Read-write access control method for plug-in memory device
A storage device, plug-and-play technology, applied in the direction of instruments, electrical digital data processing, platform integrity maintenance, etc., can solve the problems of complicating filter driver program and driver program
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
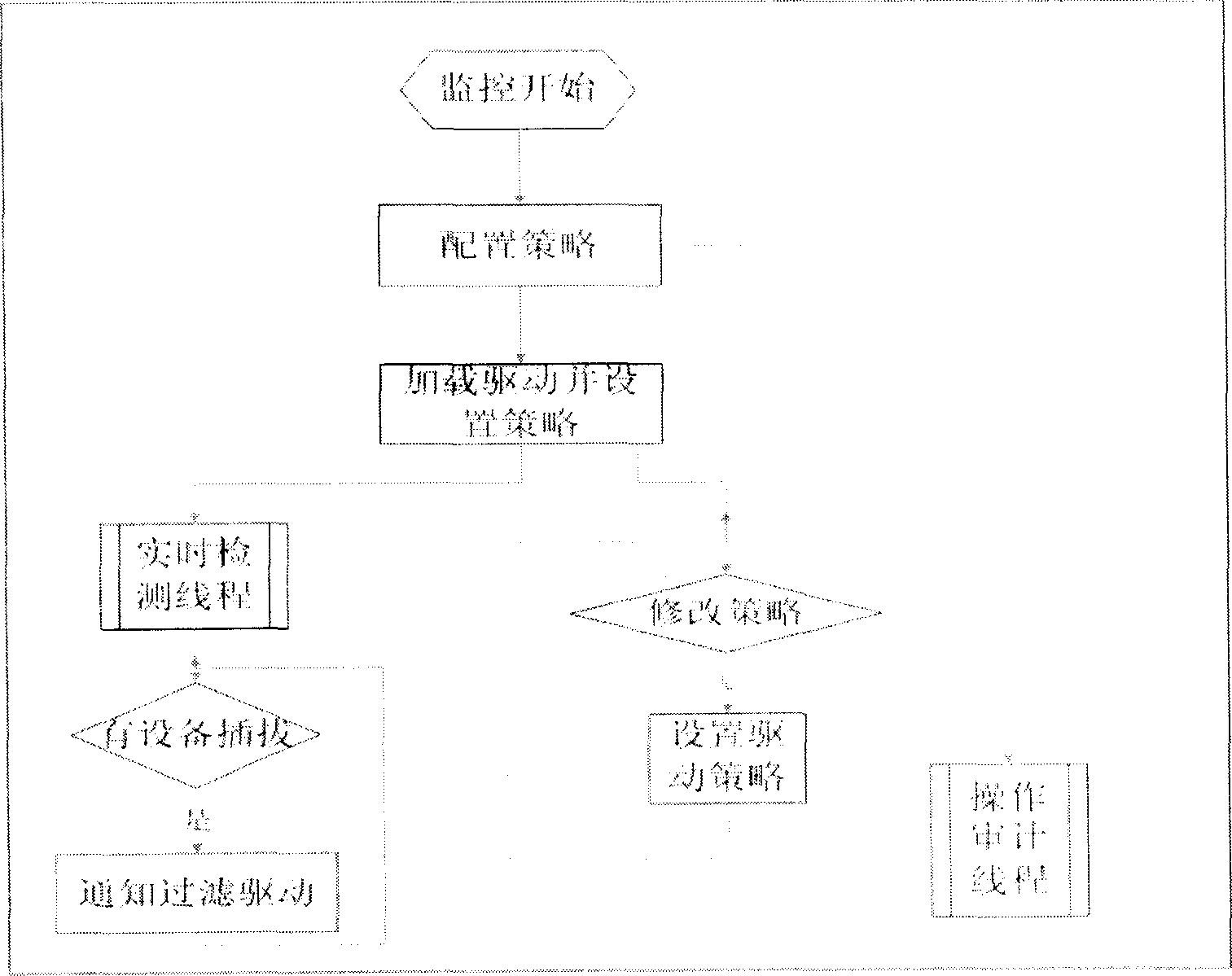
[0026] The present invention will be further described below in conjunction with accompanying drawing and specific embodiment:
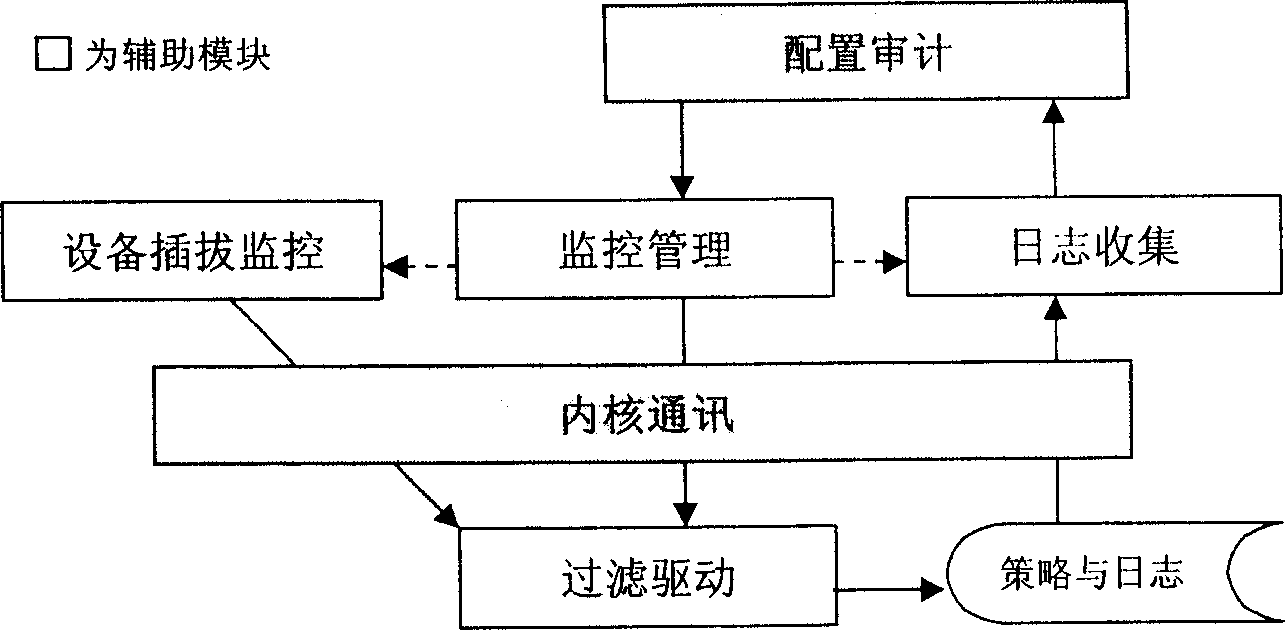
[0027] see figure 1 , the specific execution monitoring system we implemented is composed of six modules, of which five modules are in the application layer, including configuration auditing, monitoring management, log collection, kernel communication, and device plugging monitoring, and the filter driver module works in the kernel layer.
[0028] Since this embodiment is a functional component of a larger monitoring system, the two modules of configuration audit and kernel communication are not necessary modules of the present invention, but for the convenience of use and the unified implementation of design and coding , the abstraction performed.
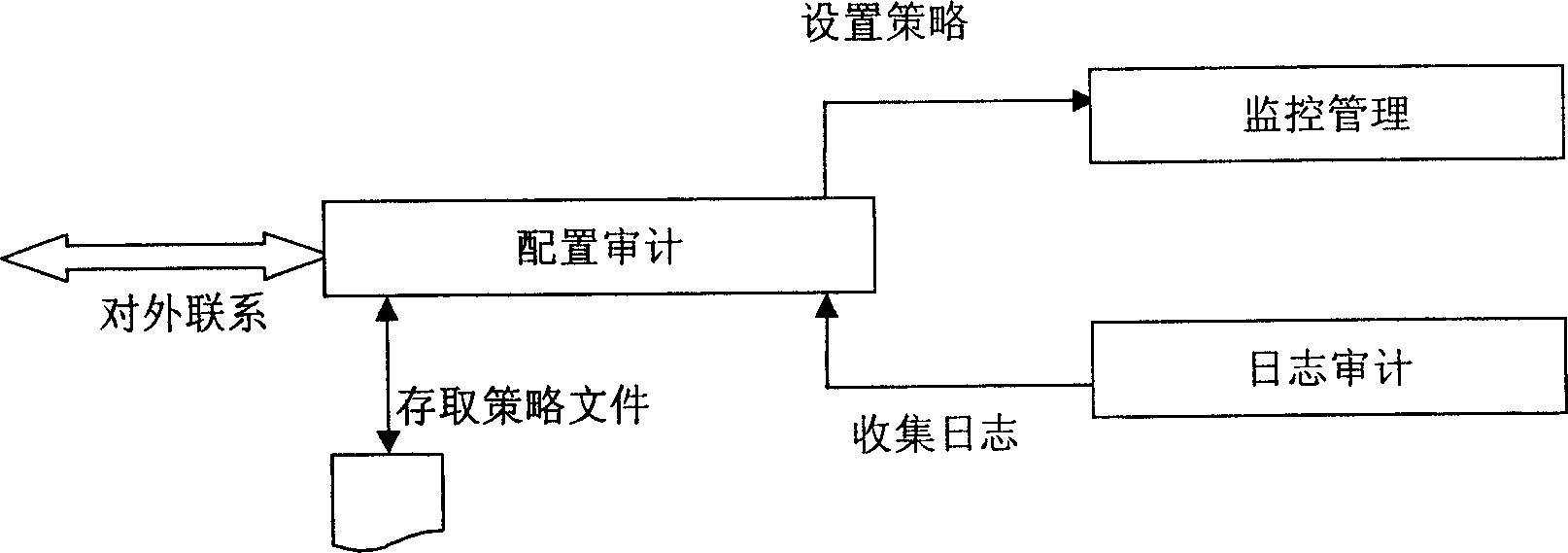
[0029] see figure 2 , the configuration of the audit module is for the system to communicate with the outside world, such as the user interface or the remote management terminal to communicate, the un...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com