System and method for traversing firewalls, NATs, and proxies with rich media communications and other application protocols
a technology of rich media communication and application protocol, applied in the field of communication network firewalls, nats and proxies, can solve the problems of blocking or restricting unauthorized incoming data and unauthorized incoming requests from devices, external devices may not be able to identify or communicate with a specific local device, and potential security threats to any computer publicly accessible on the intern
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] Reference will now be made in detail to the present embodiments of the invention, examples of which are illustrated in the accompanying drawings.
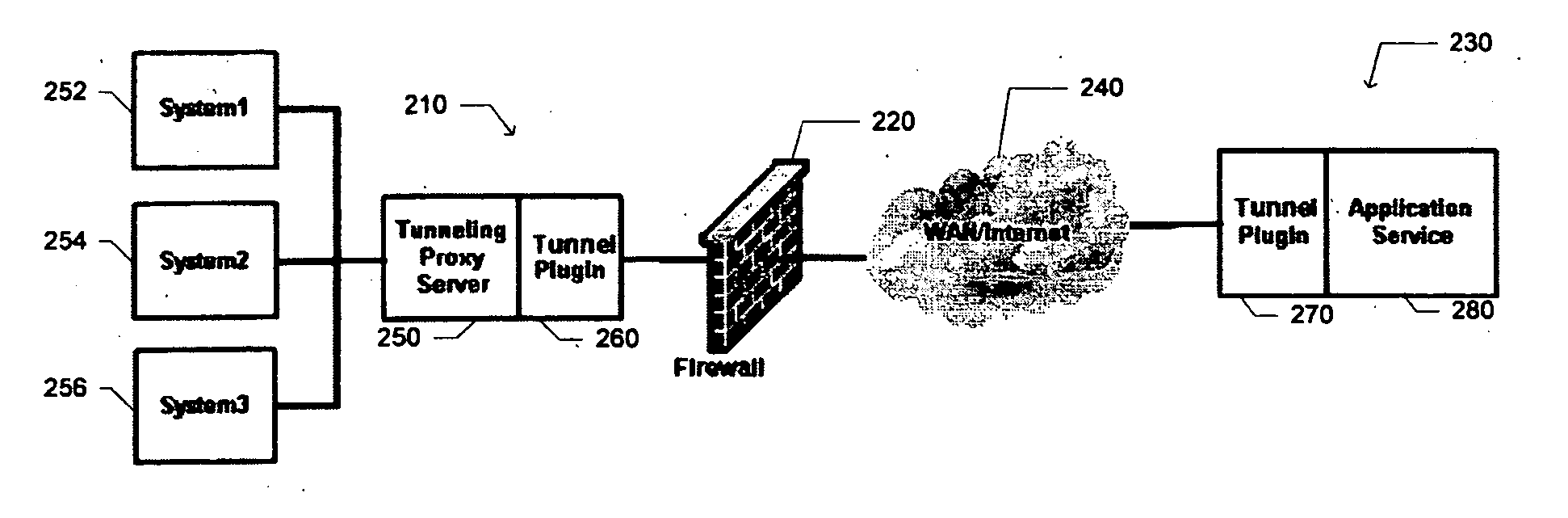
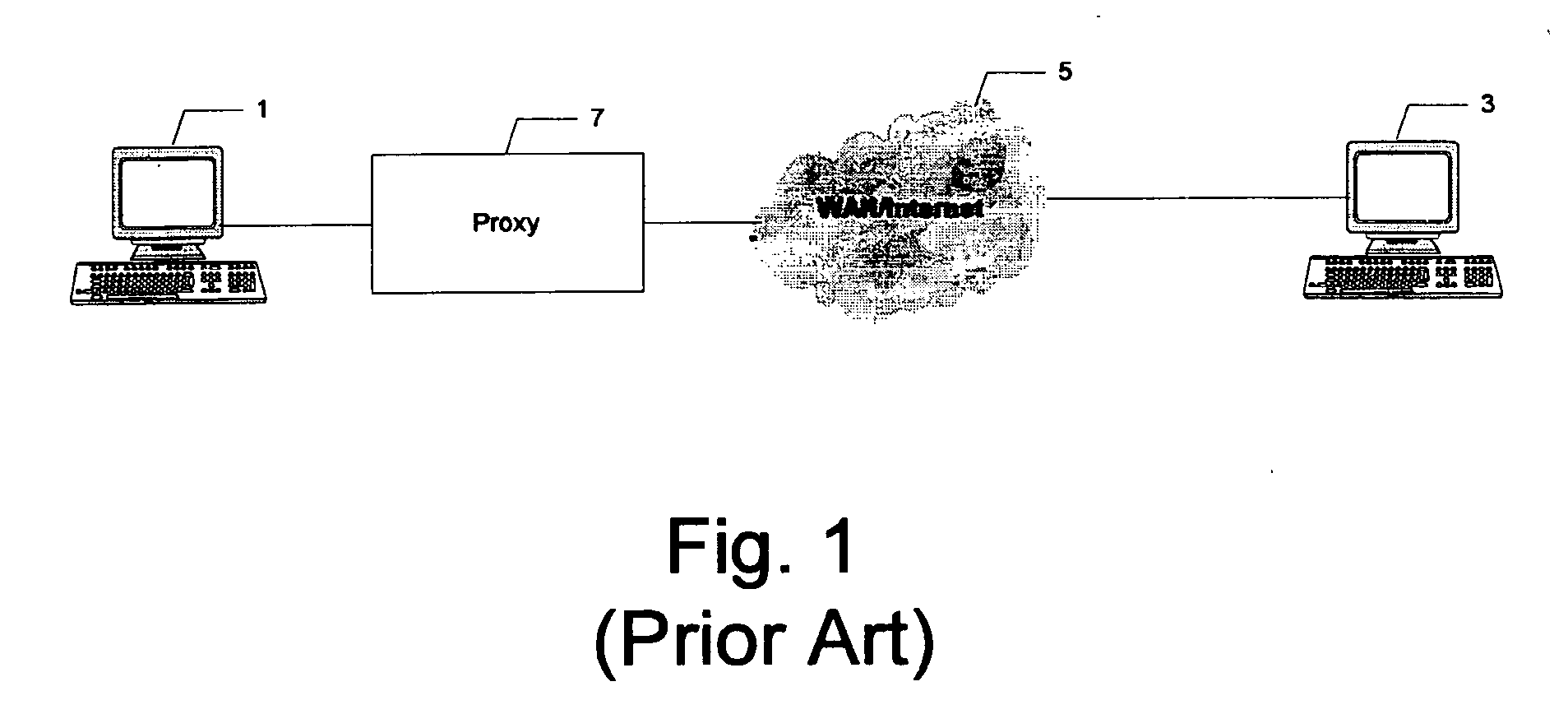
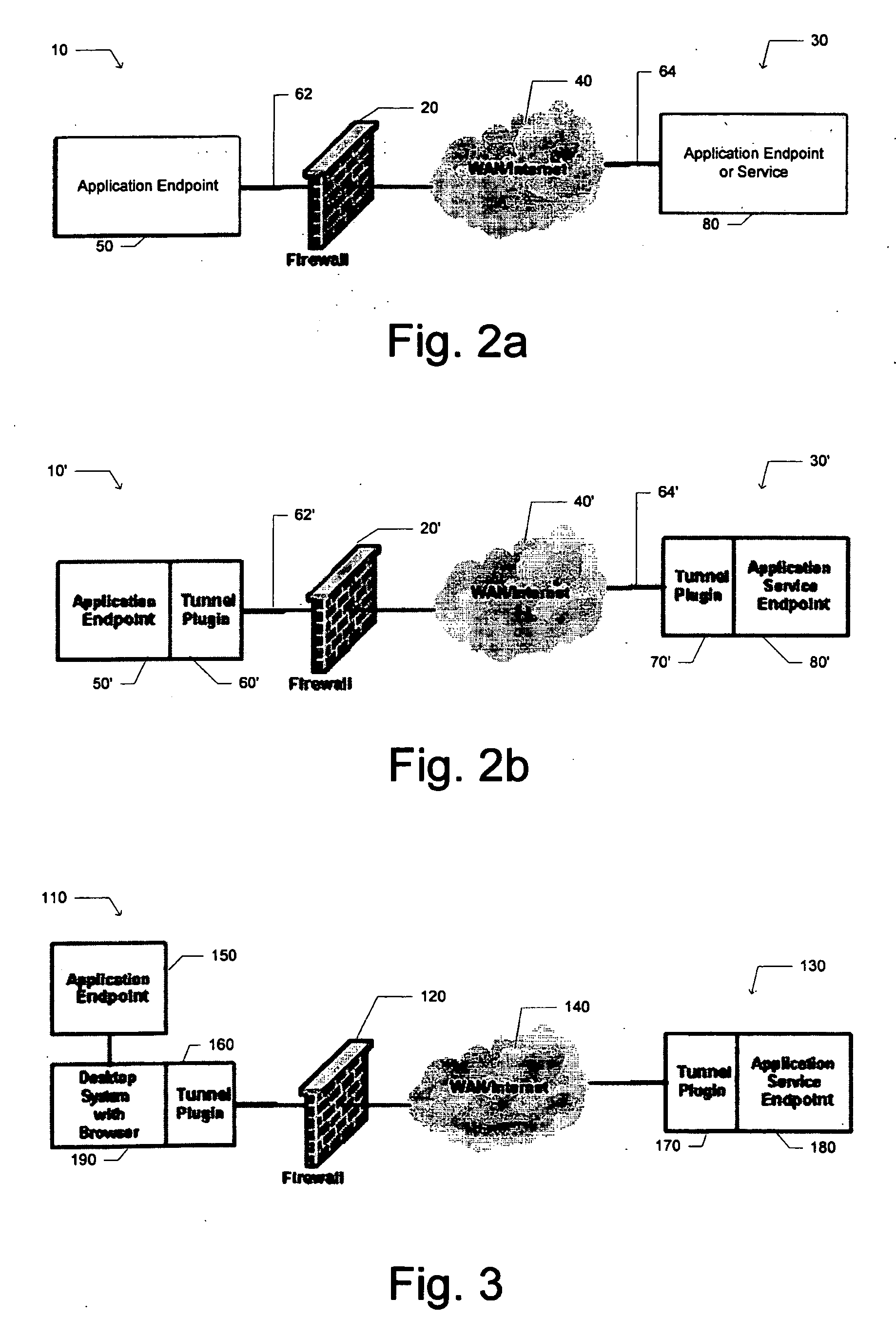
[0040] Reference to any specific operating system architecture (such as Microsoft® Windows™) is for demonstration purposes only as to how the present invention could be implemented. In addition, the terms ‘client’ and ‘server’ are for functional description only, since communication based on the tunneling approach disclosed supports bi-directional communication.
[0041] Network-based systems such as online conferences, online meetings, web seminars and application-sharing applications may depend on conditions associated with a client and server host system. Some components of a network-based application, including configuration information, may be previously installed on a client. Alternatively, the components and configuration information may be concurrently installed on the client as a network-based application is executing.
[0042]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com