Data transaction method for personalized privacy protection requirement of terminal equipment
A privacy protection and transaction method technology, which is applied in the field of data transactions oriented to the personalized privacy protection requirements of terminal equipment, can solve the problems of large privacy risks, difficulty in meeting personalized privacy protection requirements, and high communication costs, so as to improve transaction efficiency, Solve the problem of information asymmetry and maximize the effect of accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
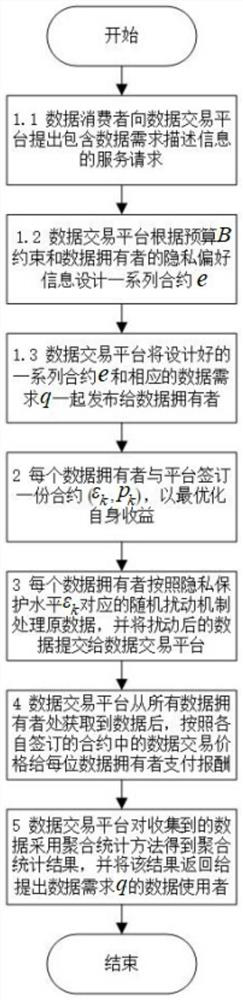
[0027] The present invention will be described in detail below with reference to the accompanying drawings and specific embodiments. This embodiment is implemented on the premise of the technical solution of the present invention, and provides a detailed implementation manner and a specific operation process, but the protection scope of the present invention is not limited to the following embodiments.
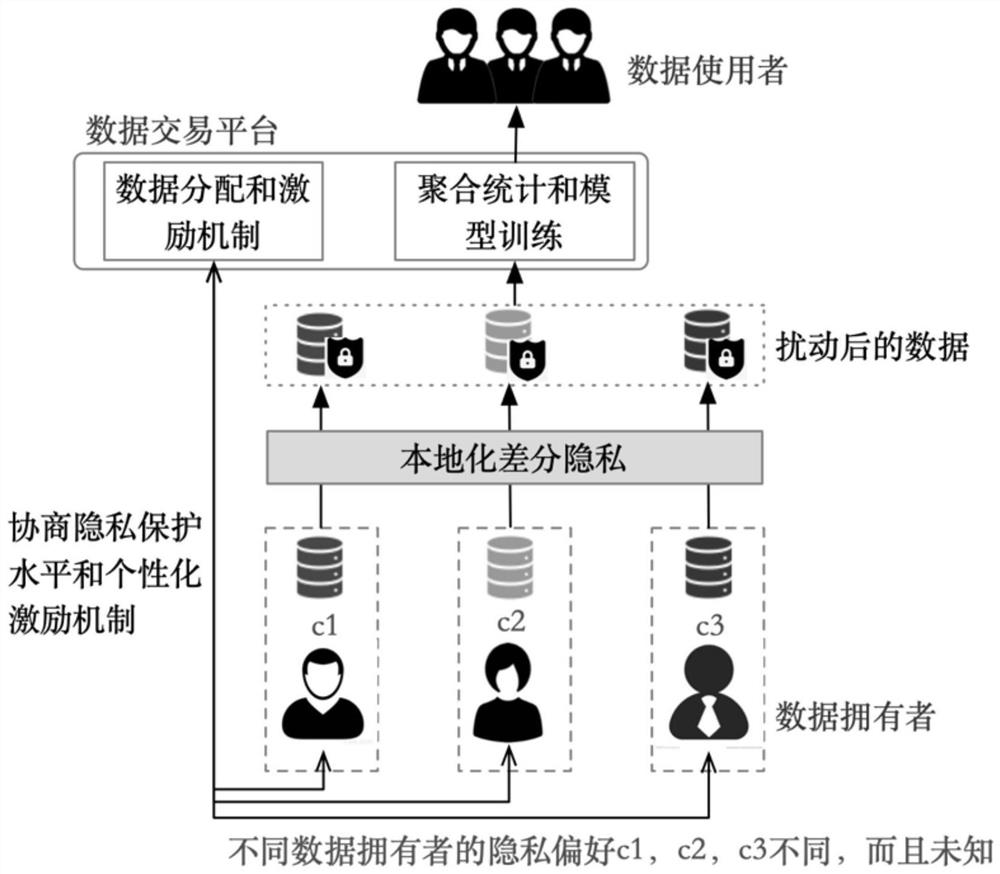
[0028] like figure 1 Schematic diagram of individualized privacy and autonomous control of data privacy for the data owner shown. In the problem solved by the present invention, there are three types of participants: data owner, data transaction platform and data user. Data users submit data acquisition requirements to the data trading platform; data owners negotiate with the data trading platform on the privacy protection level and personalized incentive mechanism according to their privacy preferences, and increase disturbance to the original data according to the agreed pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com