System and methods for efficient authentication of medical wireless self-organizing network nodes
An ad hoc network, wireless network technology, applied in transmission systems, wireless communication, digital transmission systems, etc., can solve the problems of symmetric key cryptography limited to scalability and security management, complex key management, etc., to optimize usability and sturdy effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
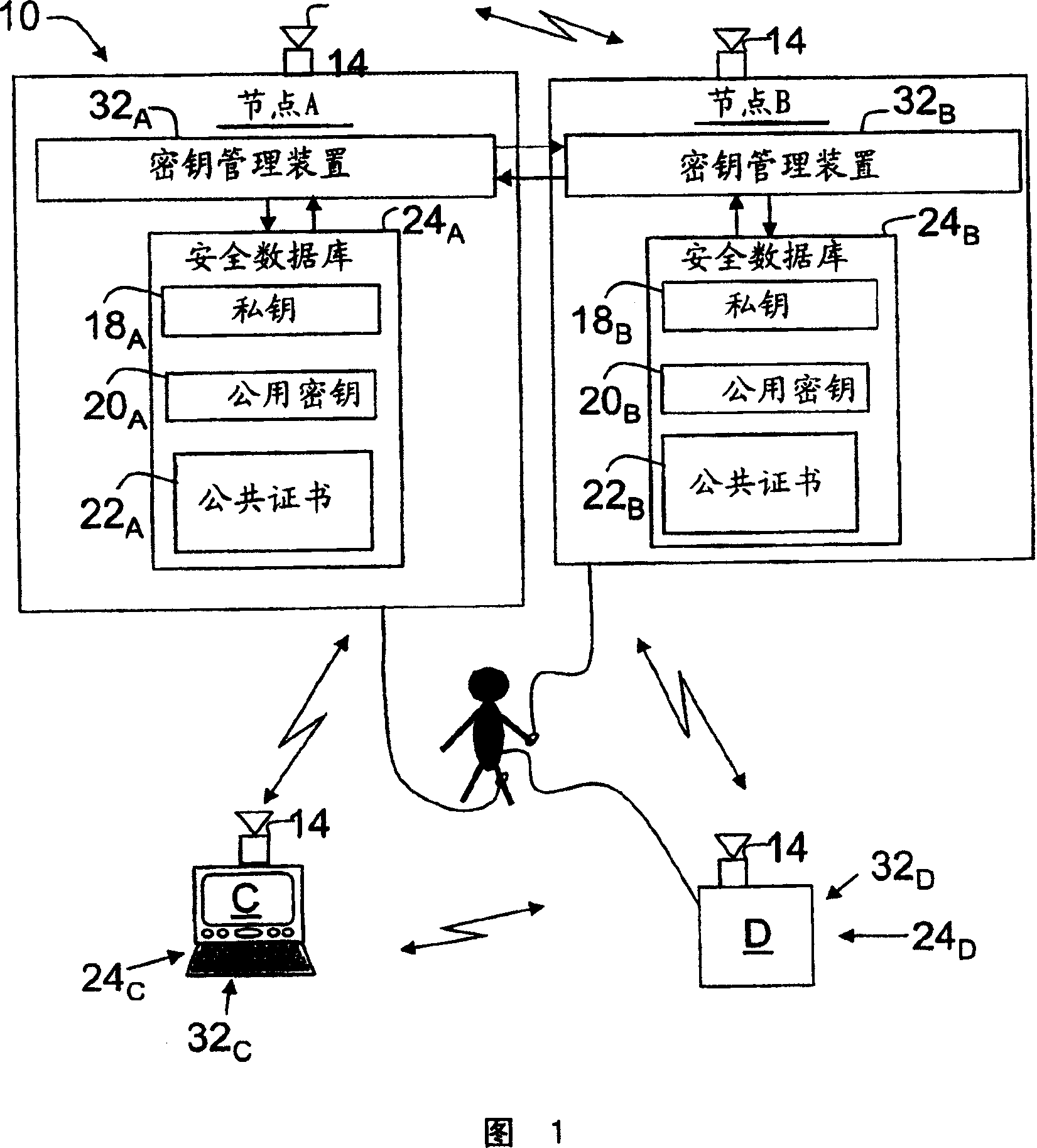
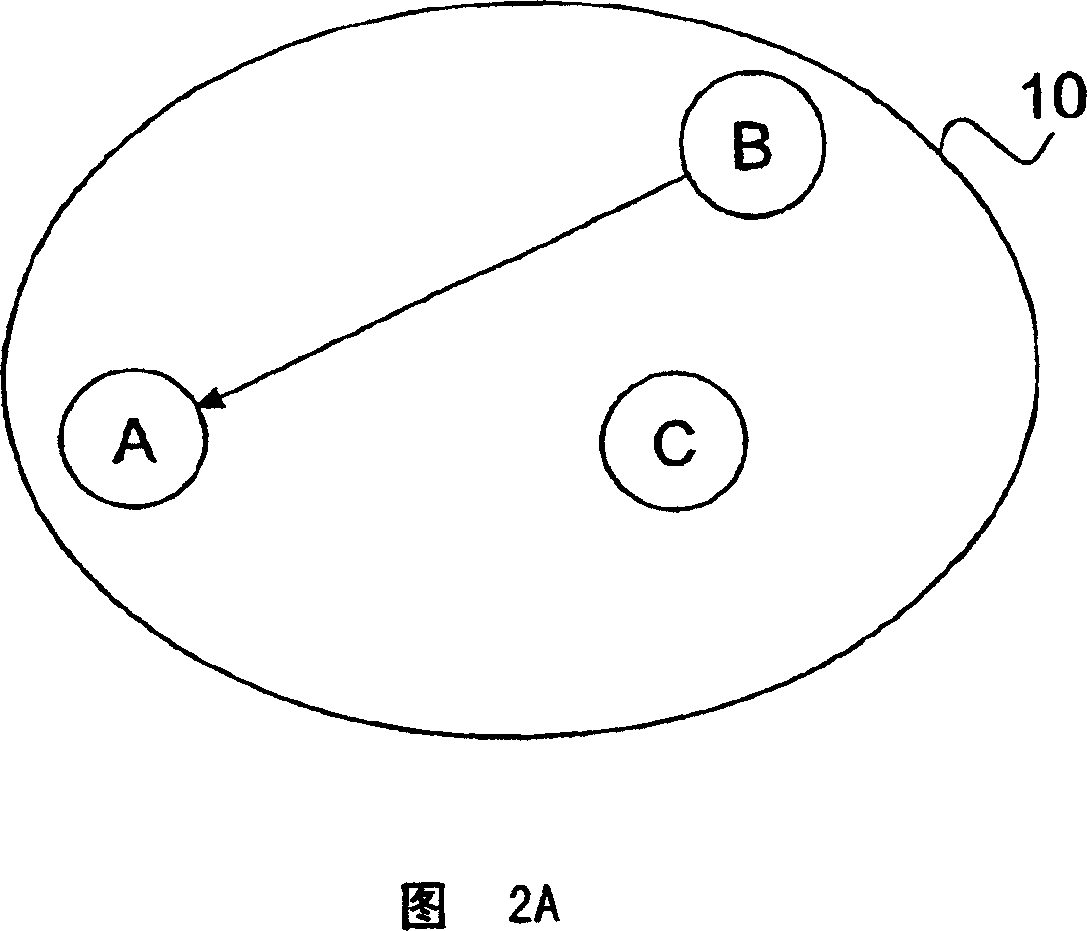
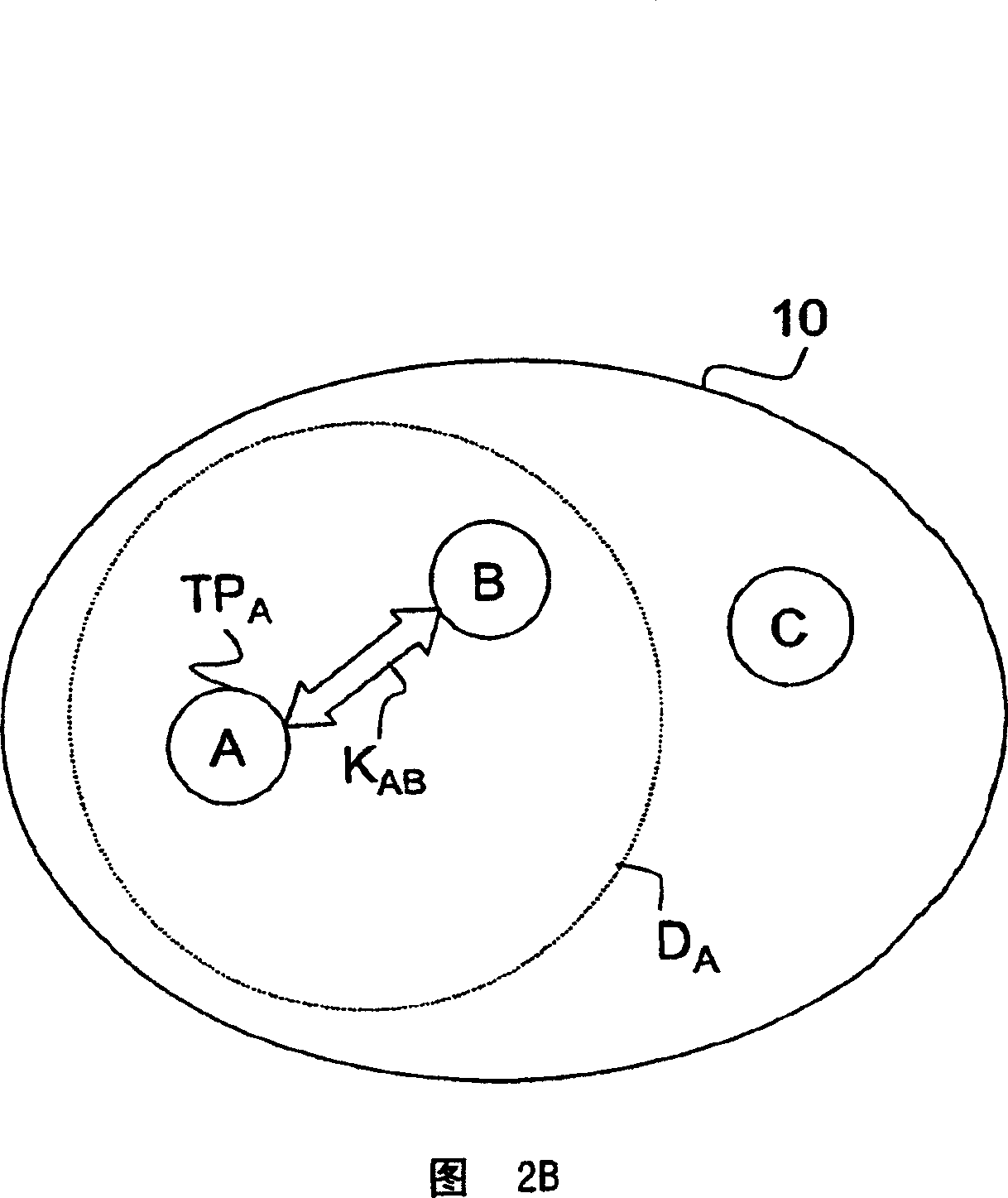
[0024] Referring to FIG. 1, each short-range ad hoc wireless network 10 includes mobile nodes (A, B, . . . , Z) owned by a single management entity, such as a hospital, business, factory, etc. Typically, each ad hoc network 10 comprises ten to twenty ad hoc nodes (A, B, . . . , Z) supported by a free network infrastructure connected by wireless one-hop links. Preferably, the mobile nodes (A, B, . . . , Z) comprise physiological monitoring devices, controlled medication management devices, PDA-like devices, embedded computing systems, or similar devices with moderate computing capabilities. Preferably, many independent short-range ad hoc networks 10 are randomly dispersed in a very limited area of use. The wireless coverage area of each ad hoc network 10 is up to 40 meters, such an extension often exceeds the application area. For example, a network may include nodes for individual physiological monitors, medication management devices, computer-based patient IDs, attending...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com