User-Defined Enablement Protocol
a user-defined and enablement protocol technology, applied in the direction of unauthorized memory use protection, digital storage, instruments, etc., can solve the problems of limiting the range and complexity of possible enablement protocols, making it more difficult for another person to learn the code by observation, and again simple for an unauthorised person to enter, etc., to achieve the effect of small display
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047]FIGS. 1 and 2 provide illustrations of prior art functionality in conventional devices.
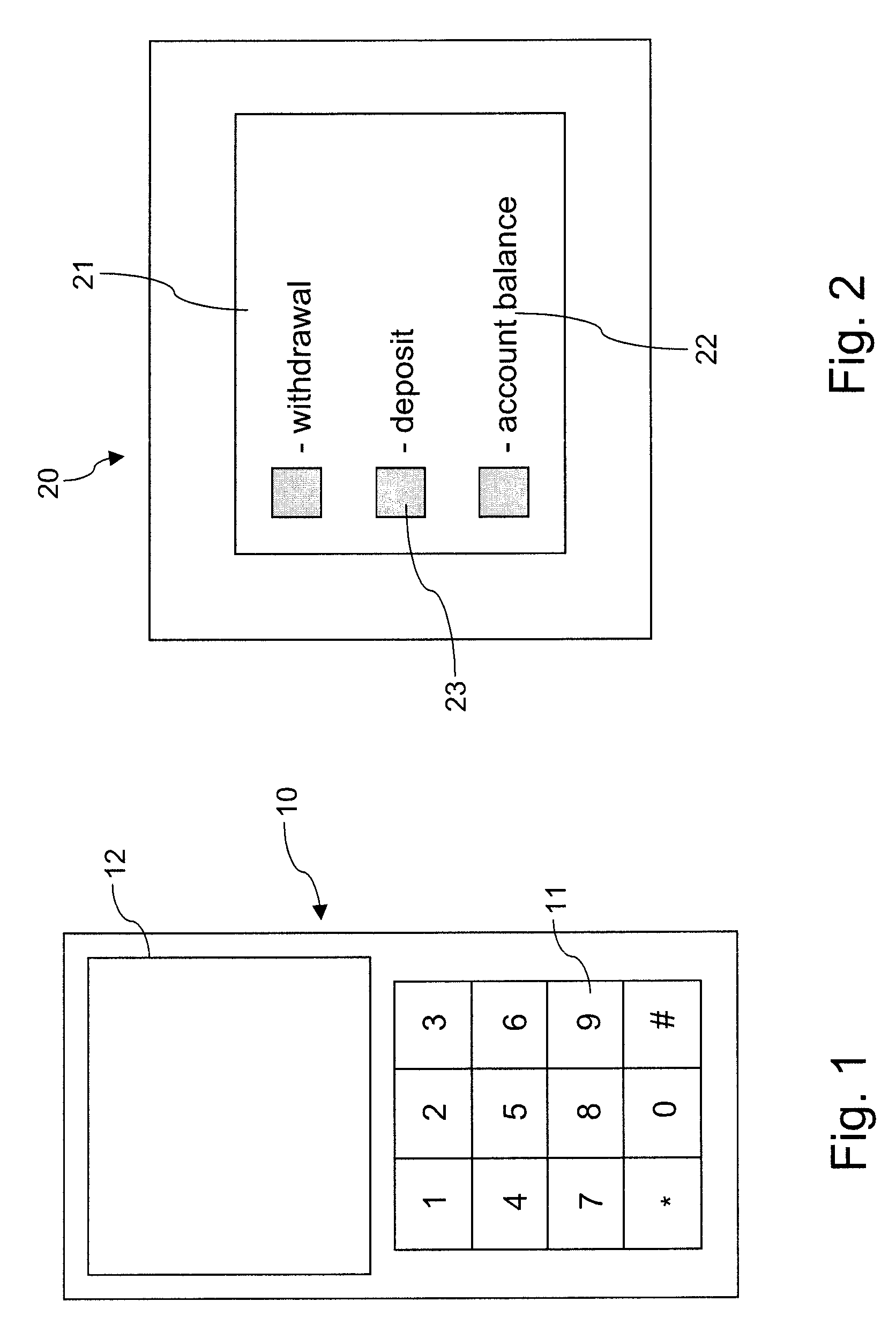
[0048]FIG. 1 shows a mobile phone 10 with an alphanumeric keypad 11 and a display 12. In many instances the mobile phone can only be enabled when a user-defined security code is entered via the alphanumeric keypad 11. Alternatively the alphanumeric keypad may be provided on a touch-sensitive display (i.e. a touch screen) but once again the conventional device comprises a pre-defined arrangement of the enablement protocol such that if an unauthorised user were aware of the code e.g. 123, they could enable the device simply by engaging the predefined locations for numerals 1, 2 and 3.
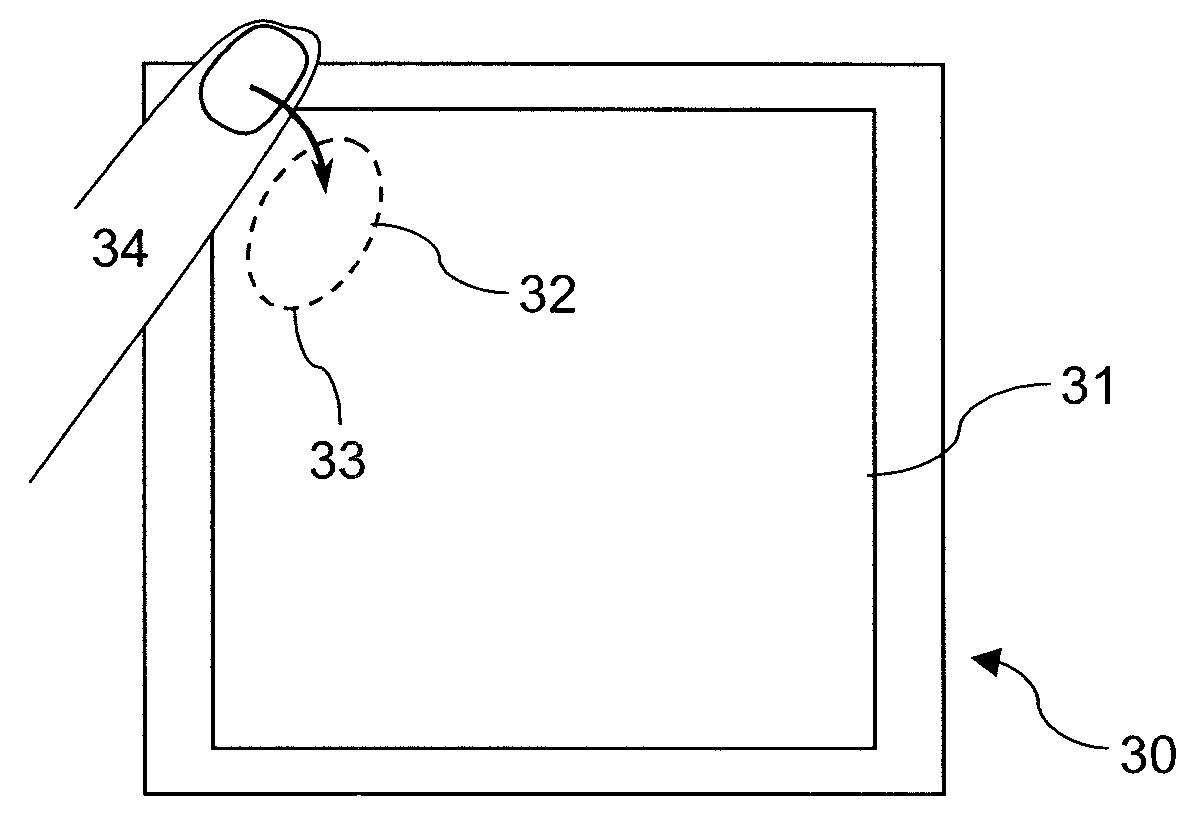
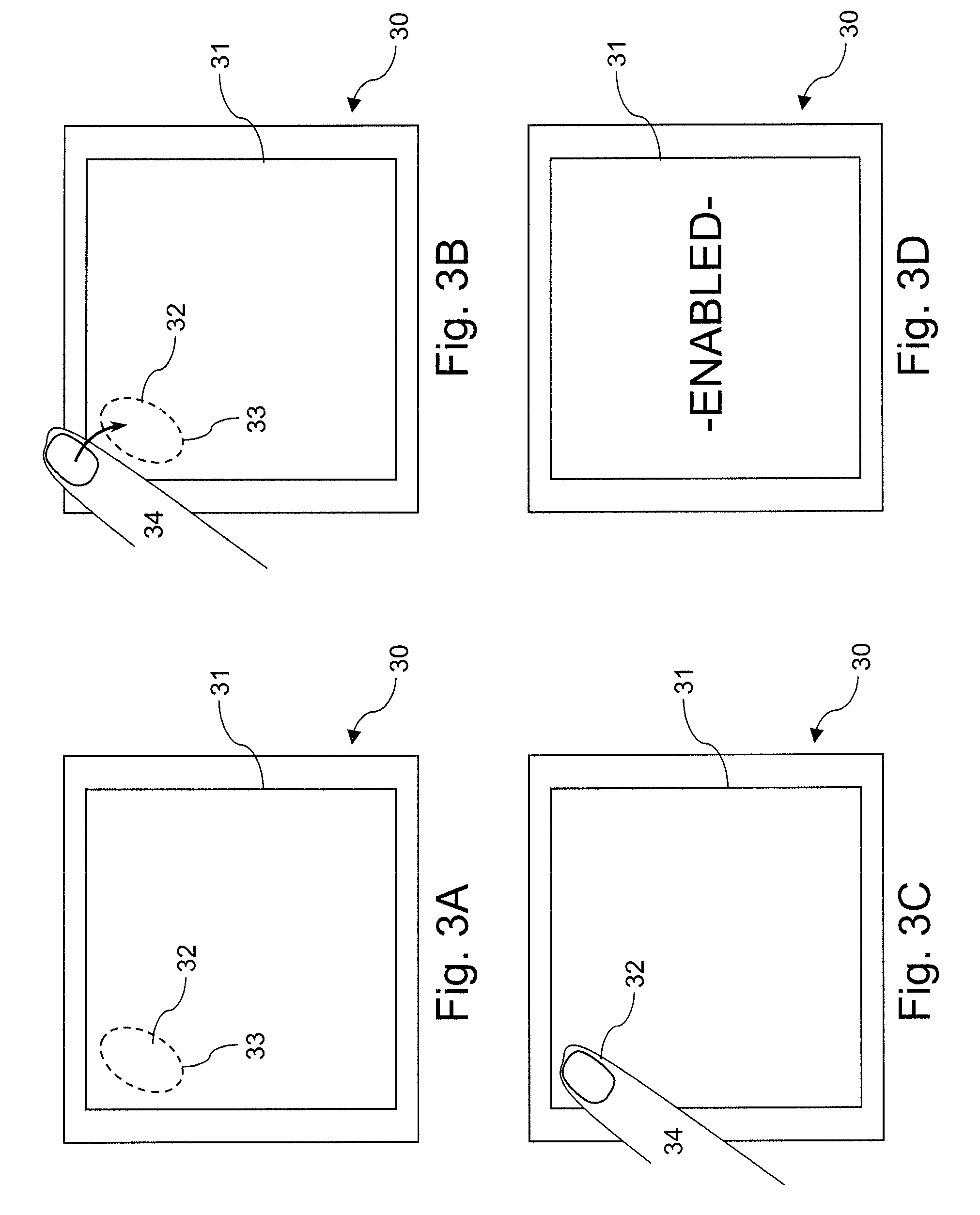
[0049]FIG. 2 is an illustration of an automatic teller machine 20 with a touch sensitive display 21. This technology is similar to the mobile phone in FIG. 1, and in this instance various functions and spatial locations for enabling those functions are clearly defined on the display. The display includes indicia 2...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com