Method for raising network security via message processing
A message processing and security technology, applied in the field of network communication, can solve the problems of complicated ACL specification configuration and maintenance work, abnormal network equipment, and heavy equipment maintenance workload, so as to improve the anti-attack capability and network reliability, Guarantee the effect of stable operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] In order to facilitate those skilled in the art to understand and implement the present invention, the embodiments of the present invention are now described with reference to the accompanying drawings.
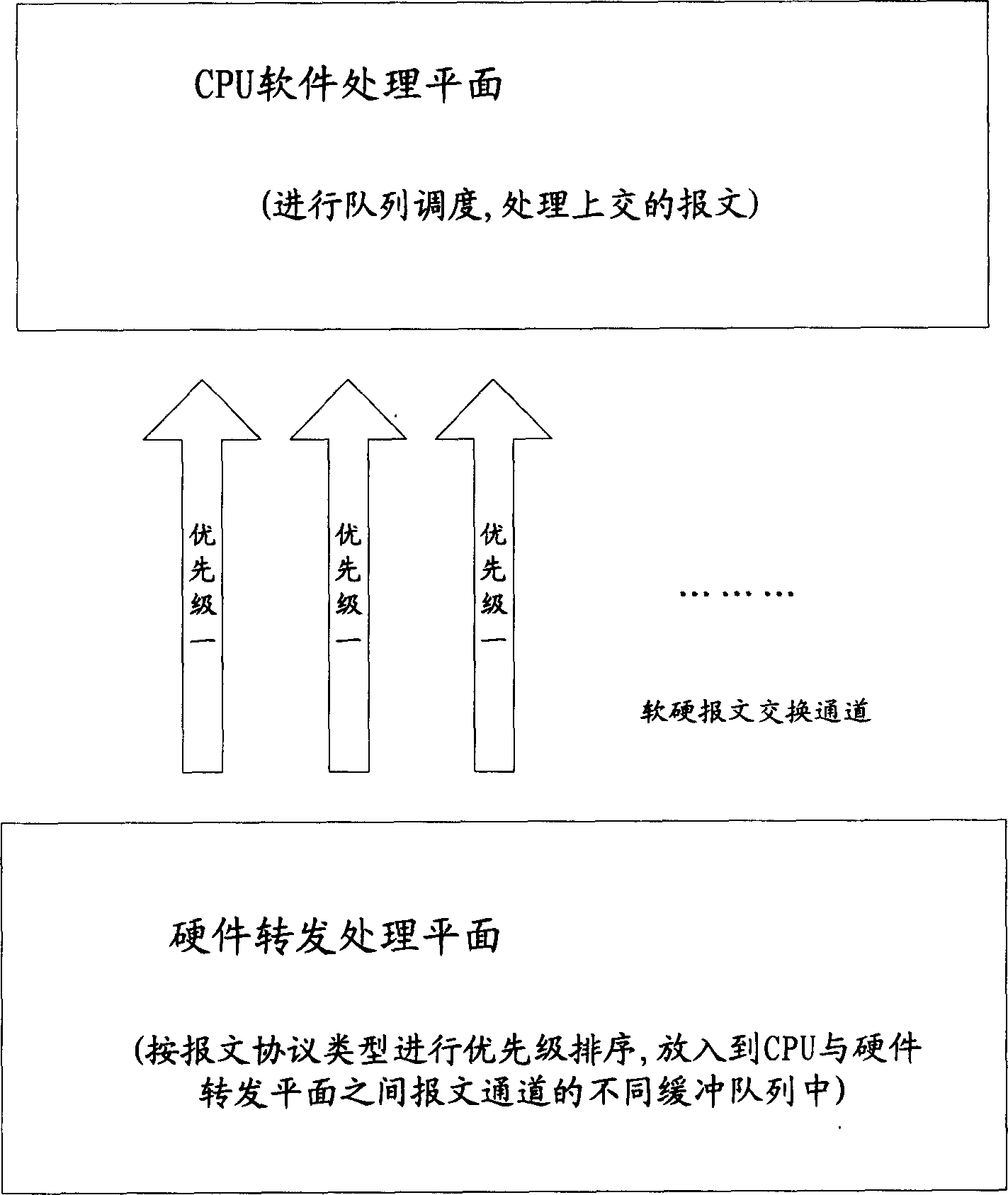
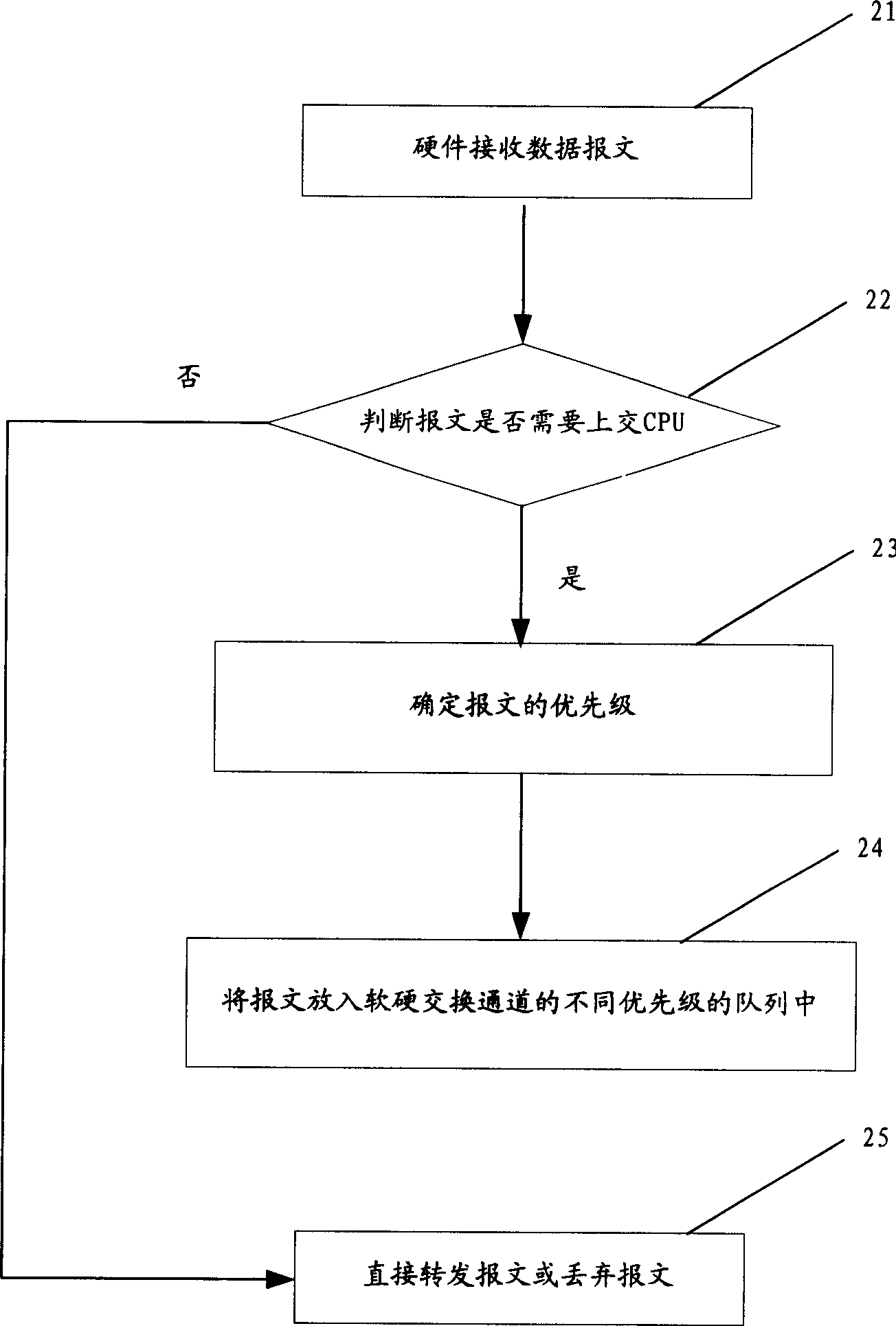
[0026] Such as figure 1 As shown, the basic idea of the present invention is: the hardware recognizes the received messages, and the messages that need to be handed over to the CPU for processing are prioritized according to the message protocol type and placed in the message between the CPU and the hardware forwarding plane. In the buffer queue corresponding to the priority of the message channel; for the messages that do not need to be handed over to the CPU for processing, if they are normal messages, they are directly forwarded, otherwise other unrecognized or illegal messages are directly discarded. The method for improving the ability to prevent network attacks through message processing of the present invention will be described in detail below.
[0027] Refer to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com