Method and system for containment of networked application client software by explicit human input
a networked application and client software technology, applied in the field of computer systems, can solve the problems of difficult automation of user responses by software, and much more difficult to reliably automate user responses for multiple arbitrary dialogues, so as to prevent the spread of malicious service usage attempts, reduce or eliminate the spread of malicious software
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
first embodiment
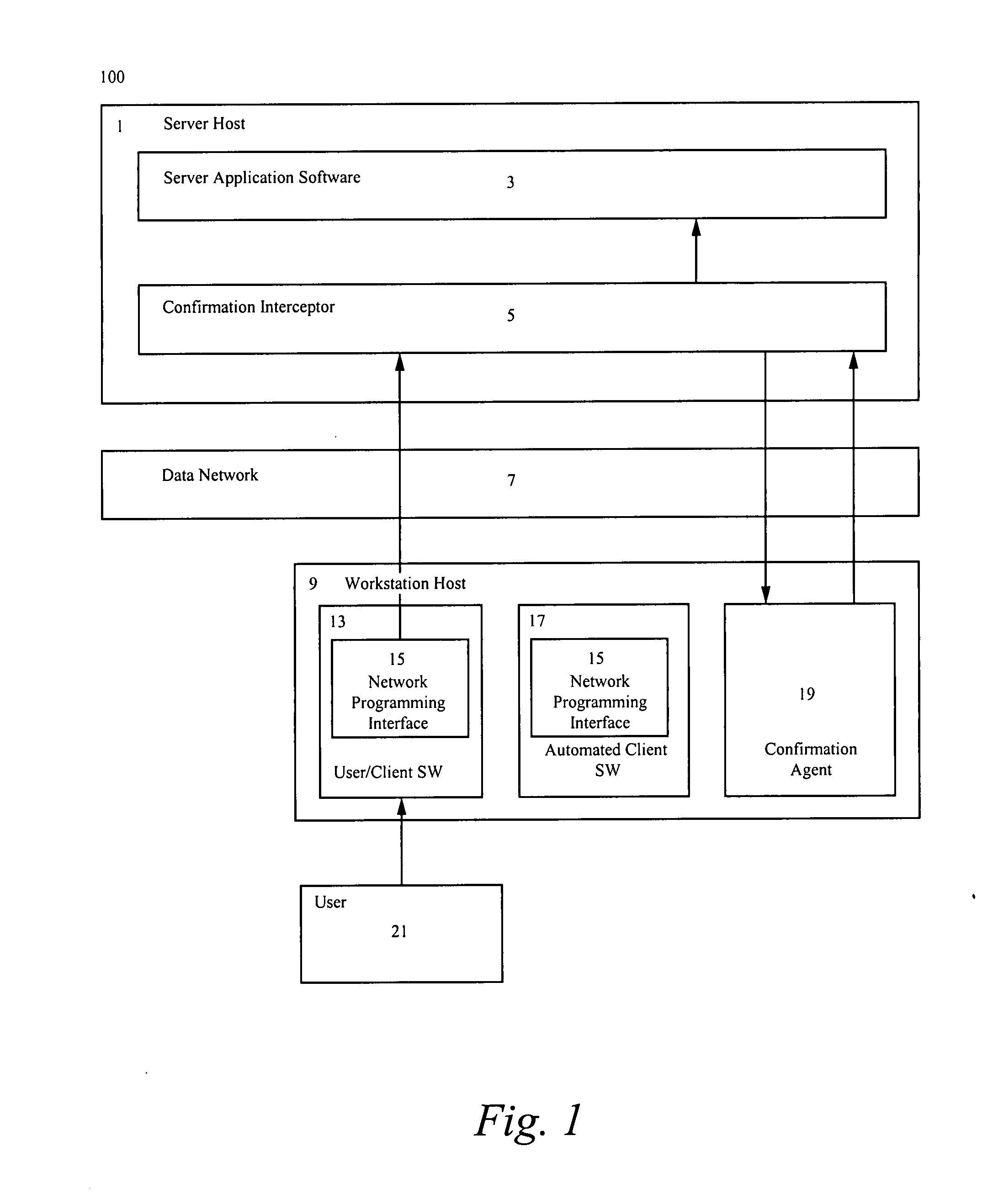
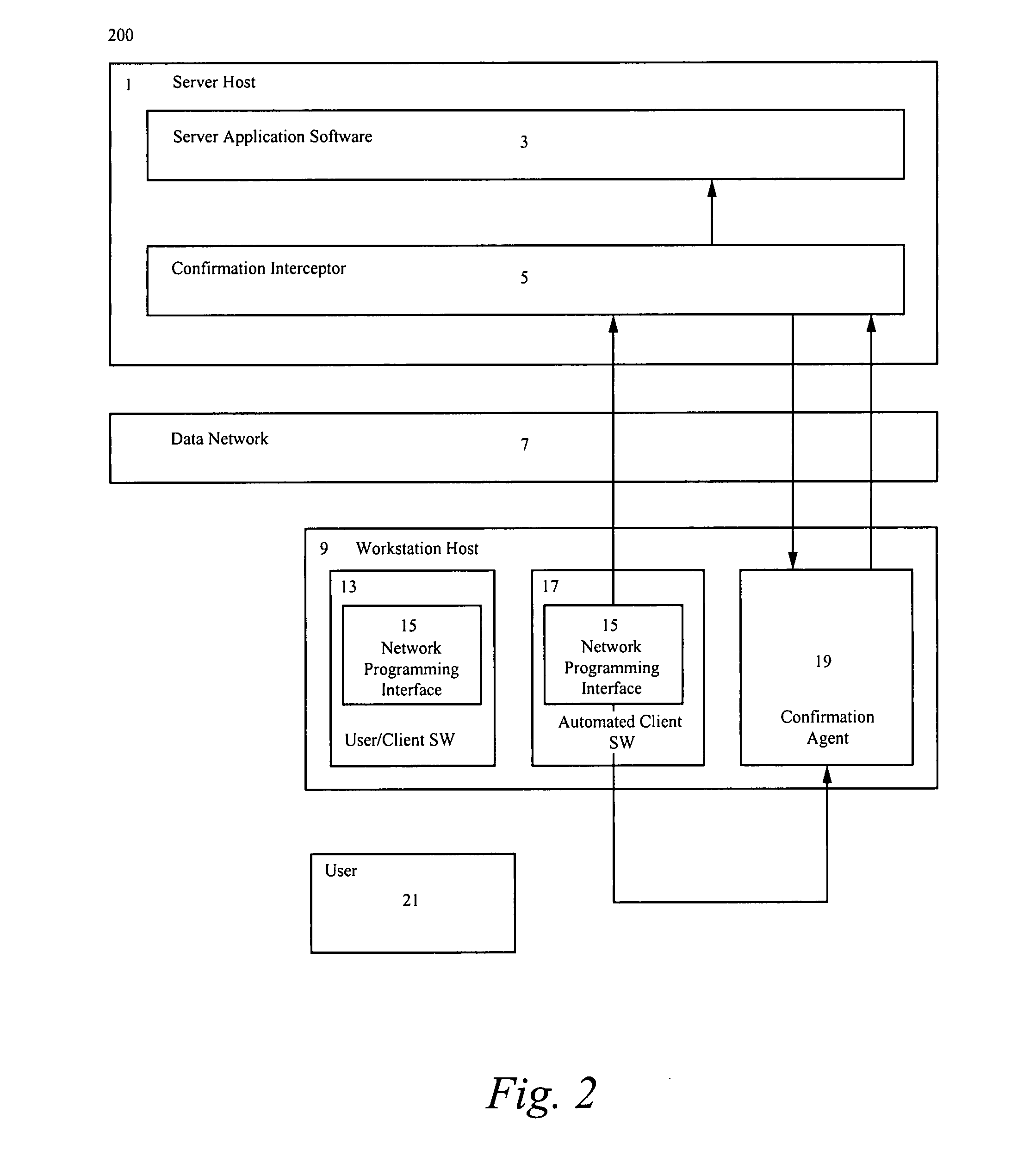
[0019]FIG. 1 illustrates a block diagram 100 in accordance to the present invention. Block diagram 100 comprises: a server host denoted 1, a data network denoted 7, a workstation host denoted 9, and a user denoted 21. The server host 1 further comprises server application software denoted 3 and a confirmation interceptor denoted 5. The workstation host 9 further comprises: user / client software denoted 13, automated client software denoted 17, and a confirmation agent denoted 19. The user / client software 13 and the automated client software 17 each in turn comprise a network programming interface denoted 15.
[0020]Furthermore, the server host 1 is herein defined as a computer that is running a service that may be used directly or indirectly by the user 21 via user / client software 13. The data network 7 is herein defined as an electronic medium used for communication between two or more computers, including communication between the server host 1 and the workstation host 9. The worksta...
second embodiment
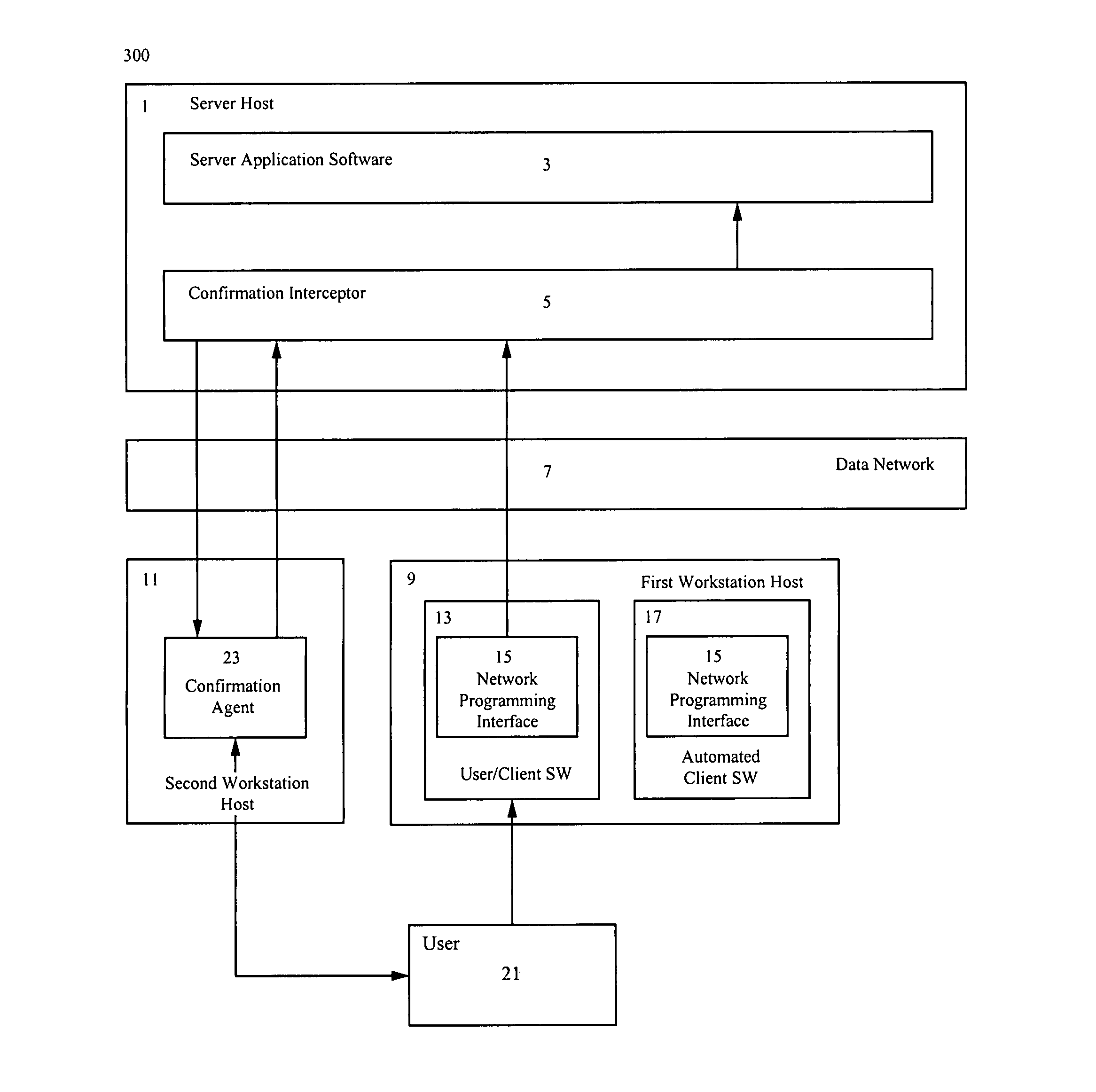
[0033]FIG. 3 is a block diagram 300 in accordance to the present invention. Block diagram 300 comprises: a server host denoted 1, a data network denoted 7, a first workstation host denoted 9, a second workstation host denoted 11, and a user denoted 21. The server host 1 further comprises server application software denoted 3 and a confirmation interceptor denoted 5. The first workstation host 9 further comprises: user / client software denoted 13, and automated client software denoted 17. The second workstation host 11 further comprises a confirmation agent 23. The user / client software 13 and the automated client software 17 each in turn comprise a network programming interface denoted 15.
[0034]As shown in FIG. 3, the server host 1, the server application software 3, the confirmation interceptor 5, the user / client software 13, the automated client software 17, the network programming interface 15, and the user 21 are substantially the same as they are illustrated and described in FIG....
third embodiment
[0035]FIG. 4 is a block diagram 400 in accordance to the present invention. Block diagram 400 comprises: a server host denoted 1, a data network denoted 7, a workstation host denoted 9, a communication device denoted 27 comprising a confirmation agent, and a user denoted 21. The server host 1 further comprises server application software denoted 3 and a confirmation interceptor denoted 5. The workstation host 9 further comprises: user / client software denoted 13, and automated client software denoted 17. The user / client software 13 and the automated client software 17 each in turn comprise a network programming interface denoted 15.
[0036]As shown in FIG. 4, the server host 1, the server application software 3, the confirmation interceptor 5, the user / client software 13, the automated client software 17, the network programming interface 15, and the user 21 are substantially the same as they are illustrated and described in FIG. 1. However, whereas the confirmation interceptor 5 is sh...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com