Secure identity authentication in an electronic transaction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
Overview
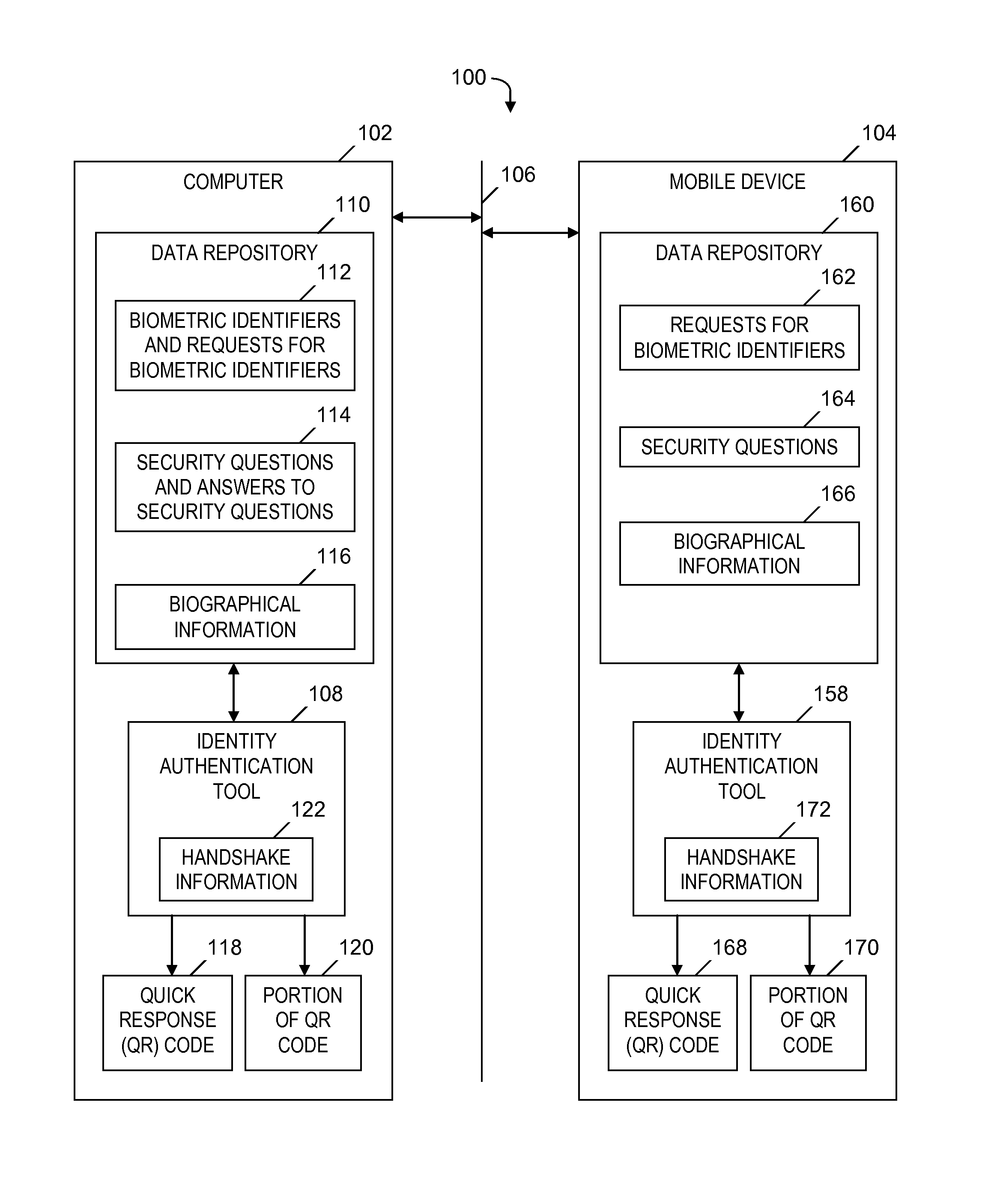
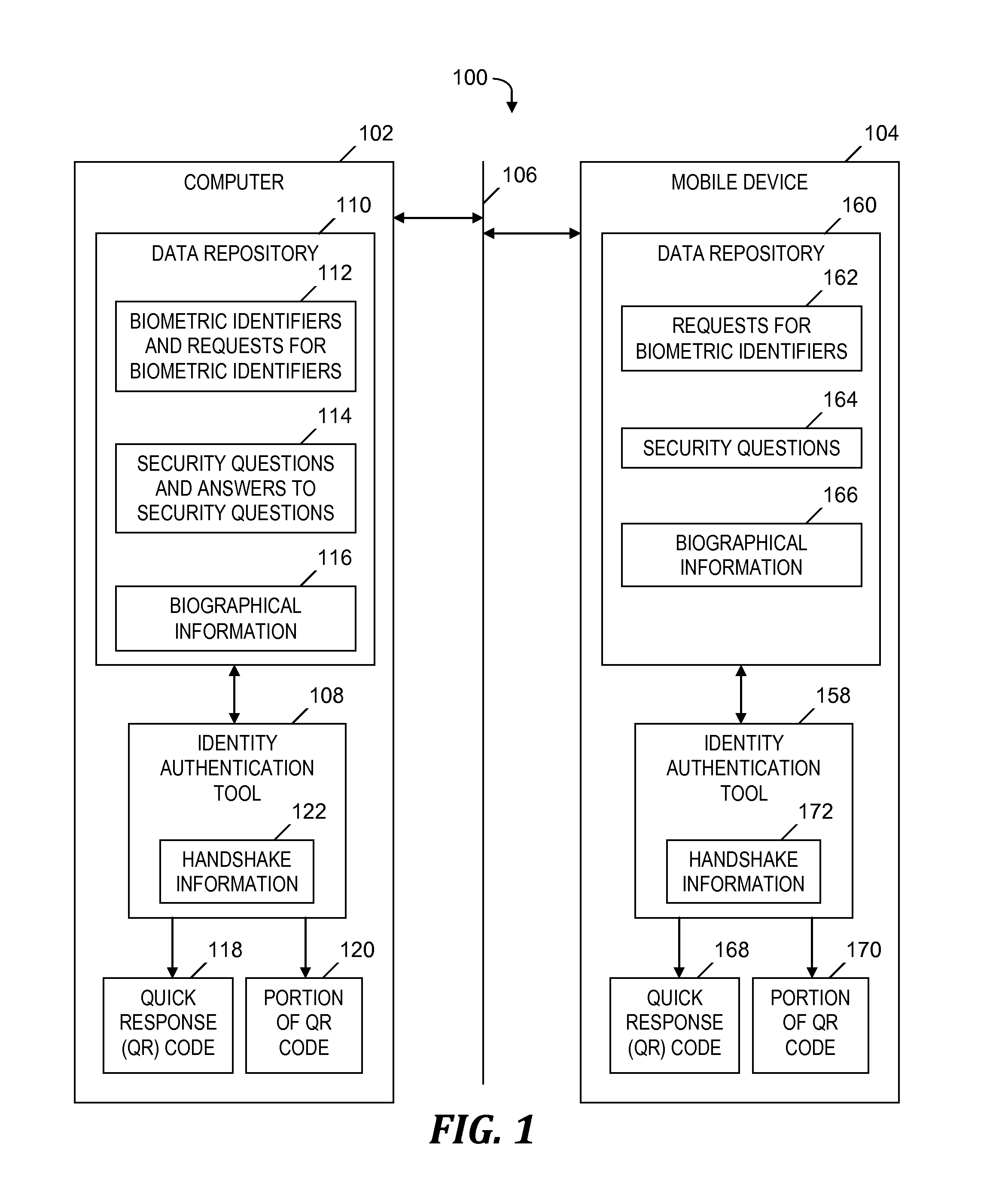
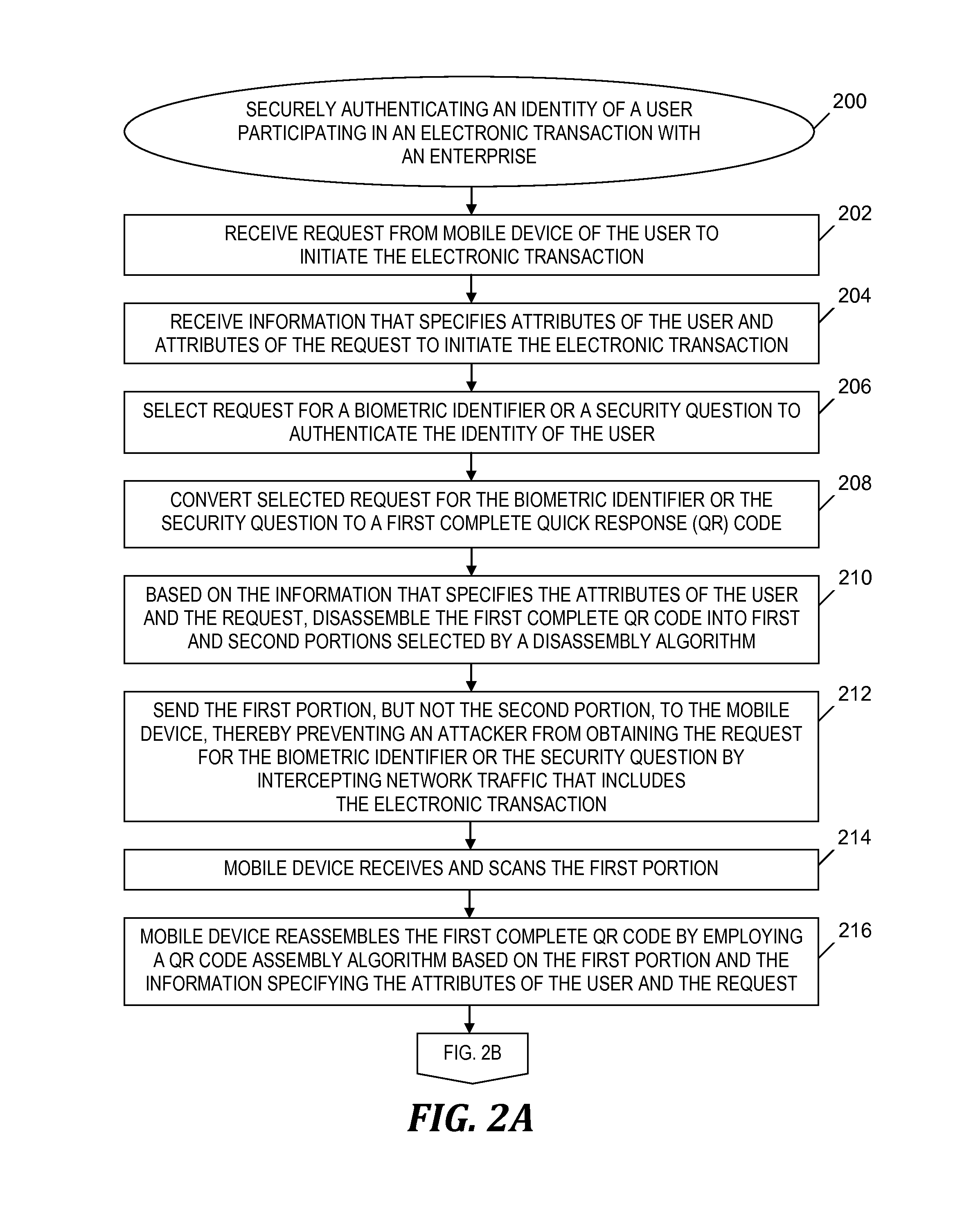
[0016]Embodiments of the present invention sends a portion of a complete QR code during an electronic transaction between a first computer (e.g., mobile device) and a second computer, where the QR code specifies authentication information which authenticates the identity of a user of the first computer. By sending only a portion of the complete QR code, rather than the complete QR code, embodiments of the present invention prevent a malicious entity from (1) intercepting the authentication information or (2) intercepting the complete QR code and deriving the authentication information from the intercepted complete QR code, and subsequently using the authentication information for a fraudulent transaction.
System for Secure Authentication of an Identity in an Electronic Transaction
[0017]FIG. 1 is a block diagram of a system 100 for securely authenticating an identity of a user participating in an electronic transaction with an enterprise, in accordance with embodiments of the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com