Roaming access method of mobile node in radio IP system
A mobile node and wireless technology, applied in transmission systems, wireless communications, wireless network protocols, etc., can solve problems such as password leaks, simultaneous satisfaction, and security cannot be reduced, and achieve high efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
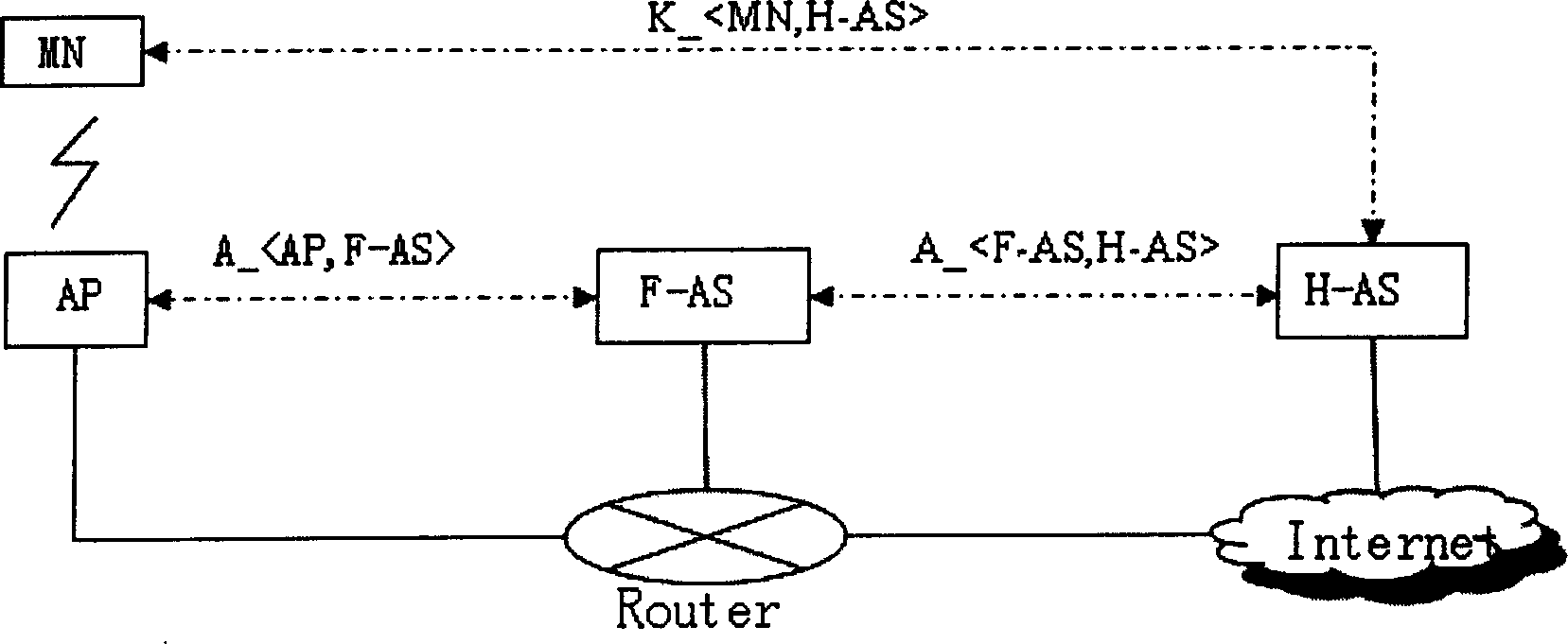
[0041] exist figure 1The MN is the mobile node, the AP is the access node, the F-AS and the H-AS are the foreign and home authentication servers respectively, and the mobile node MN and the access node AP are required to have public key certificates and corresponding certificates issued by their respective authentication servers. private key. The dotted lines in the figure represent the logical security connections, and the solid lines represent the actual physical connections. The mobile node MN and its home authentication server H-AS share a security association K_. The access node AP and the foreign authentication server F-AS have a secure channel A_, and the access node AP and the foreign authentication server F-AS trust each other; the foreign authentication server F-AS and the home authentication server H-AS There is also a secure channel A_, and the foreign authentication server F-AS is trusted by the home authentication server H-AS.
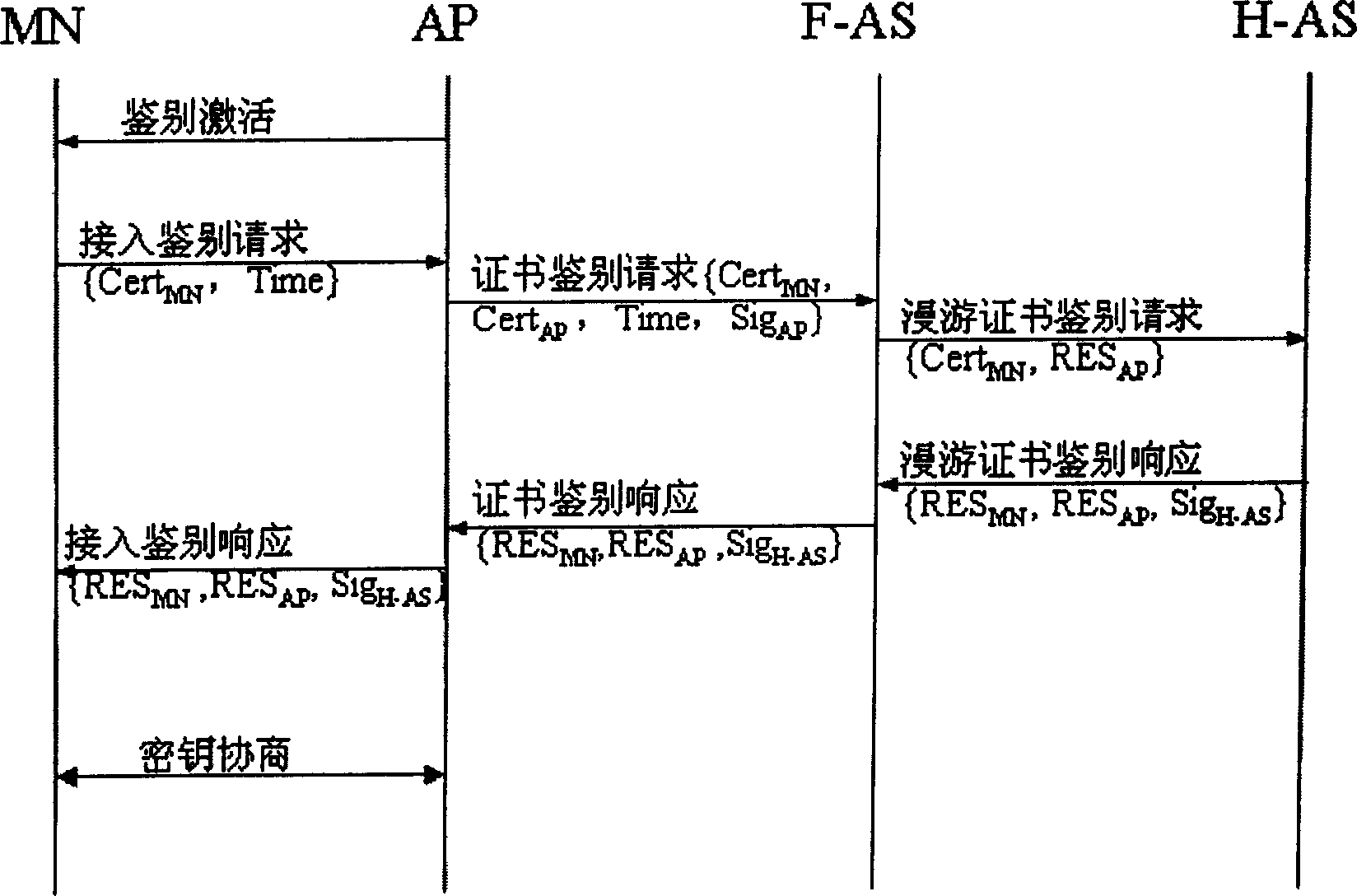
[0042] figure 2 The process f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com