Byzantine attack defending method in decentralized federated learning based on block chain
A decentralized, blockchain technology, applied in the field of information security, can solve problems such as increasing communication overhead, and achieve the effect of reducing computing overhead, improving efficiency, and reducing computing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
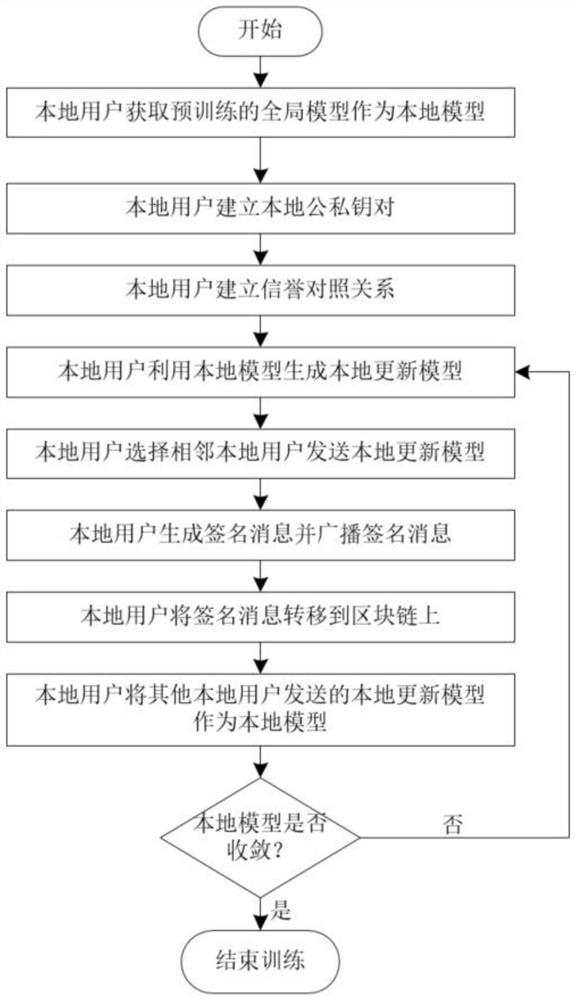
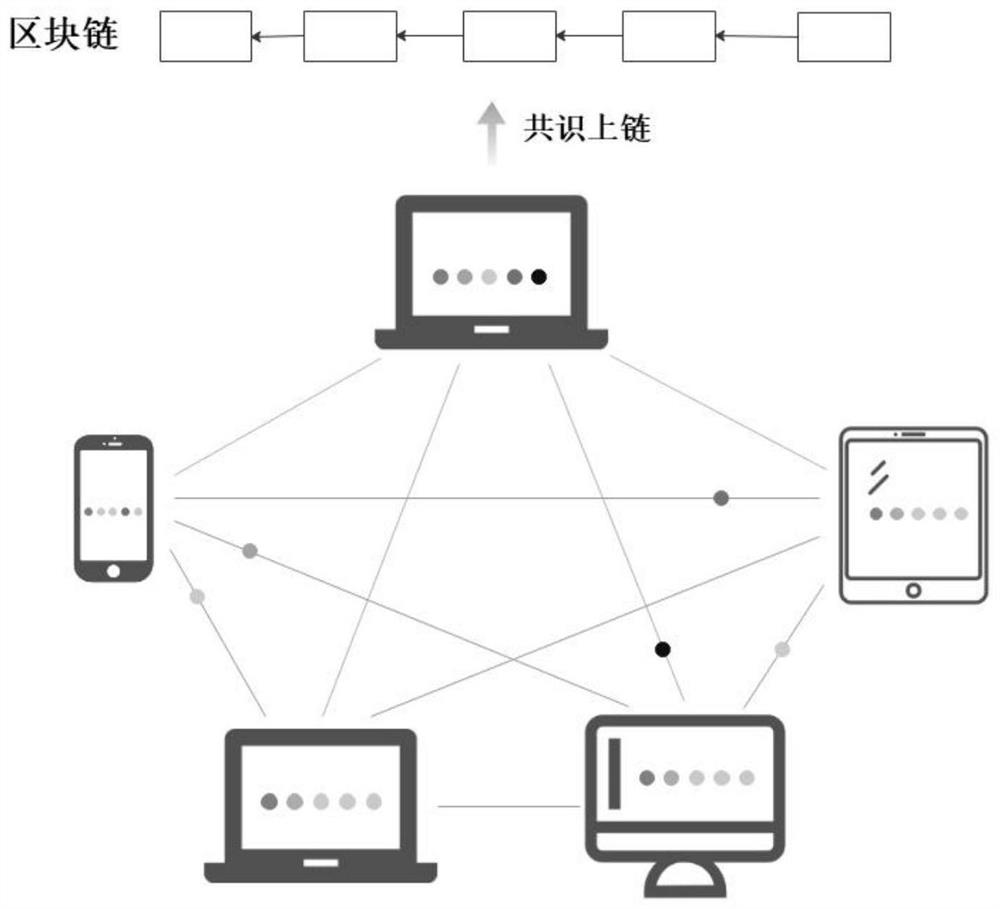
[0055] Decentralized federated learning relies on direct interaction between adjacent users to distribute the training model tasks to other users in the system, thereby obtaining a model with good generalization ability. Specifically, users participating in decentralized federated learning hold their own private data and obtain a pre-trained global model as a local model, use the private data to train the local model to obtain a local update model, and send the local update model to neighboring user, and receive the locally updated model sent by neighboring users as a local model for retraining. This decentralized federated learning model update process is iterative until the user's local model converges.
[0056] The present invention will be further described in detail below with reference to the accompanying drawings and embodiments.
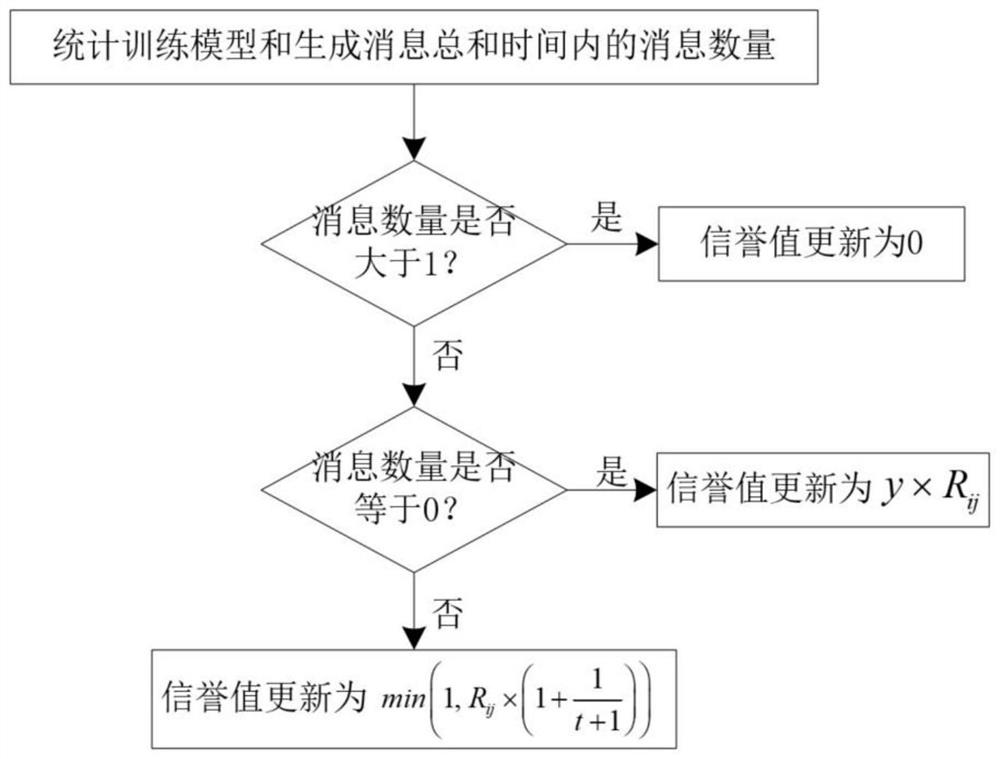
[0057] refer to figure 1 and figure 2 , to further describe the Byzantine attack defense method in the blockchain-based decentralized fe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com