Method, system and data structures for implementing nested databases
A technology of data structure and data processing system, which is applied in the direction of memory system, electrical digital data processing, special data processing application, etc., and can solve problems such as ACID characteristic conflicts and difficulties
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
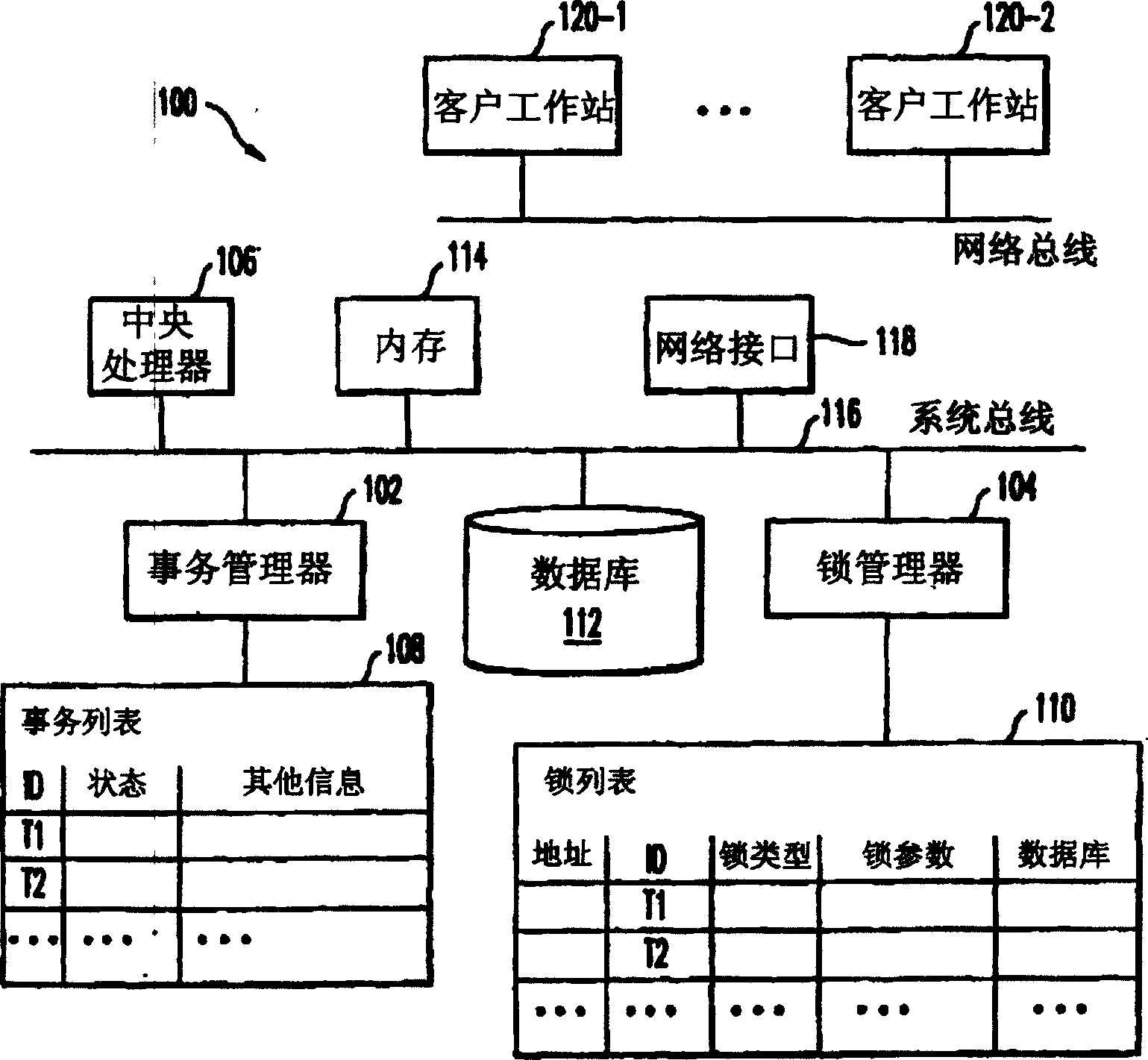
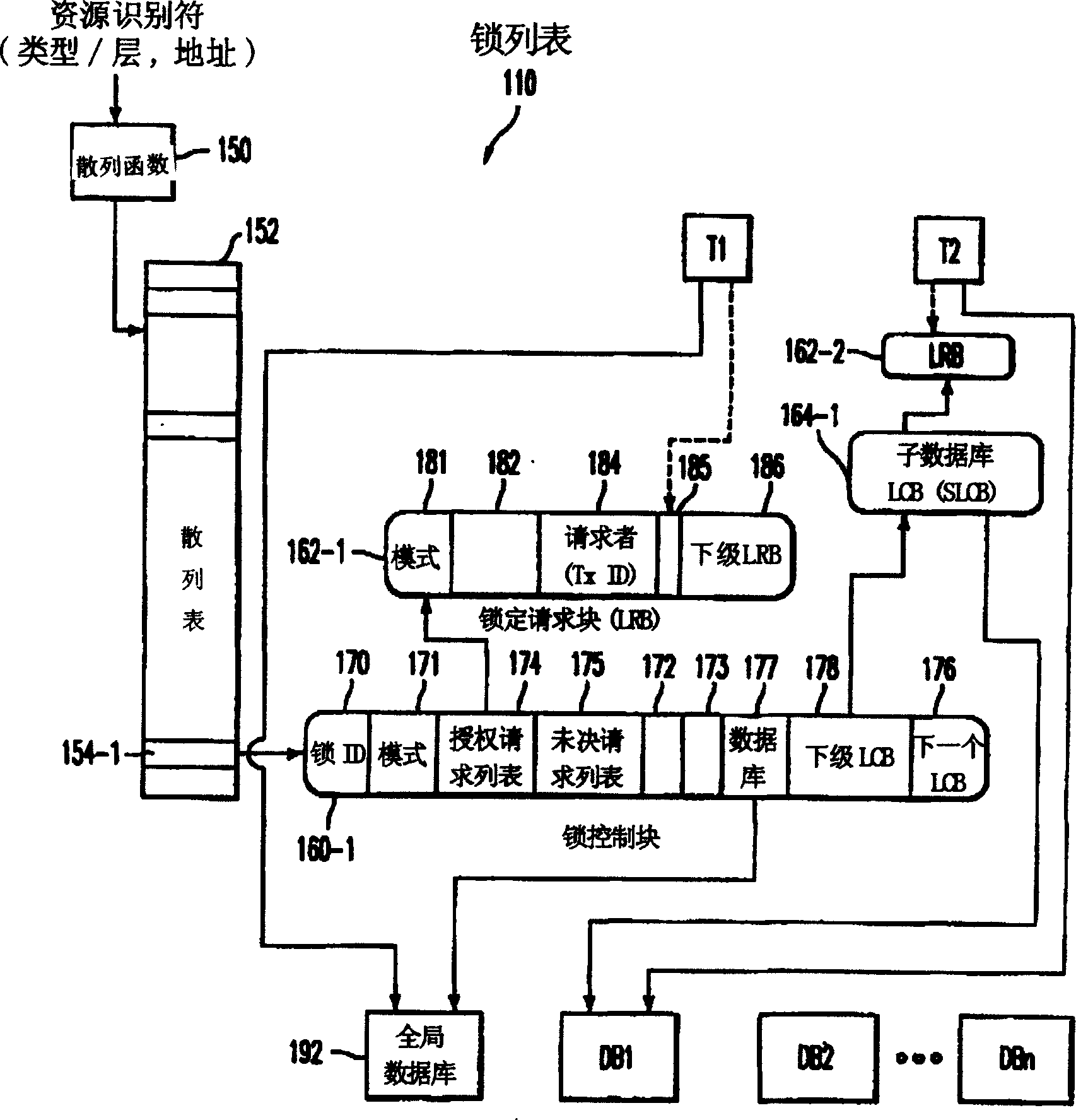
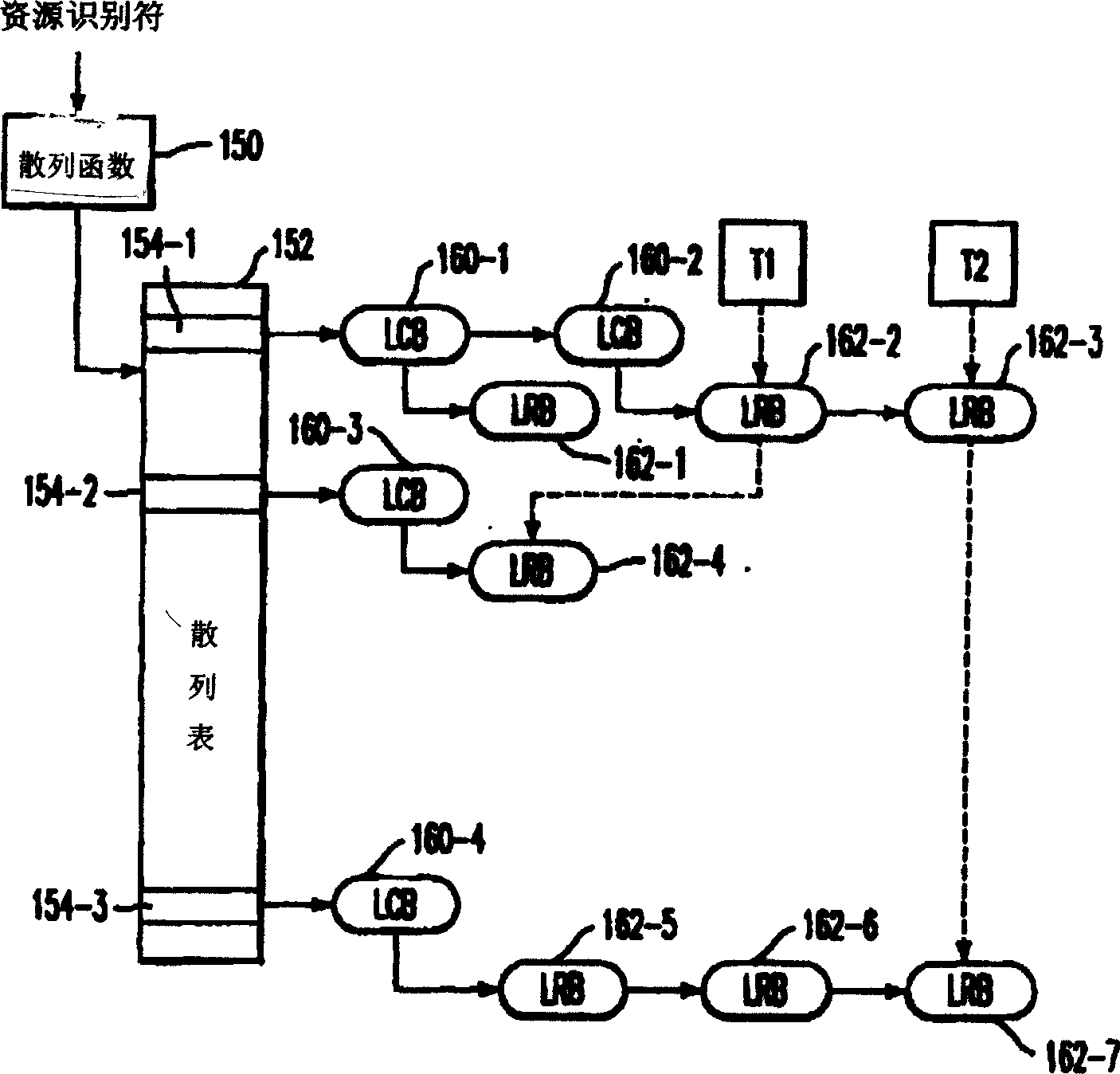
[0045] Referring now to the accompanying drawings, more specifically, such as the figure 1 , which illustrates a database management system 100 (DBMS), and in these drawings, the same reference numerals represent the same or corresponding parts. The operation and management of transactions is handled by a transaction manager 102 and a lock manager 104, both of which are software programs executed by the data processor or CPU 106 of the system. A transaction list 108 is maintained in the transaction manager, often implemented as a tree structure, to keep track of the status and attributes of pending transactions. The lock manager 104 maintains a lock list 110, commonly implemented using hash tables and various linked lists and / or tree structures (this will be discussed in more detail later). Lock list 110 keeps track of lock requests for data resources on database 112 . Lock list 110 may store information about a transaction's memory address, a transaction identifier, a lock ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com