Behavior specification, finding main, and call graph visualizations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
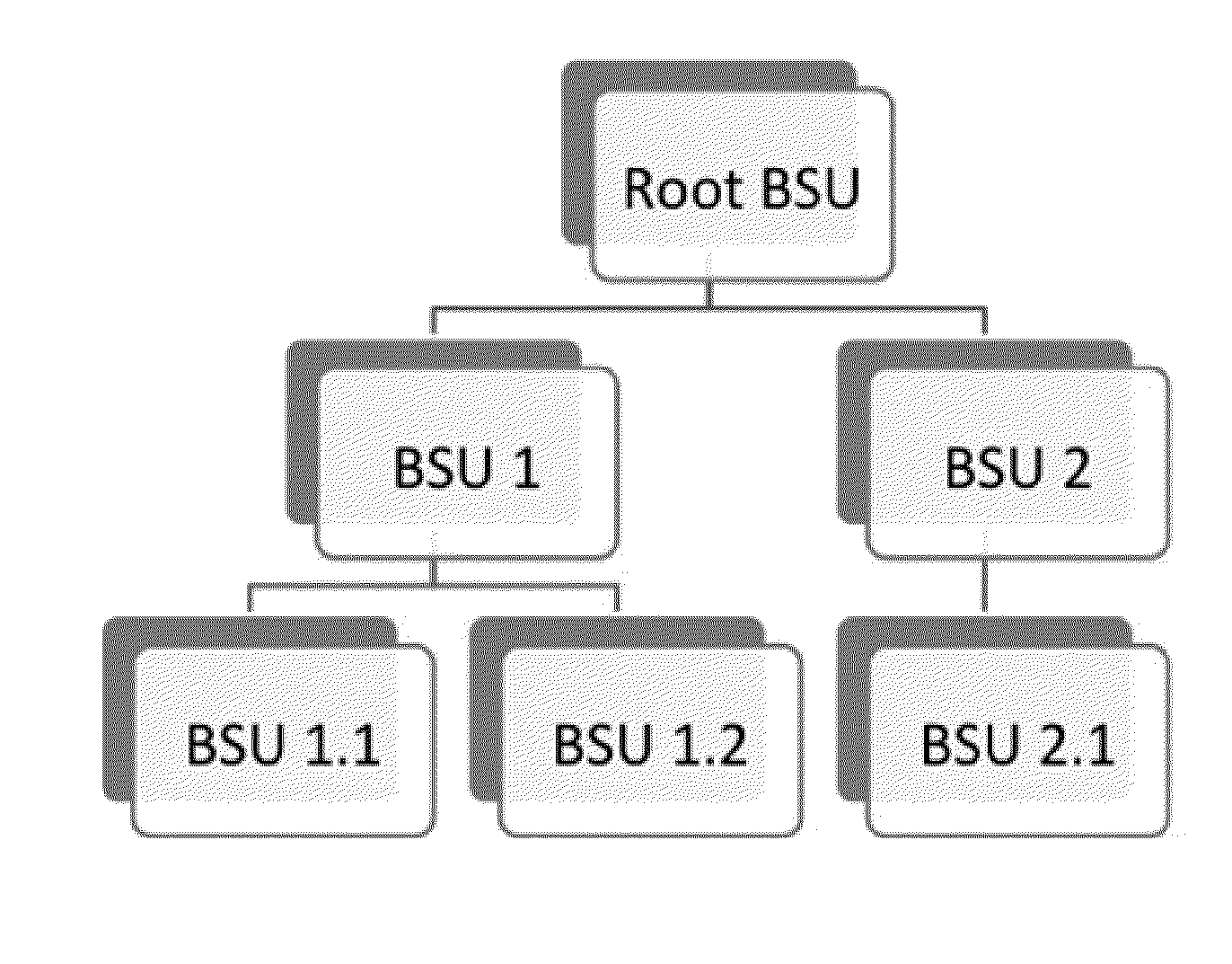
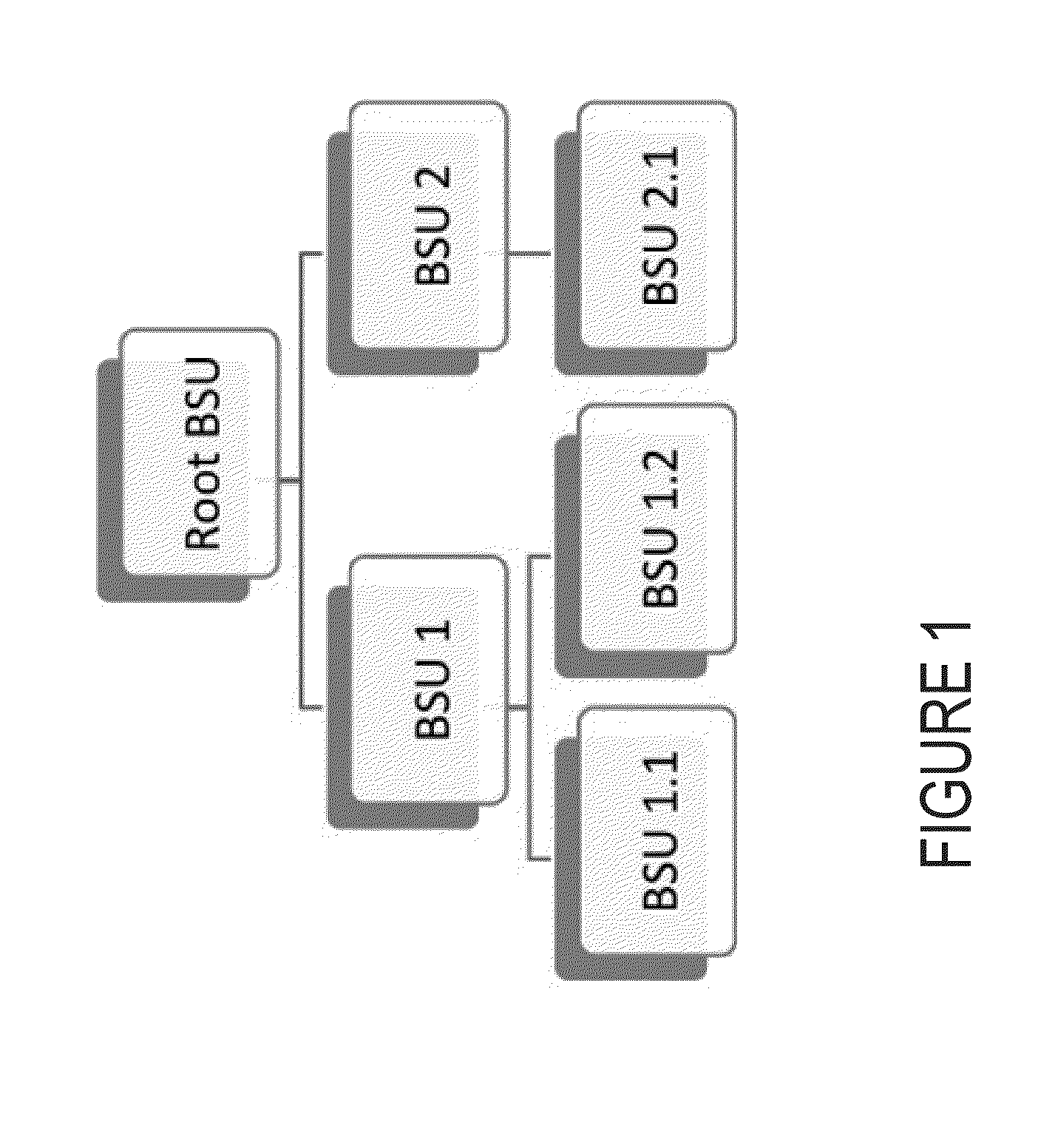
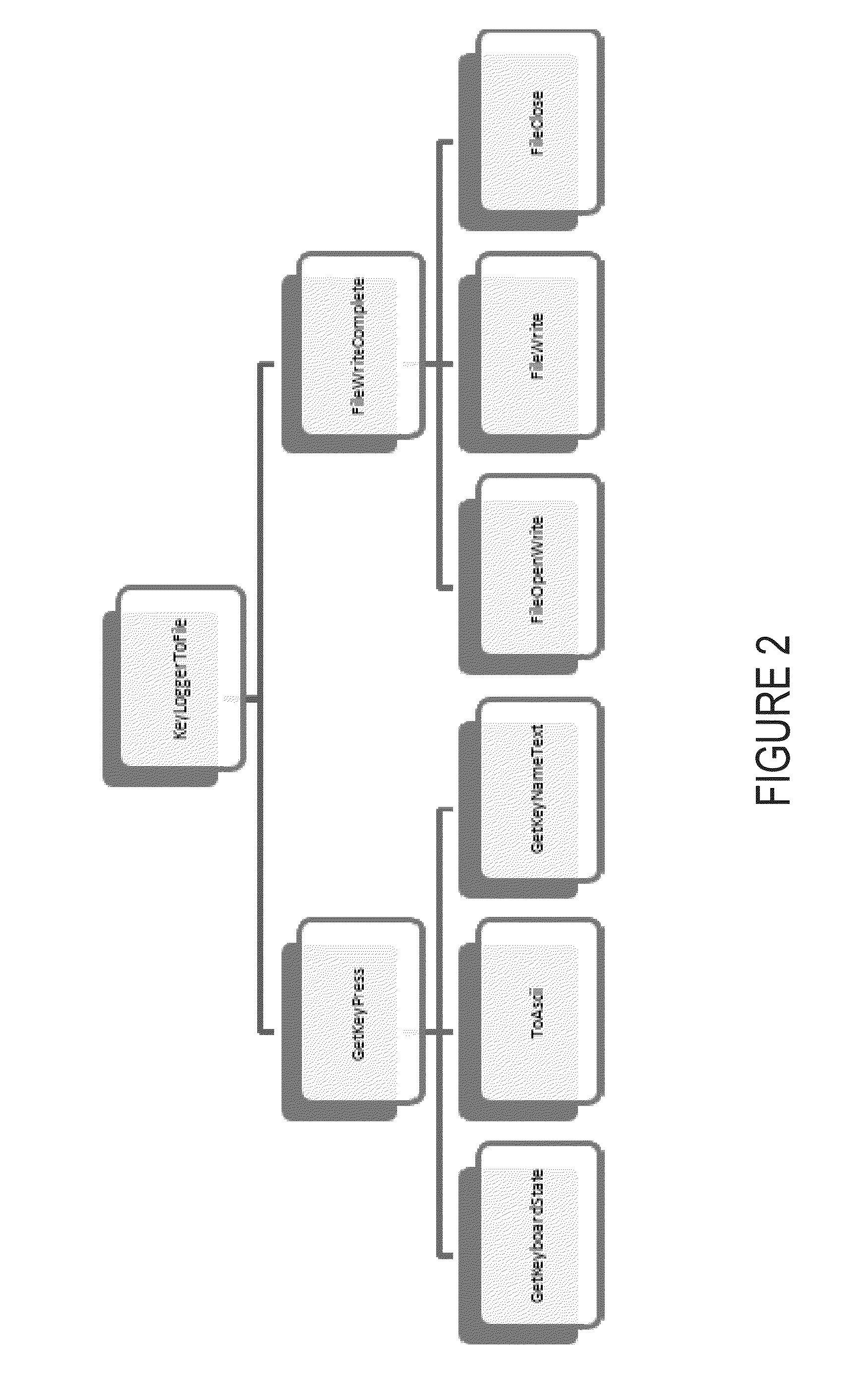
[0028]This disclosure describes a novel compiler agnostic system that automatically identifies where the functionality of a program (that may include application software, operating system software, and / or software libraries / tools) begins and ends, and detects malicious software by analyzing program behavior. Operating system software manages computer hardware and software resources and provides common services for computer programs. Application software (an application) is a set of computer programs designed to permit the user to perform a group of coordinated functions, tasks, or activities. Application software cannot run on itself but is dependent on system or operating software to execute.
[0029]The novel compiler agnostic system recognizes specific classes of program behavior without decompiling the machine language into its original source code. The system recognizes specific program behaviors by identifying patterns in external function call behavior. The system includes reco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com