Method for negotiating about security alliance
A security and alliance technology, applied in the field of IP security, can solve problems such as waste of network resources, unsuccessful SA negotiation process between communication parties, and affect normal operation of business, so as to achieve the effect of ensuring normal operation and successful negotiation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
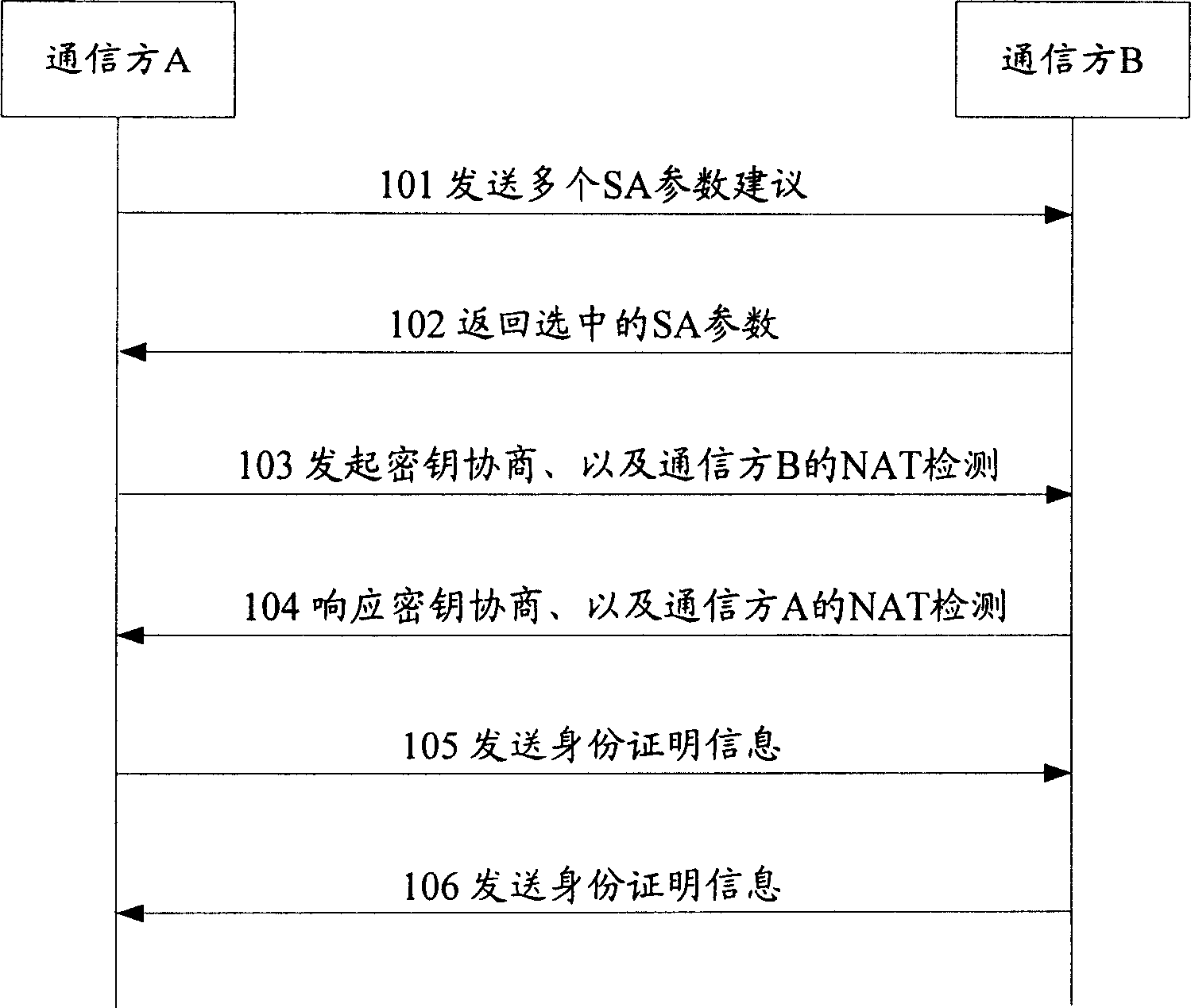
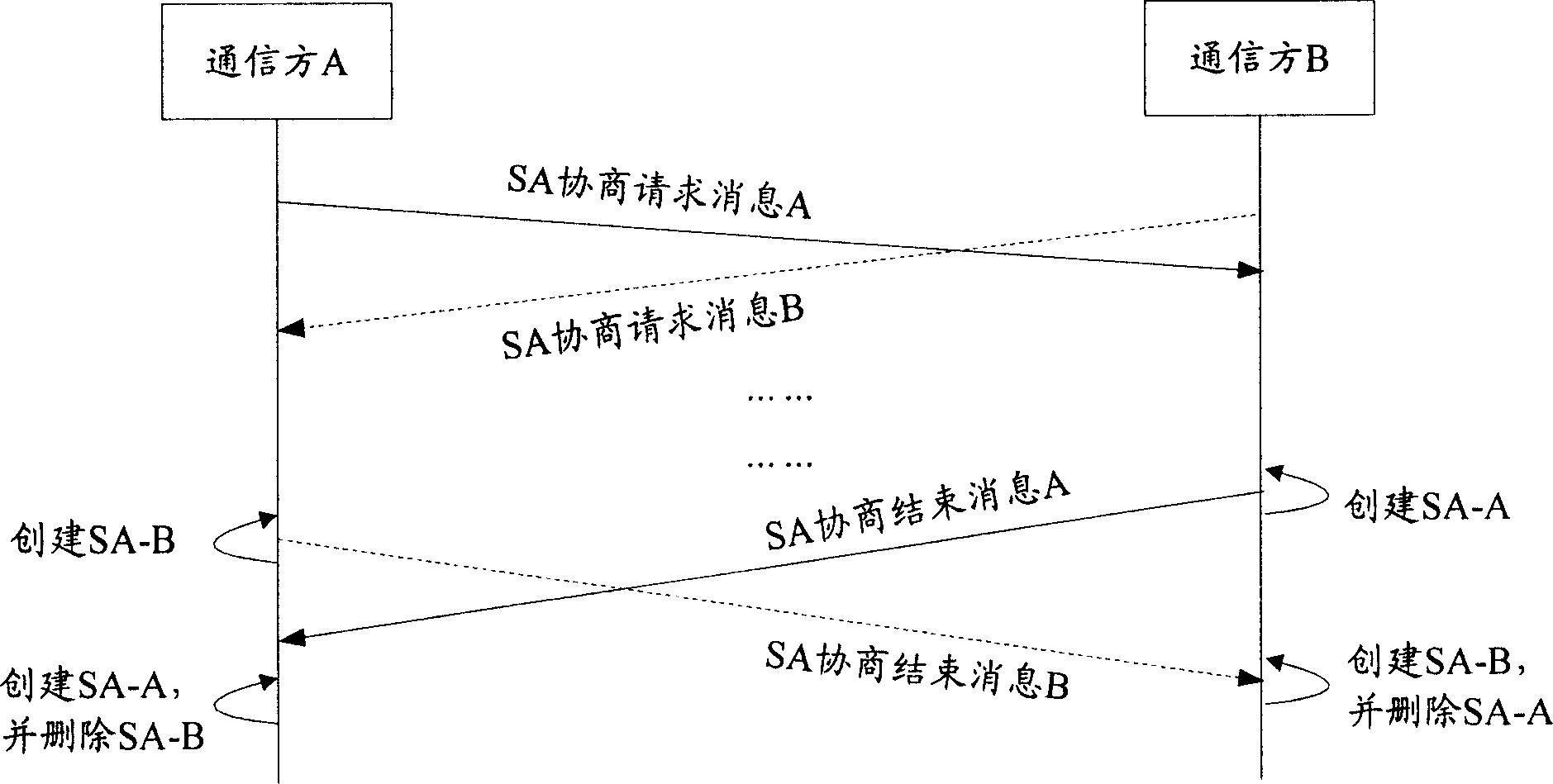
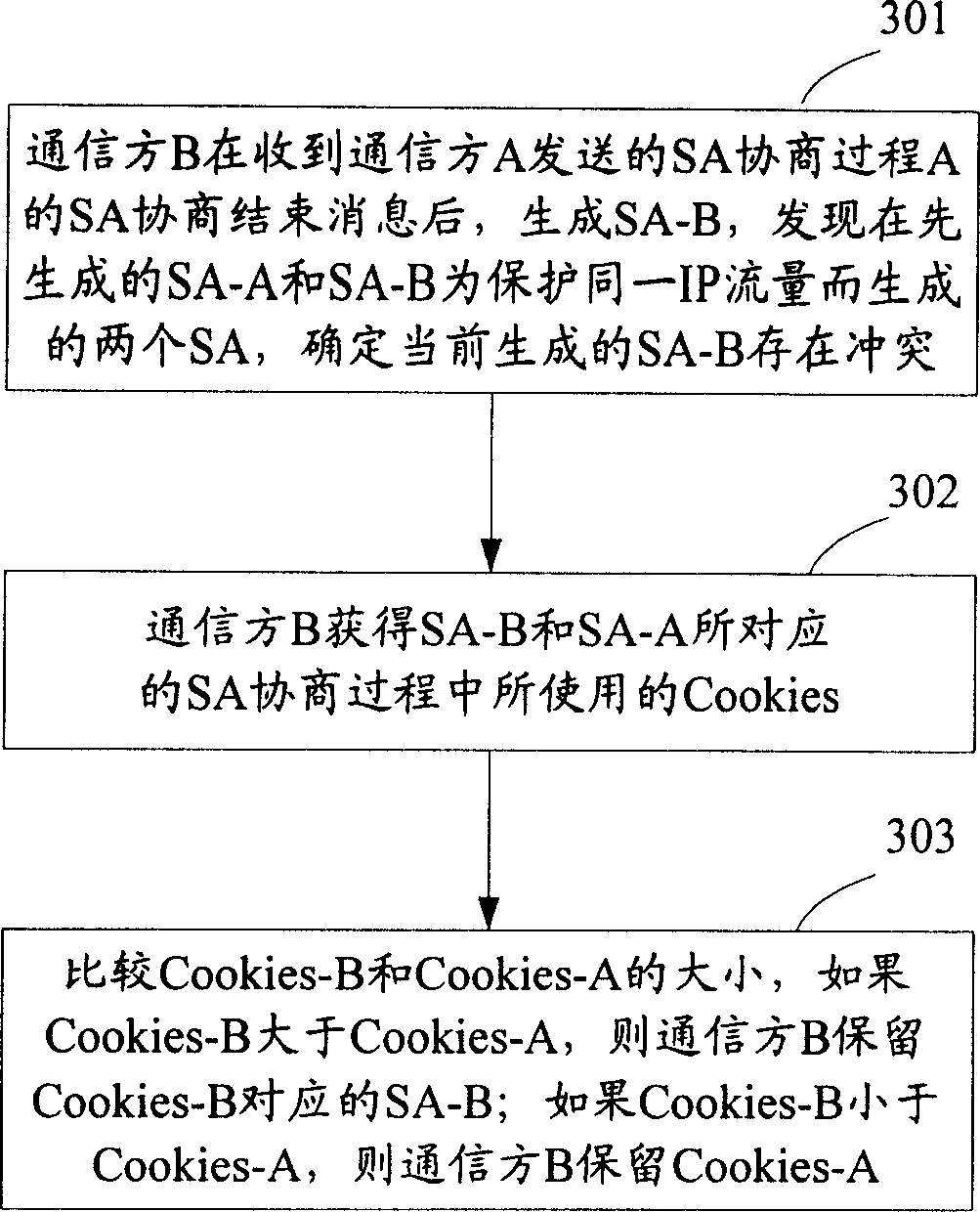
[0051] The core idea of the present invention is: set selection rules, and when it is determined that there is a conflict in the two SA negotiation processes, obtain the characteristics of the two conflicting SA negotiation processes according to the selection rules, and select the conflicting SA negotiation process according to the obtained characteristics and selection rules. An SA corresponding to the two SA negotiation processes.
[0052] Here, there are two ways to determine that there is a conflict in the negotiation process of the two SAs. One is: when the communication party generates two SAs to protect the same IP traffic, it is determined that the SA negotiation process corresponding to the two SAs has a conflict; the other is : When the communication party receives the SA negotiation request message, it judges whether there is a conflict in the SA negotiation process corresponding to the SA negotiation request message. In the SA negotiation process, it can be dete...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com