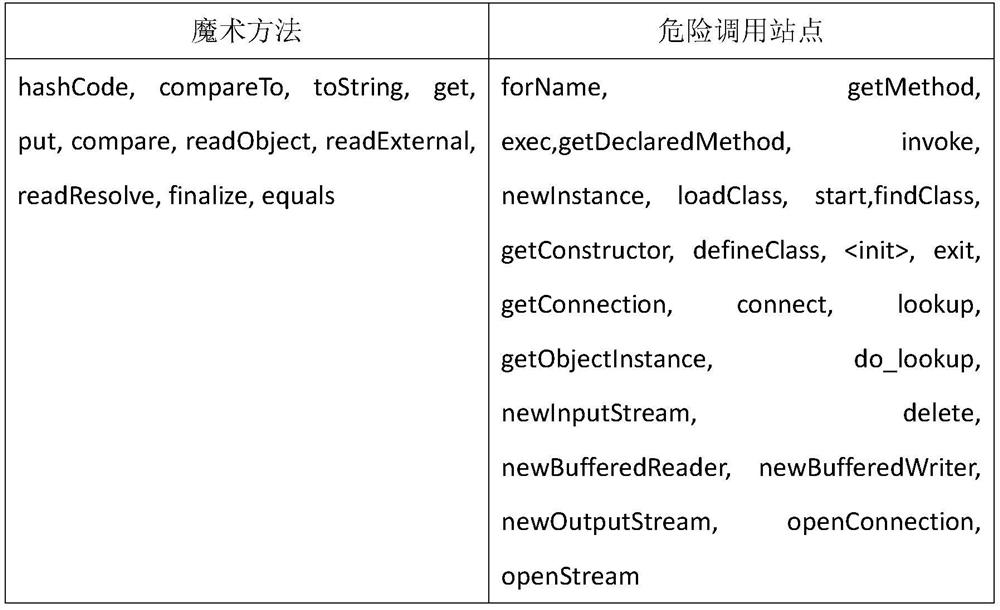
[0044] 1.2) Integrate the method alias graph and method call graph to construct a deserialization-aware method attribute graph, where the nodes in the deserialization-aware method attribute graph represent various methods in the program, and the compareTo node represents the JAR file to be tested The compareTo method used to compare the size of the two attribute values; similarly, the equals node represents the equals method used to jud...
Embodiment 2
[0057] Corresponding to the reflection-guided Java deserialization call chain mining method in Embodiment 1, this embodiment 2 provides a reflection-guided Java deserialization call chain mining system. Please refer to figure 1 and figure 2 As shown, the system includes a property graph building module, a suspicious call chain mining module, and a vulnerability call chain verification module;
[0058] The property graph building module is used to perform static analysis on the item to be detected, and construct a method property graph for deserialization awareness. The property graph building module includes a compilation unit and a representation unit;
[0059] The compilation unit is used for the analysis tool Soot based on Java static programs, to perform pointer analysis and call relationship analysis on the JAR / WAR / CLASS files of the project to be detected, and to construct a method alias graph and a method call graph;
[0060] The representation unit is used to fuse th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com