Identity authentication method and system
An identity authentication and user terminal technology, applied in the field of system security, can solve problems such as different message types, achieve the effects of convenient use, avoiding errors, and avoiding system freezes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] The invention will be further described below with reference to the accompanying drawings and specific embodiments.
[0051] This section includes several different examples.
[0052] However, it should be pointed out that different embodiments of the present invention respectively solve one or more technical problems mentioned in the background art, and achieve corresponding technical effects, and different combinations of embodiments can solve all the mentioned technical problems and achieve all technical problems. effect; however, it is not required that every single embodiment of the present invention solves all technical problems or obtains all improvements. The corresponding embodiments aimed at solving a certain problem or improving a single technical effect can all constitute independent technical solutions of the present invention.
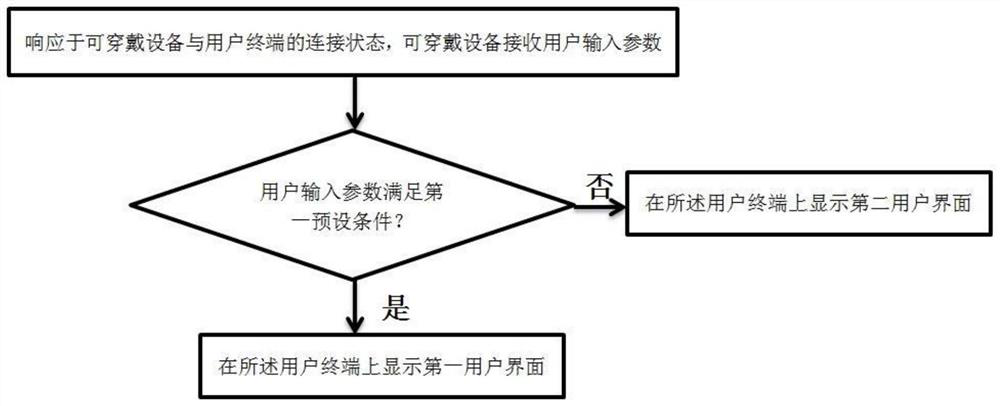
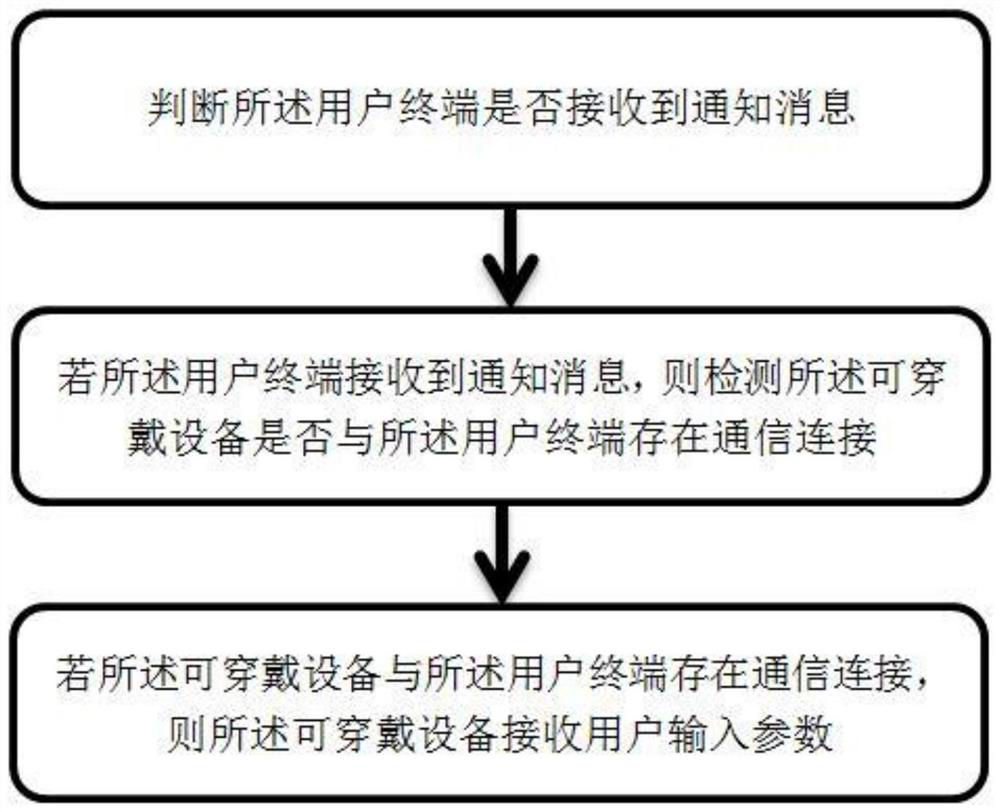
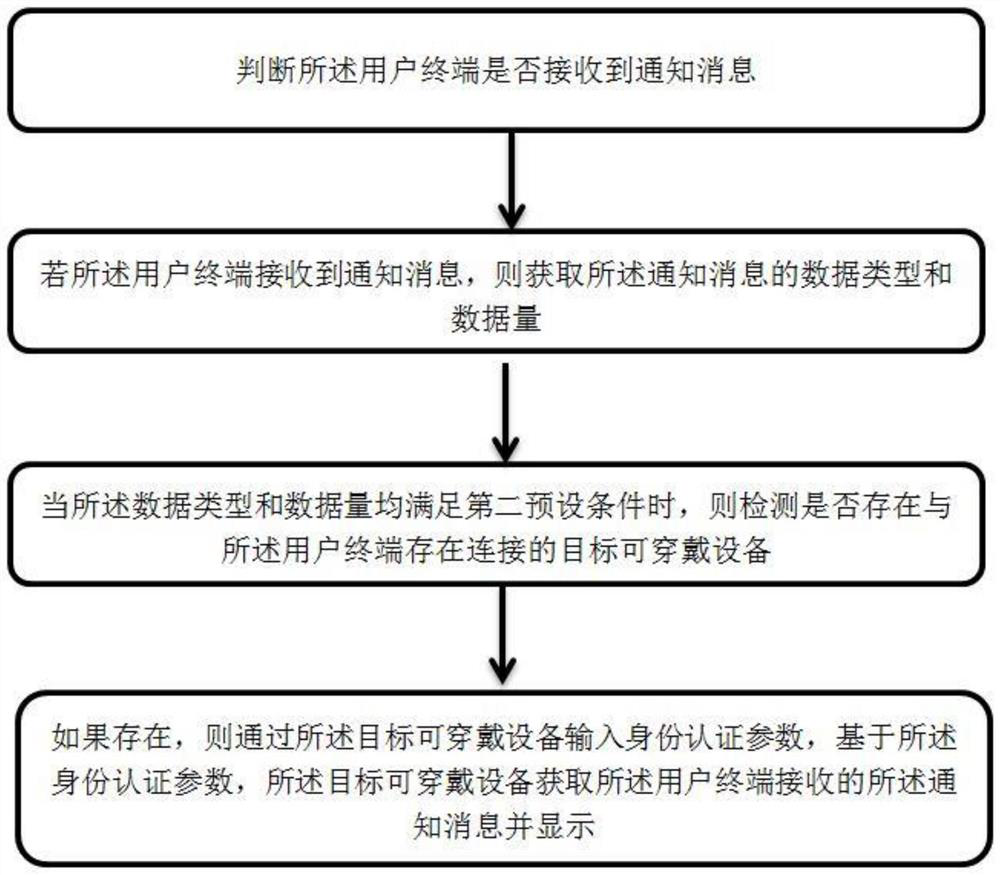
[0053] see figure 1 , figure 1 It is a schematic flowchart of an identity authentication method according to an embodiment of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com