E-mail certification service
a certification service and email technology, applied in the field of electronic mail, can solve the problems of reducing the usefulness of technology, becoming intrusion, and dangerous to blindly assume that received e-mail is legitimate,
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
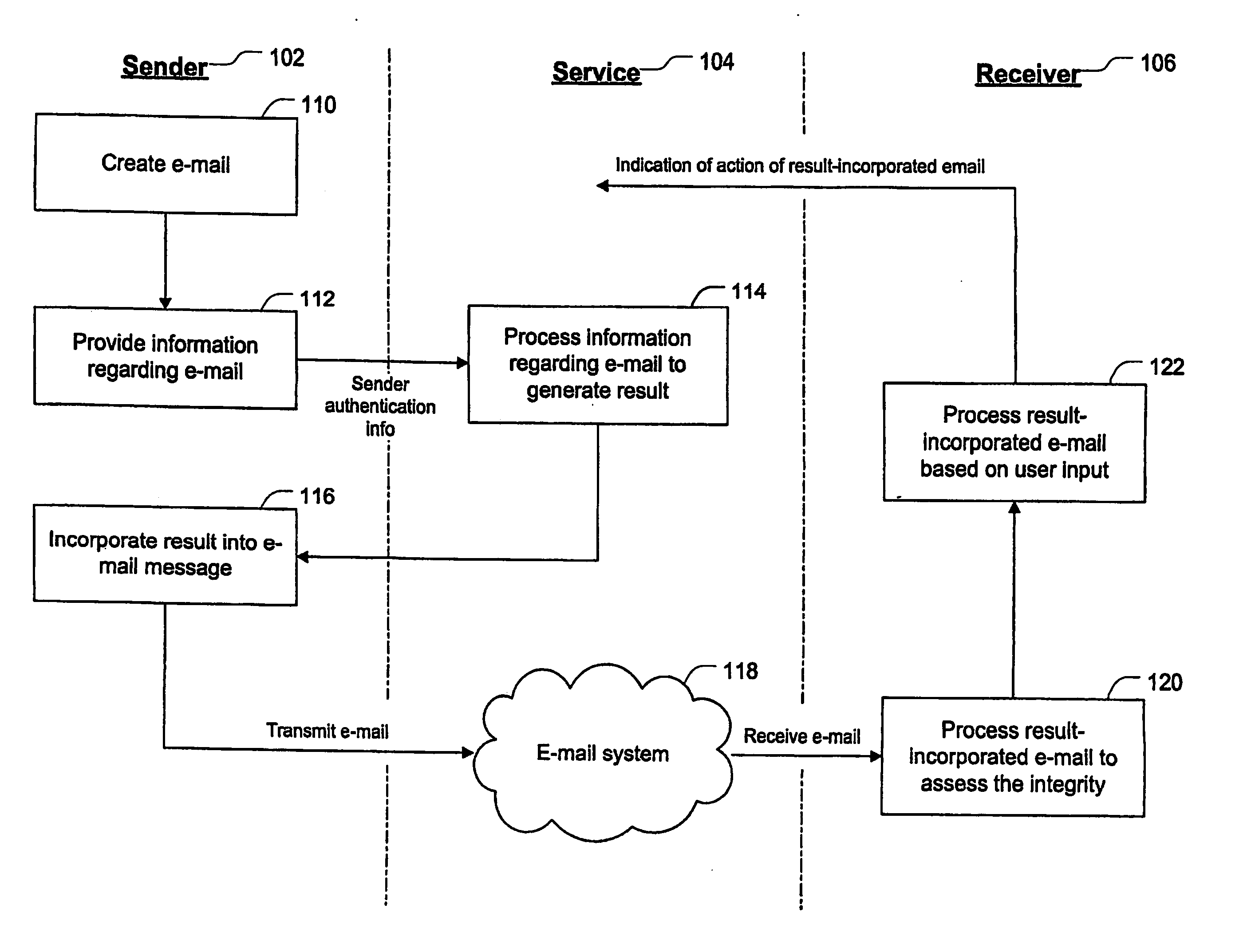
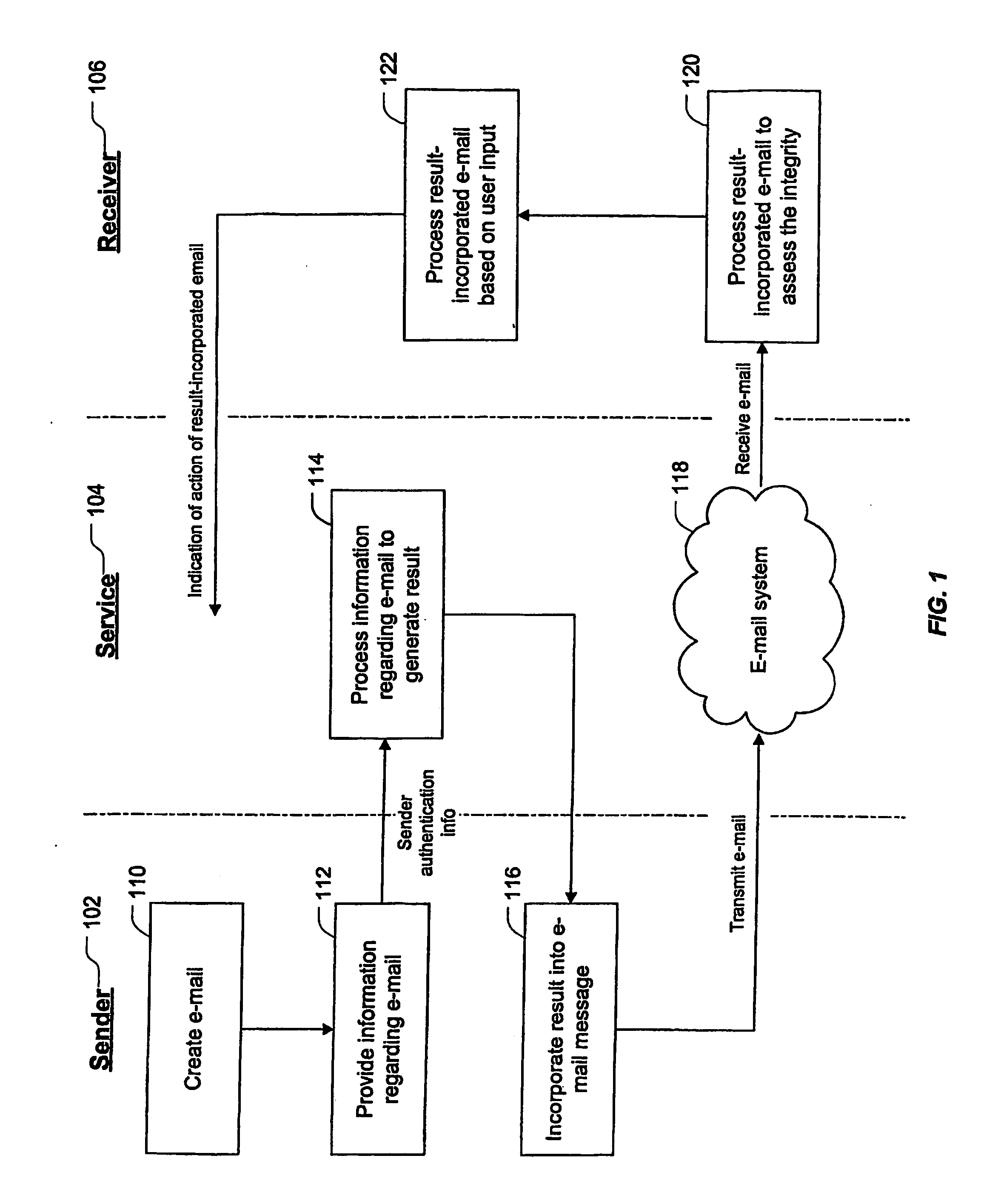
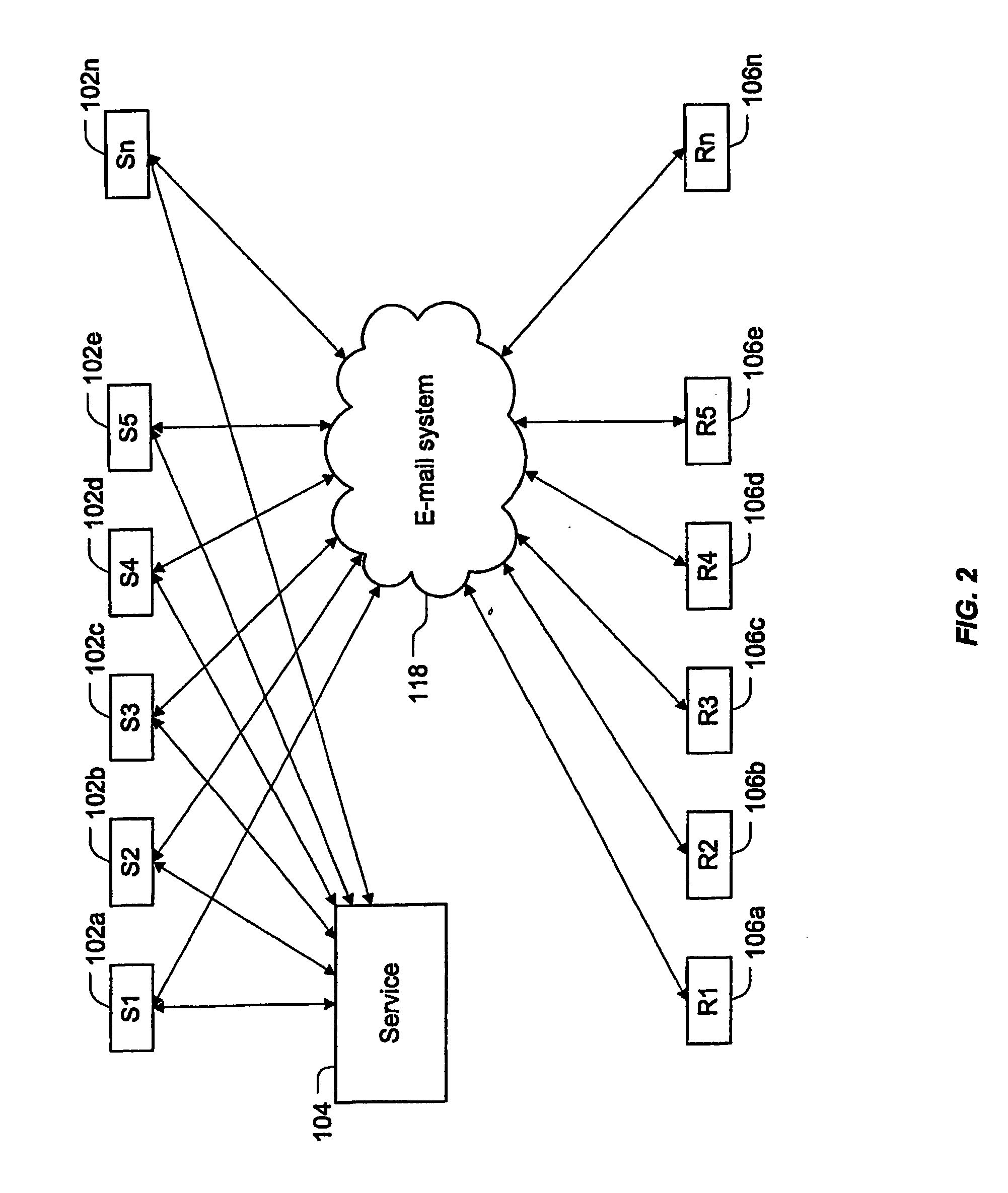
[0019]FIG. 1 illustrates a broad aspect of a method / system to handle an e-mail message such that a receiver of the e-mail message can assess the integrity of the e-mail message. FIG. 2 illustrates the architecture of the method / system. Referring to FIGS. 1 and 2, a plurality of senders 102a through 102n (referred to generically in FIG. 1 by the reference numeral 102) and a plurality of receivers 106athrough 106n(referred to generically in FIG. 1 by the reference numeral 106) are, in a basic form, present in any e-mail system. That is, any sender 102 can send an e-mail message to any receiver 106 via the e-mail system 118.
[0020] Referring specifically to FIG. 1, at step 110, an e-mail is created at the sender's side. 102 For example, the user authors an original e-mail message using standard e-mail client software (e.g., Outlook 2000 or Outlook 2003), including indicating a desired recipient of the message. At step 112, information regarding the e-mail is provided to the service 104...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com