Method for preventing IP address from forged based on rewritten address
An IP address and address technology, which is applied in the field of computer communication, can solve problems such as inability to prevent, and achieve the effects of preventing forgery, small impact on network performance, and simple rewriting operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] Accompanying drawing is the specific embodiment of the present invention;
[0021] Below in conjunction with accompanying drawing, content of the present invention is described in further detail;
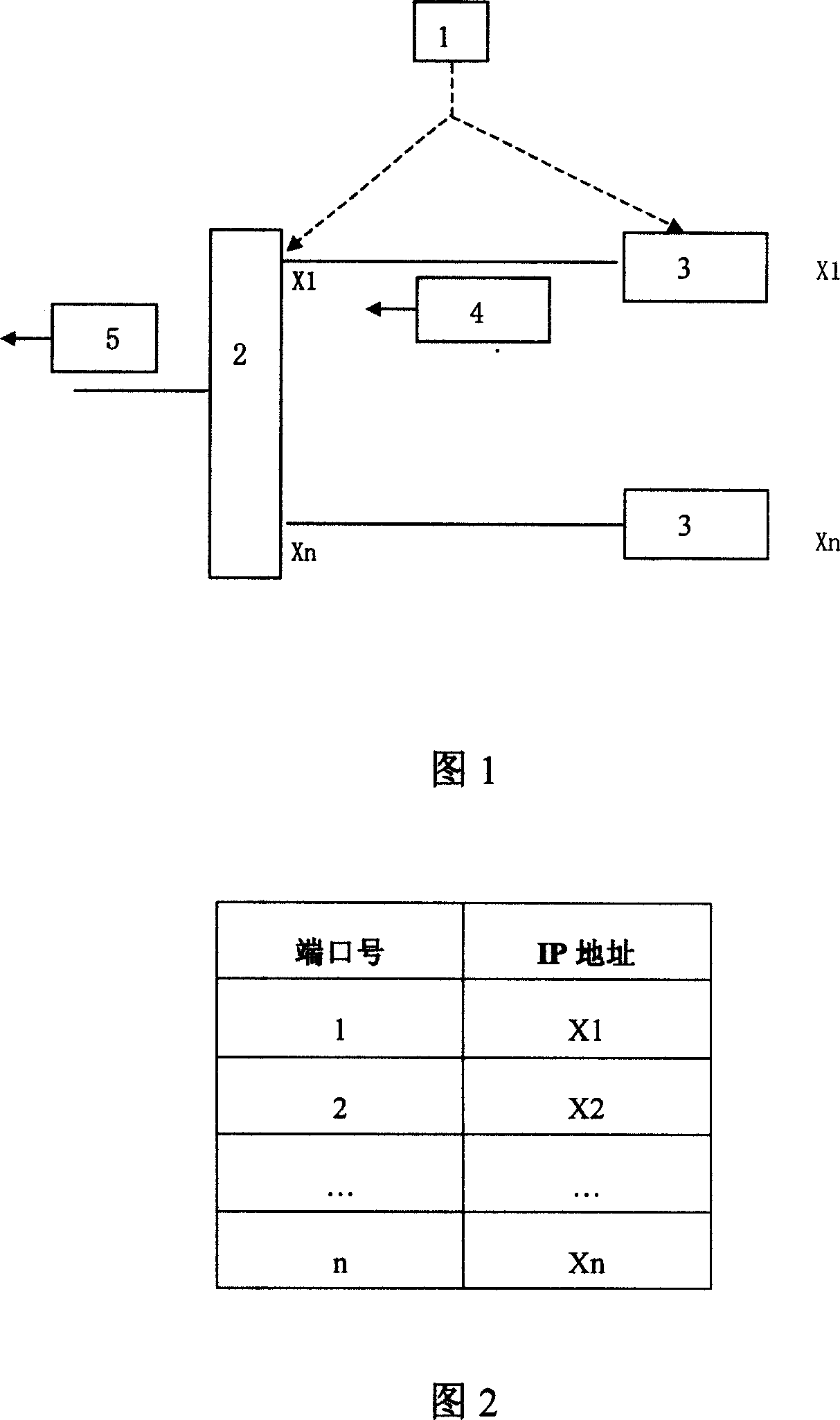
[0022] Referring to Fig. 1, 1 is a network management organization for address allocation. The network access device 2 can be an Ethernet switch, a dial-up server, a DSL concentrator, etc., and the port numbers for connecting computers are 1-N. A single computer 3 is directly connected to the network access device 2 . The IP data packet 4 is an IP packet sent by a single computer 3 . The IP data packet 5 is an IP packet after the address of the access device 2 is rewritten.
[0023] The realization process of the present invention is composed of address allocation and source IP address field rewriting in IP packets.
[0024] 1) If the port i (1≤i≤n) of the network access device 2 is not connected to a single computer 3, then the IP address field of item i in the "Port-IP ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com