Application and network abuse detection with adaptive mitigation utilizing multi-modal intelligence data
a multi-modal intelligence and application network technology, applied in the field of network security, can solve problems such as inability to service legitimate requests, overwhelm a server, and inability to respond to additional requests
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
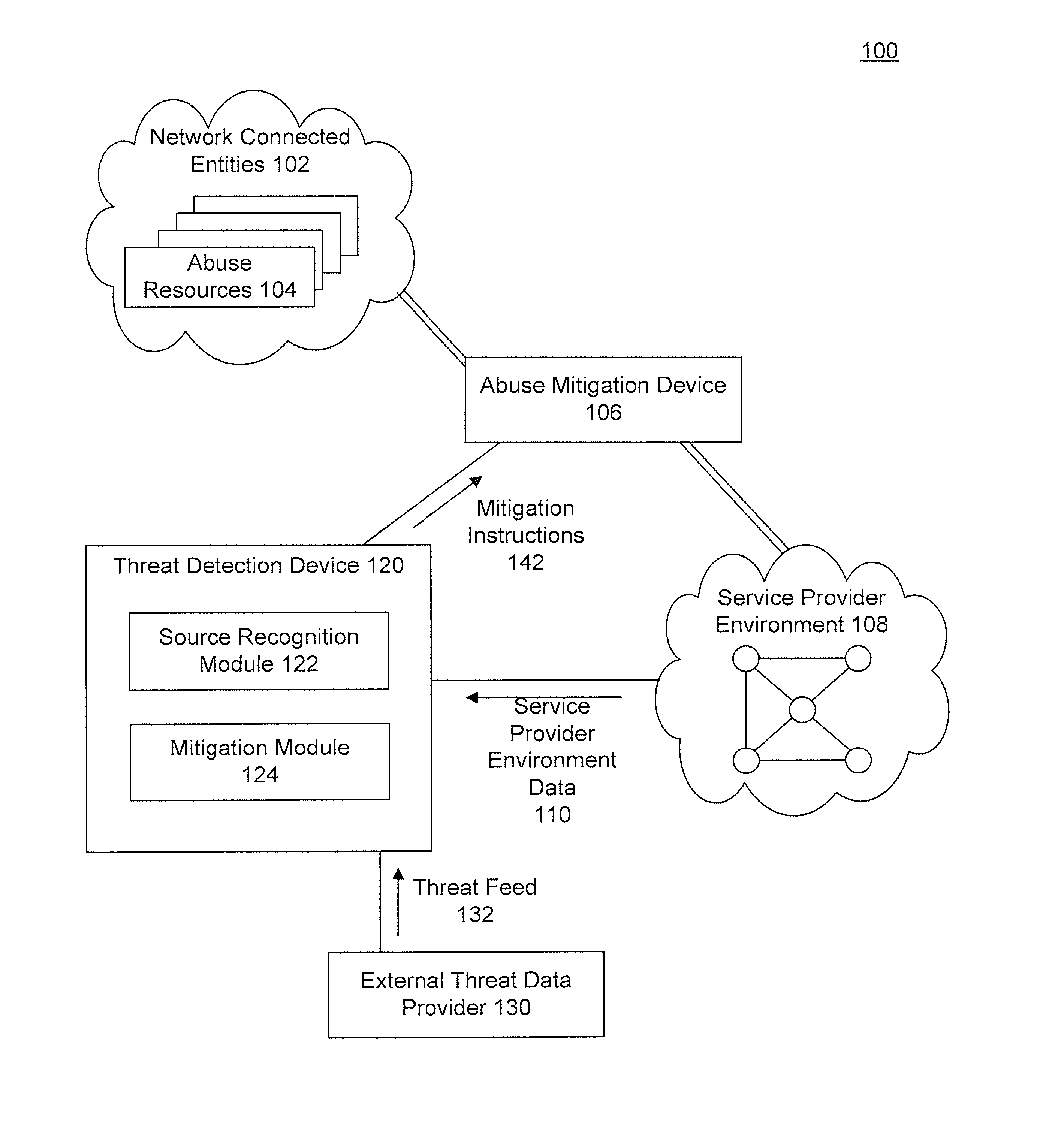
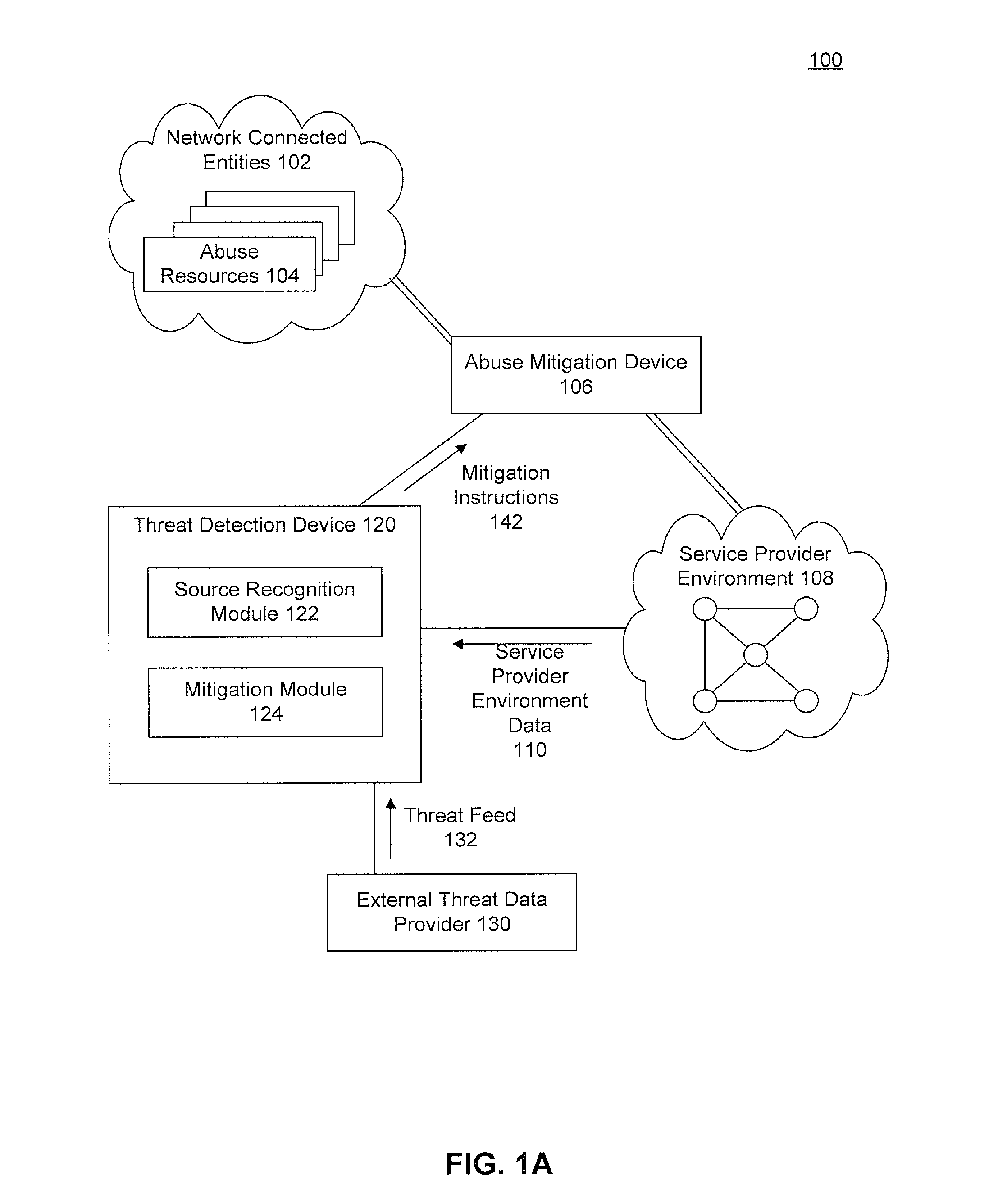
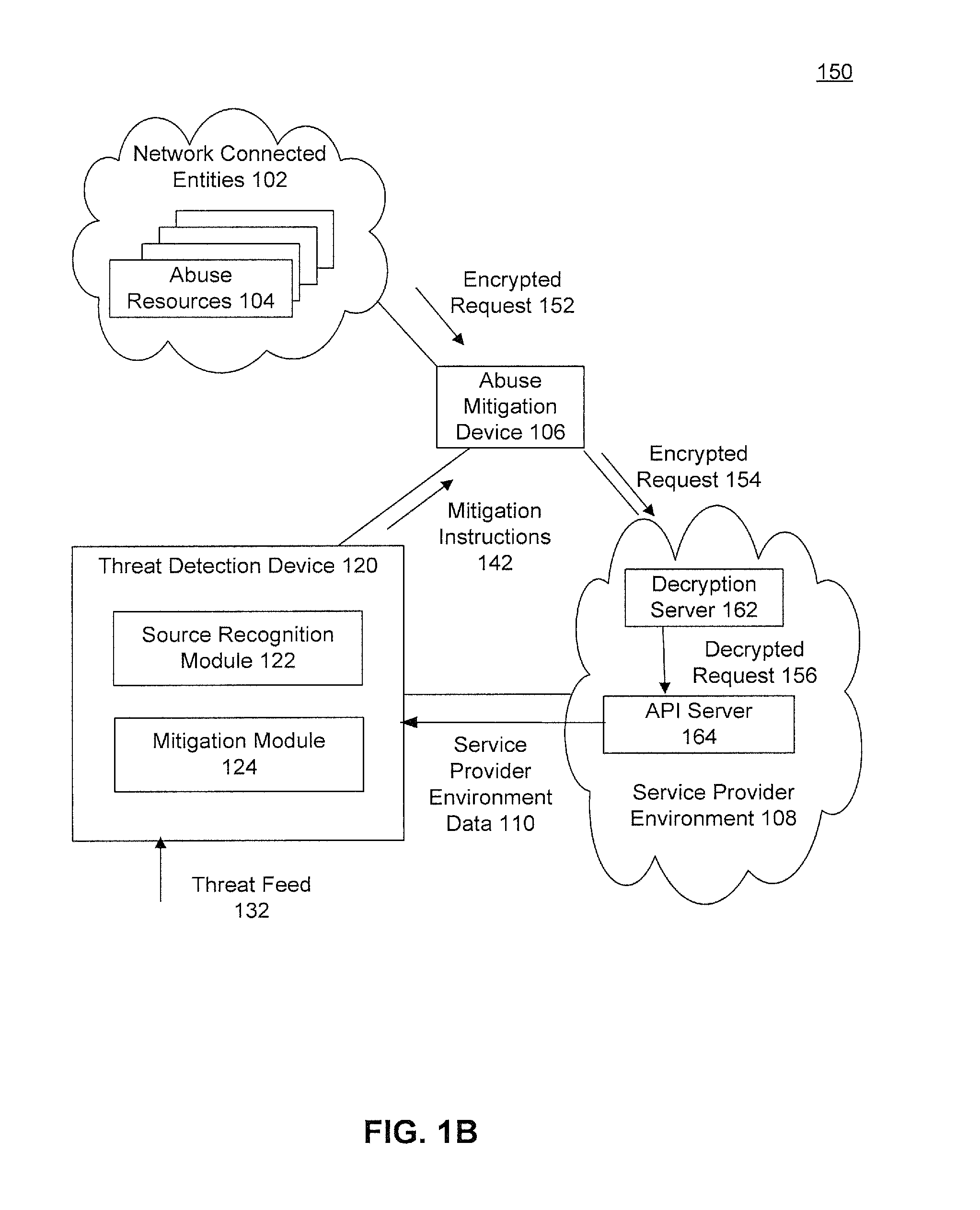
[0022]As mentioned above, operating in their own silos, existing network appliances may not effectively adapt and react to new denial of network and application abuse threats. To deal with this, embodiments use data from the service provider environments in concert with external threat data and / or historical data to identify malicious activity, even when using multiple vectors of abuse. More specifically, embodiments collect data on requests to the service provider's environment. They compare the requests against a set of heuristics to determine whether the different requests, being transmitted from or received from different entities, may, in fact be from a common abuse entity. The data is also evaluated against multiple data heuristics to determine whether the source(s) may be attempting or actively abusing the service. If application or network abuse is determined to be in progress, an operator may be alerted or steps to mitigate the abuse may be provided to the administrator or ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com