Method and system for linking certificates to signed files
a technology of digital certificates and signed files, applied in the field of network computing security, can solve problems such as difficult inspection, lost digital certificates, accidental or even intentional removal, and methods that are not compatible with standard file formats such as images, video, audio or executable files
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
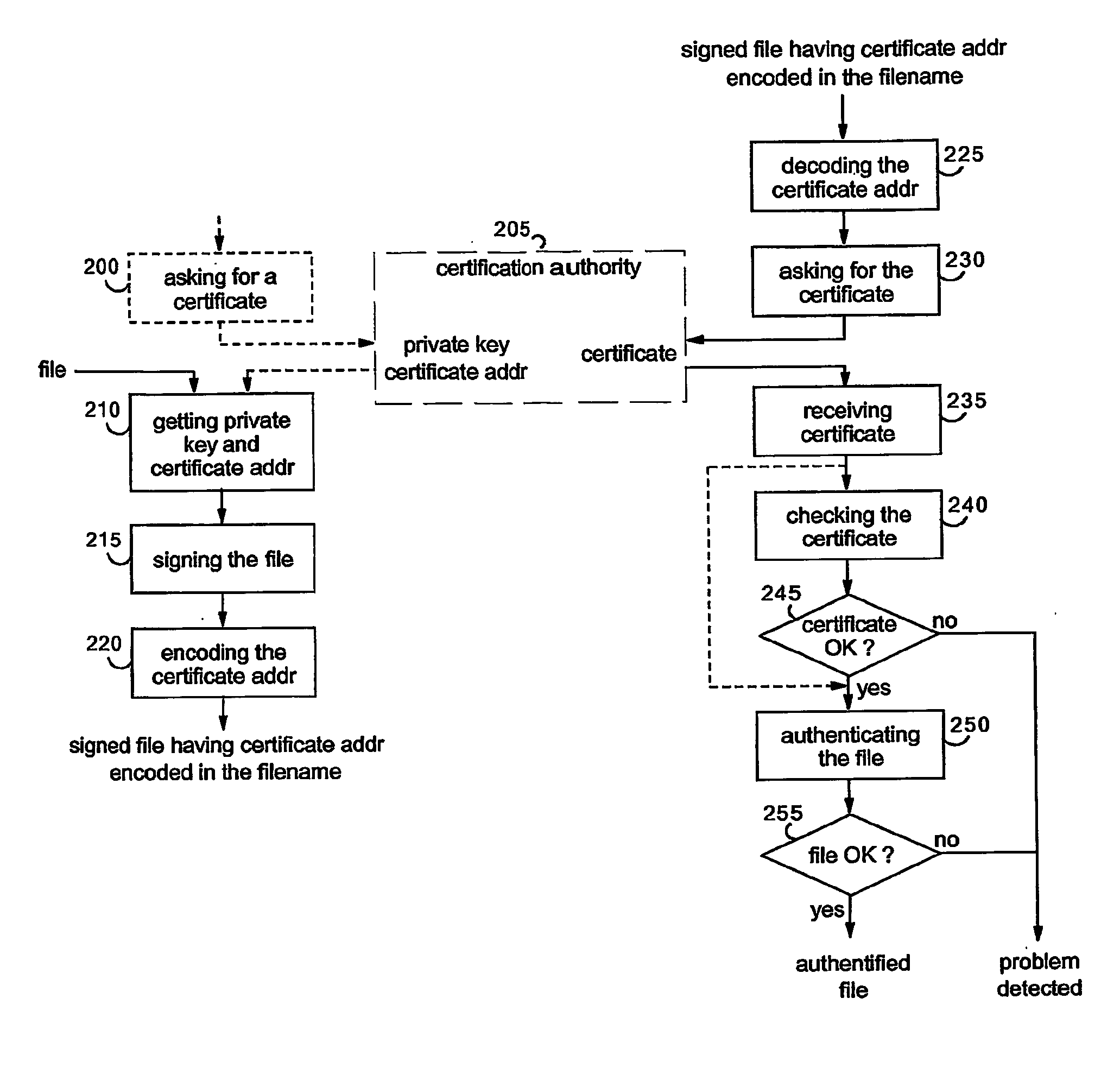
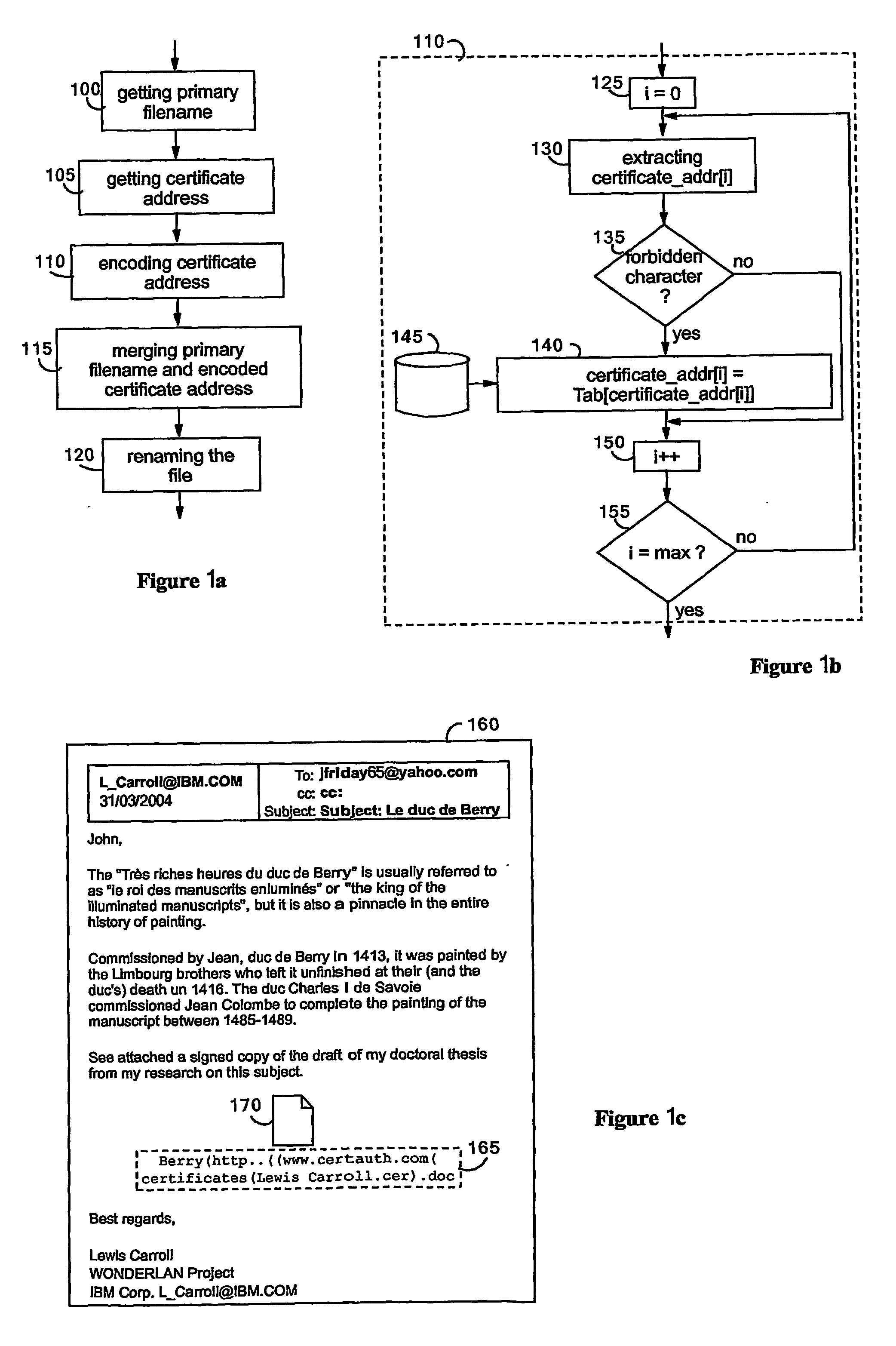
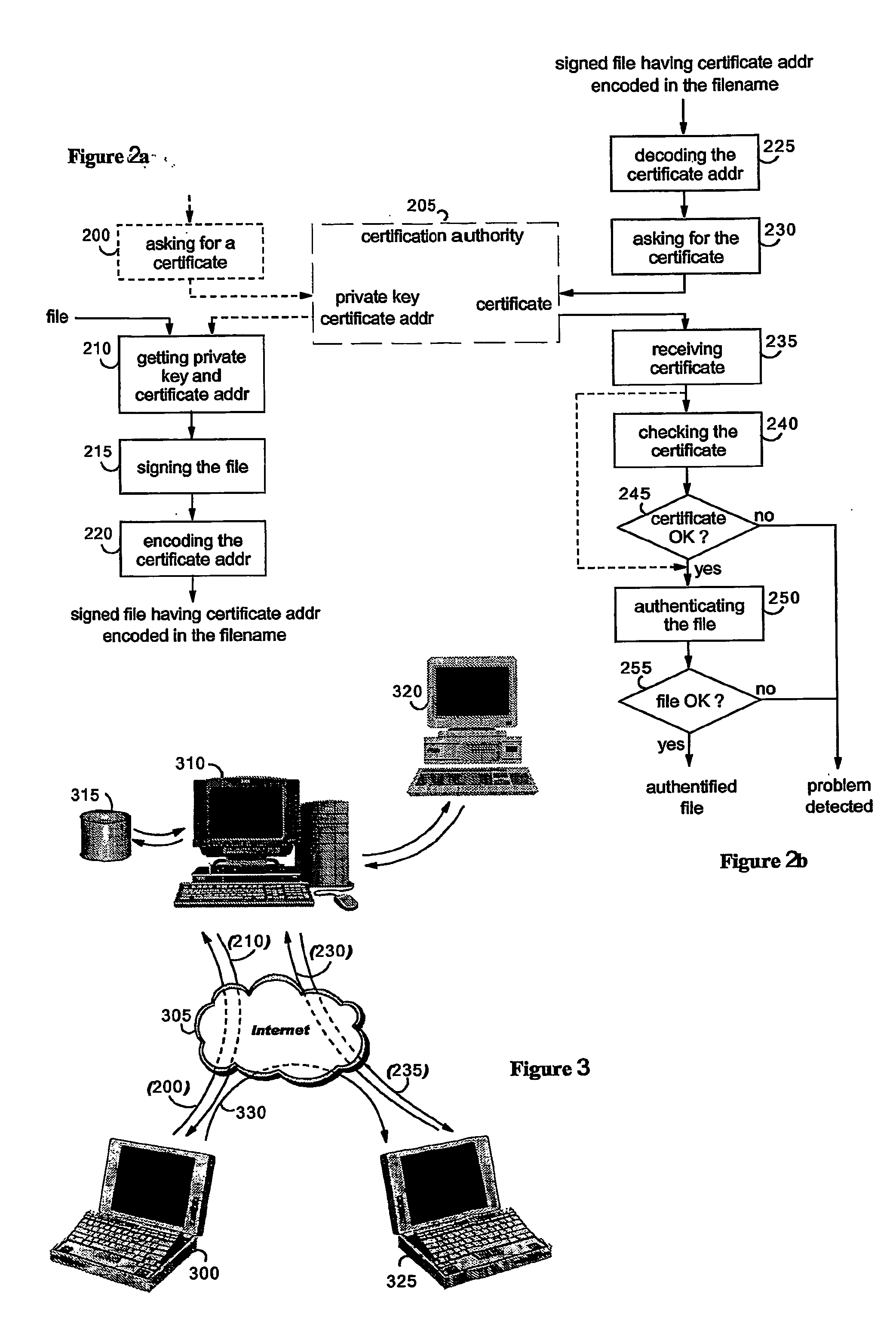
[0057] According to the invention, the filename of a file that is accessed locally or through a computer network is used to encode the address, or URL, from which the certificate that can be used to check the integrity and to verify the signature of the file can be accessed. A lexicography is determined so as to avoid particular characters that may be forbidden by the file system, e.g., “\” with Microsoft Windows system (Windows is a Trademark of Microsoft Corporation), and / or to encode the addresses so as to reduce their sizes. Addresses to be encoded may be of any forms e.g., local addresses, addresses in private networks or Internet addresses, however, for sake of illustration, the examples given in the following description are based on URL type of addresses. The address from which the certificate can be accessed can be encoded either when the file is transmitted from a server to the user system or when it is locally saved or transmitted to another system.
[0058]FIG. 1 illustrat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com