Network intruding danger estimating method based on immunity
A network intrusion and risk technology, applied in the field of information security, can solve the problems of inability to identify new attacks and variants of existing attacks, too simple network security calculation, and lack of self-adaptation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The idea of the present invention will be described in detail below in conjunction with the accompanying drawings.
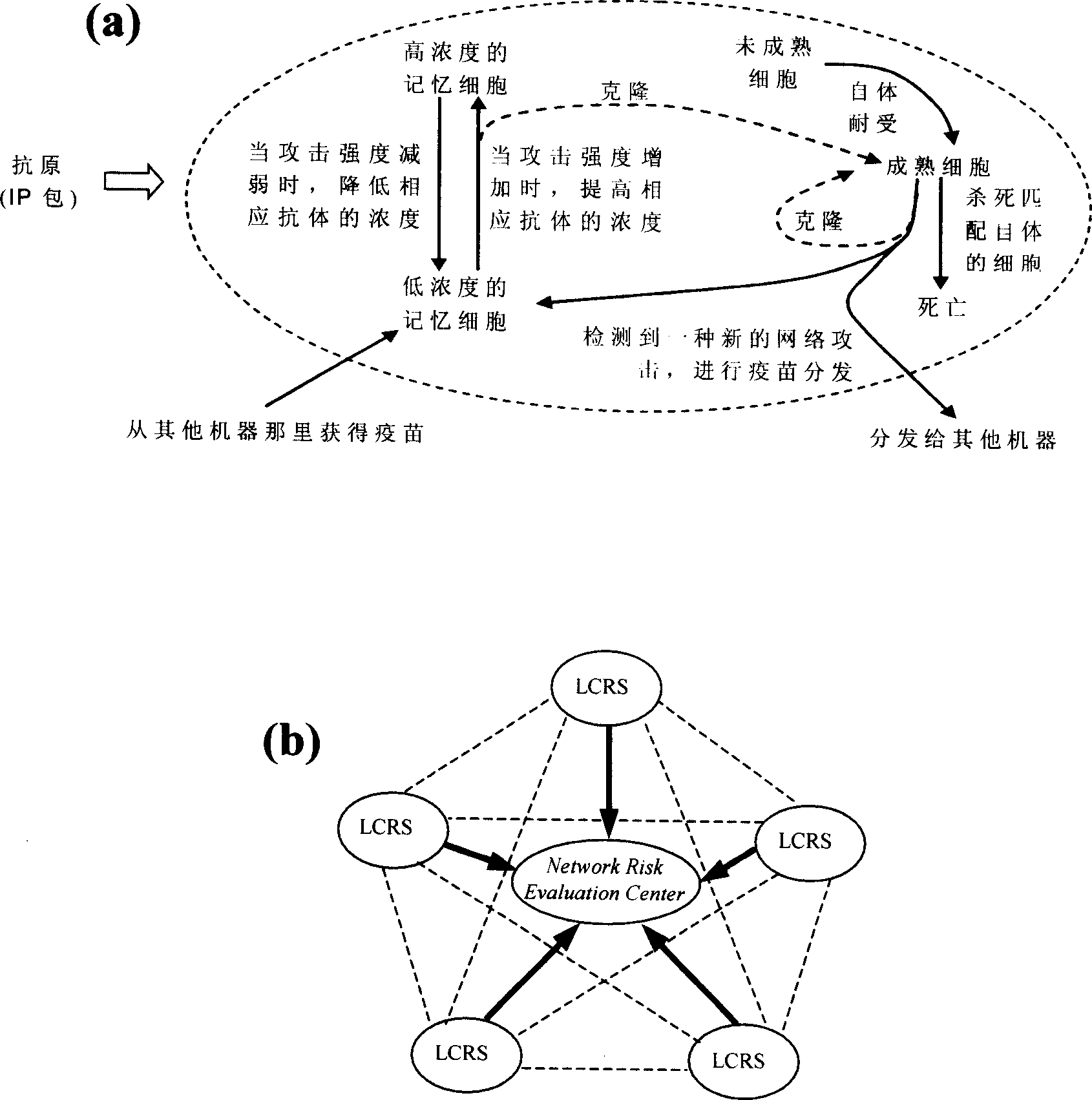
[0032] figure 1 Is the working principle of the present invention.
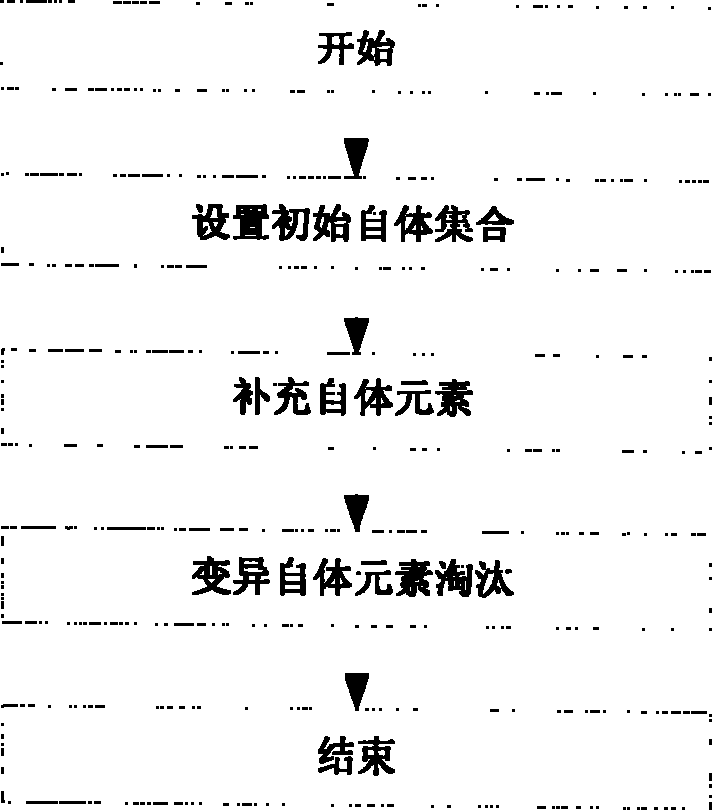
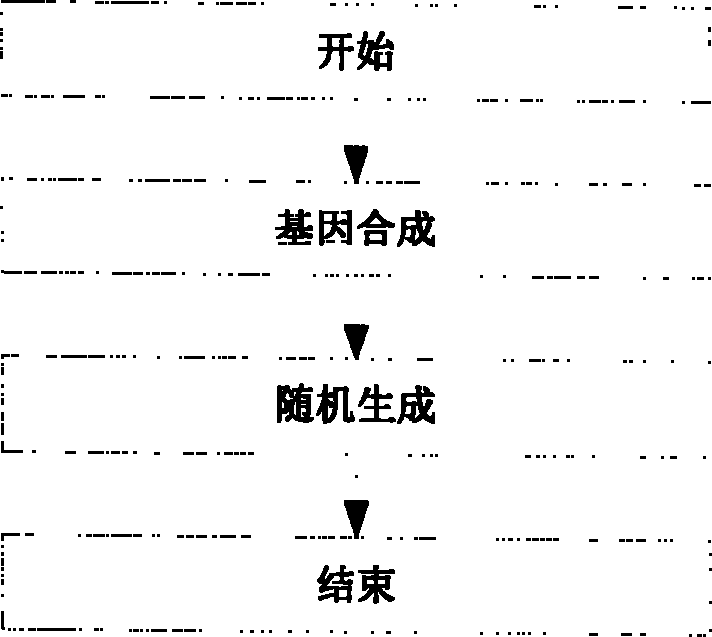
[0033] figure 1 The basic principle of the invention is given. We simulate the human immune system, and first design a local danger sensor LCRS (such as figure 1(a), quite a local immune cycle). In LCRS, we use an artificial immune cell to detect attacks from the network: when an immune cell detects an attack, it will self-clone and produce a large number of similar cells to resist more violent network attacks, and at the same time increase the concentration of its own antibodies In order to increase its vigilance; when the network attack is eliminated, the concentration of the corresponding cell antibody will also decay to 0 synchronously, indicating that the alarm is lifted. In this way, by calculating the concentration of antibodies in the host, the type, quantity, intensity an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com