Internet access system and method
A network access and network access technology, applied in the Internet access system and access field, can solve the problems of Internet user account theft, account uniqueness restrictions, etc., achieve convenient use, solve the problem of strong calculation of weak passwords, and promote business The effect of development
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
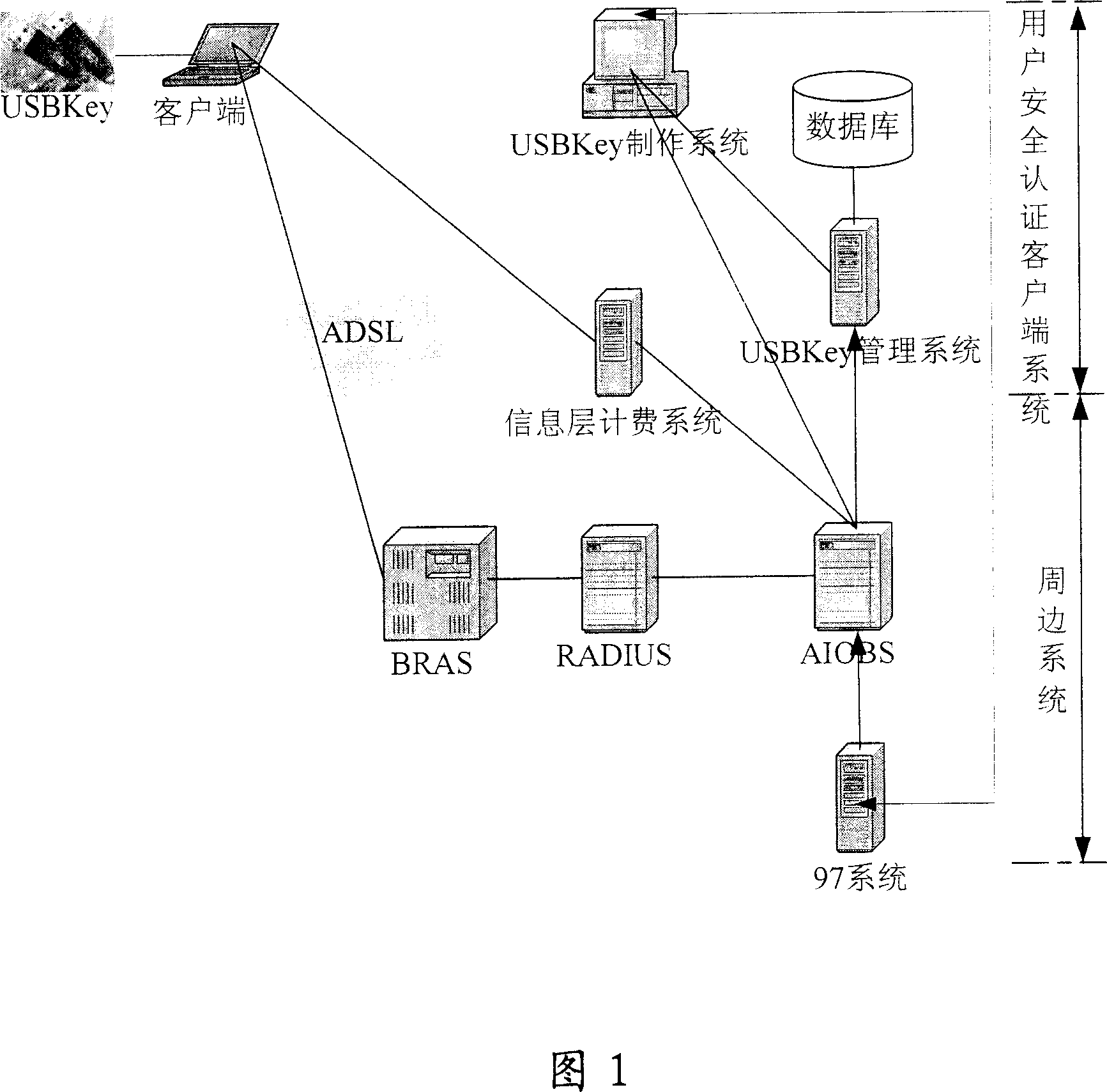
[0050] In the prior art, for broadband users developed through the three channels of on-site office, online acceptance, and agency, users need to set a query password when applying for broadband access services, and the broadband access account is provided when the communication company installs a computer for the user. distributed to users. Then, the user can obtain the broadband access account corresponding to the broadband access account by using the broadband access account provided by the communication company and the query password set when applying for broadband service on the online acceptance page or by dialing the service number of the broadband access (such as ADSL) account inquiry system. password (such as the password corresponding to the ADSL account).
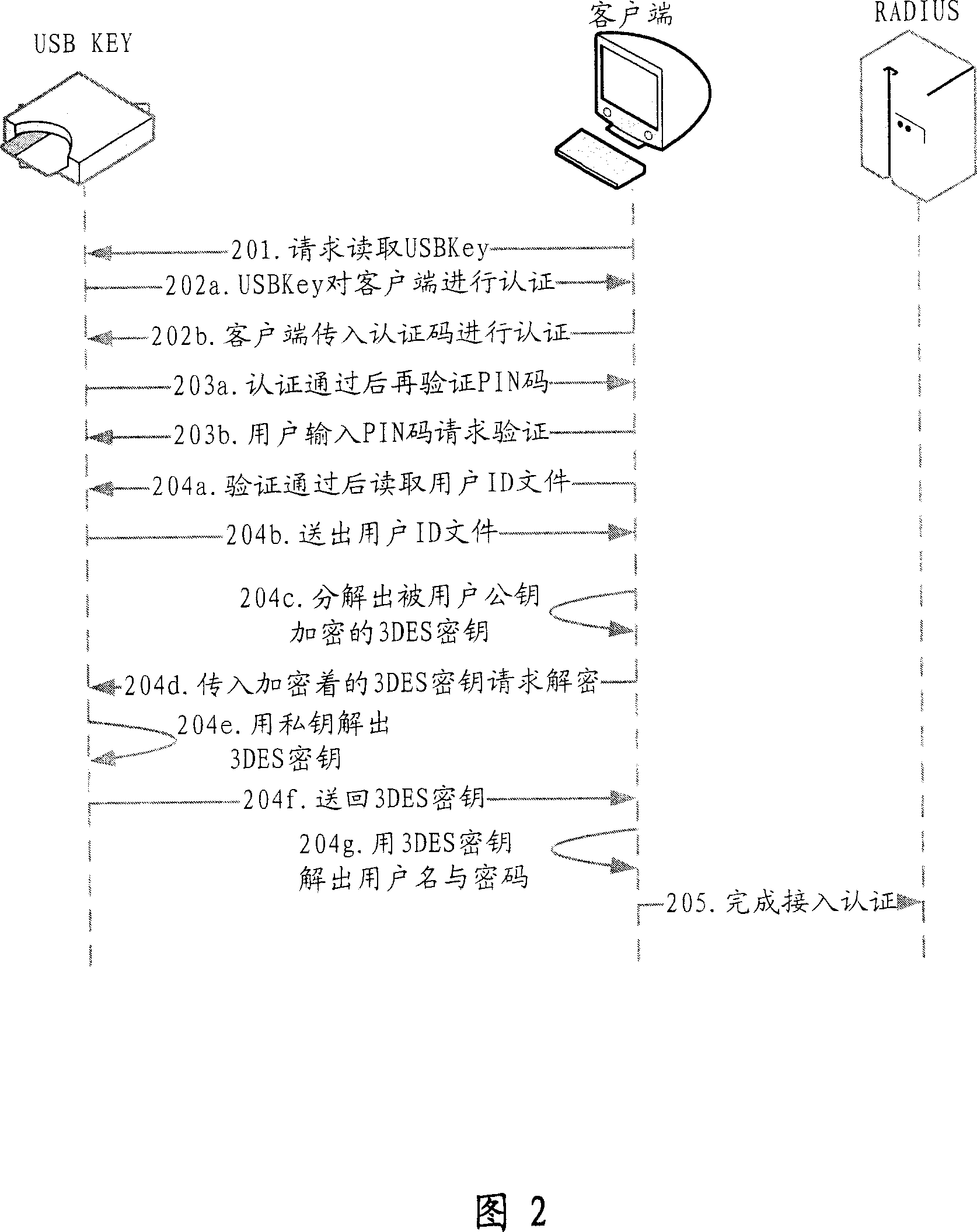
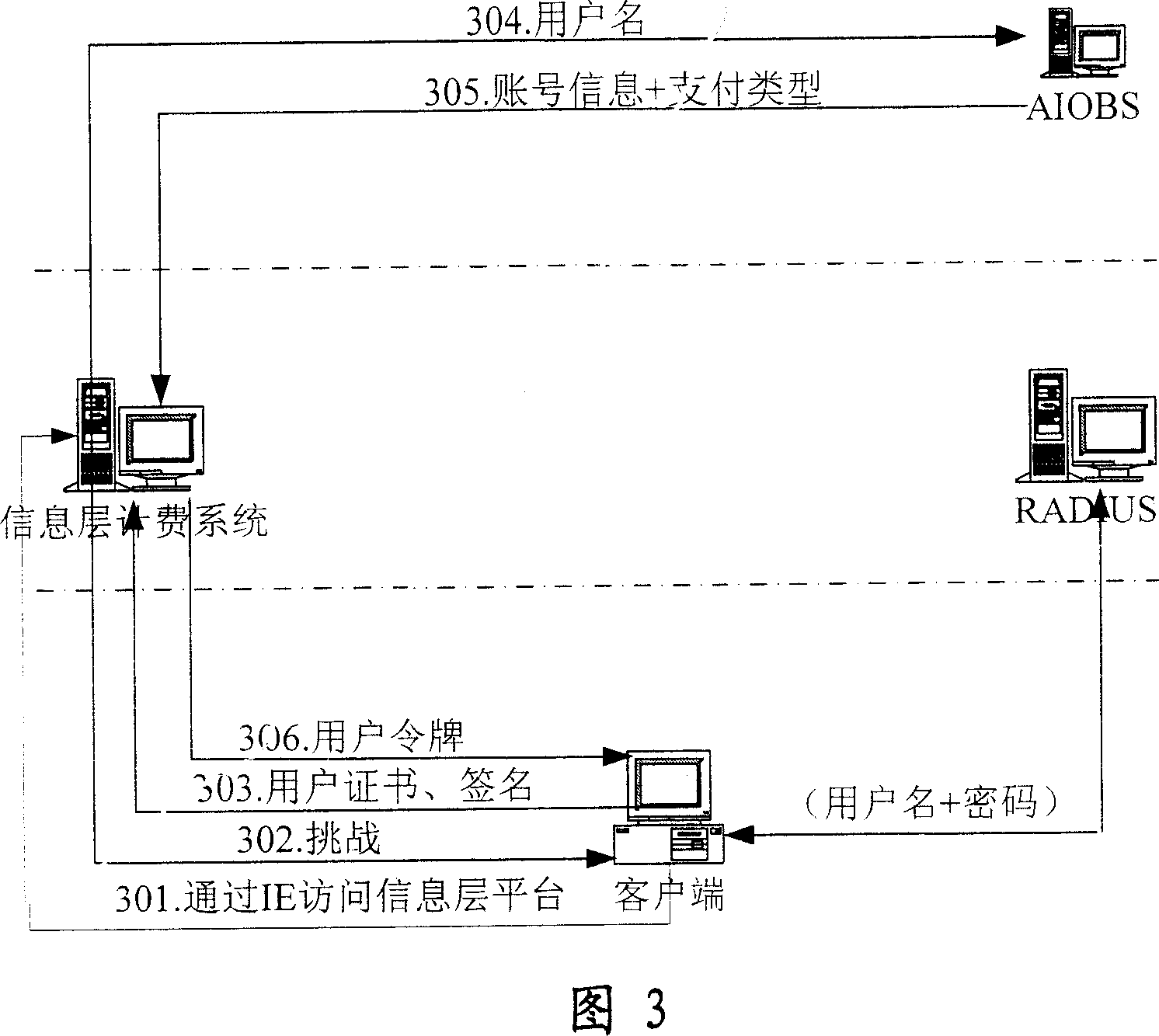
[0051] The present invention relies on the client, combines the PKI (Public Key Infrastructure) security mechanism, and utilizes an external authentication device (a special hardware, which will be described late...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com