Program instrumentation method and apparatus for constraining the behavior of embedded script in documents
a script and embedded script technology, applied in the field of computer programming, can solve the problems of difficult control from the user's point of view, javascript code from attacker.com will not be able to read a cookie set by mybank.com, and annoying pop-ups of undesirable contents
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
an example implementation
Architecture
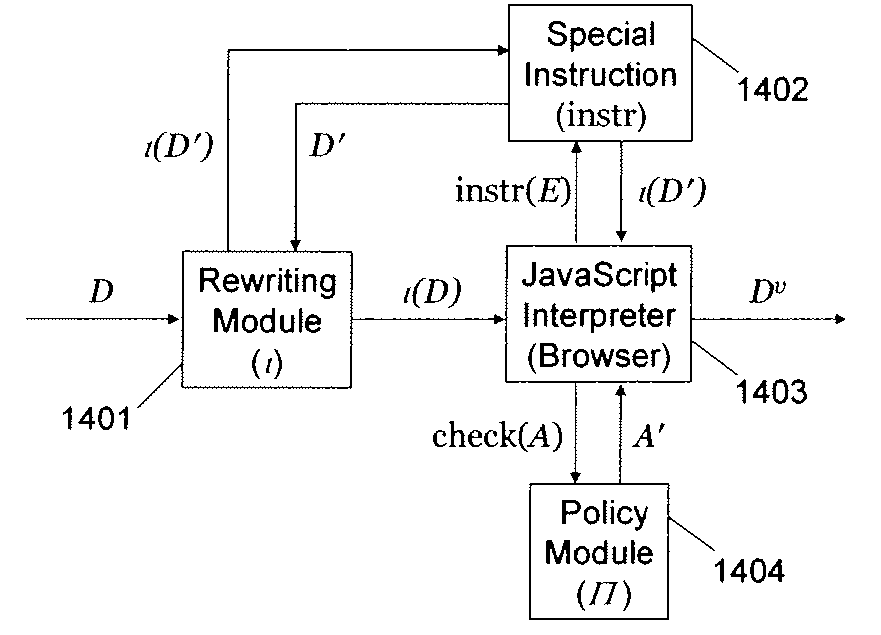
[0119]FIG. 14 illustrates an example of an implementation architecture. Each of the modules may comprise hardware (circuitry, dedicated logic, etc.), software (such as is run on a general purpose computer system or a dedicated machine), or a combination of both.
[0120] Referring to FIG. 14, the implementation may extend a browser with three small modules—module 1401 for the syntactic code rewriting (ι), module 1402 for interpreting the special instruction (instr), and module 1404 for implementing the security policy (Π). In one embodiment, a browser 1403 does not interpret a document D directly. Instead, browser 1403 interprets a rewritten version ι(D) produced by the rewriting module. Upon a special instruction instr(E), the implementation of instr evaluates the expression E and sends the result document D′ through rewriting module 1401. The result of the rewriting ι(D′) is directed back to browser 1403 for further interpretation. Upon a call to the policy interface che...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com