Method and system of adding region and obtaining authority object of mobile terminal
A mobile terminal and copyright object technology, applied in the DRM field, can solve the problems of poor security of the DRM system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
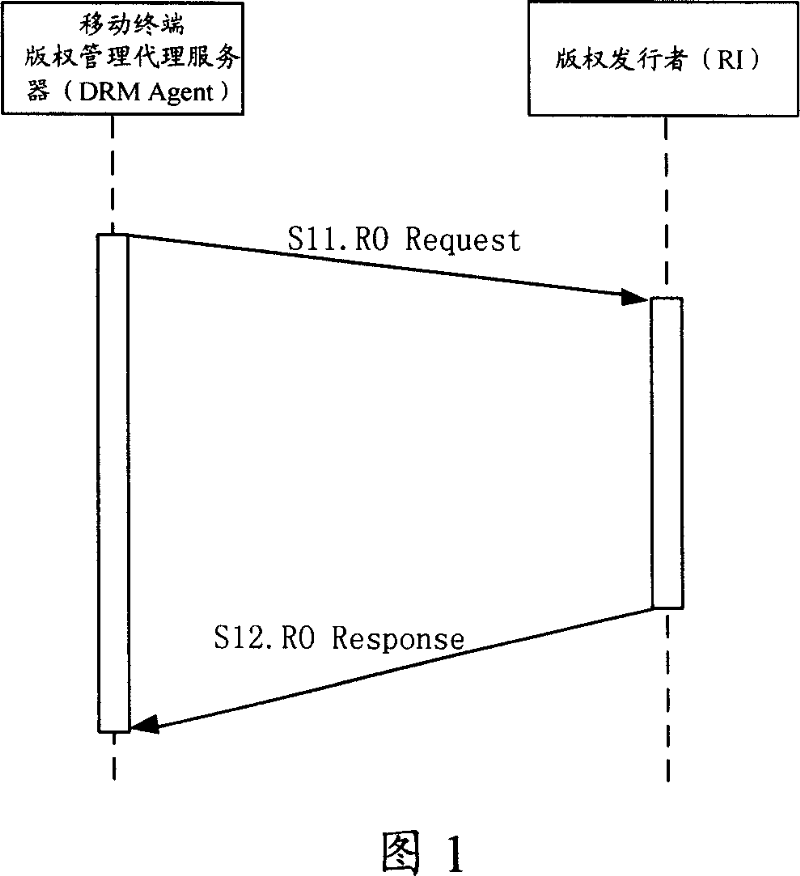
[0110] As shown in Figure 4, the first embodiment is based on the existing 2-pass protocol process of requesting RO from RI initiated by the mobile terminal, and adds the step of RI requesting the OCSP responder to verify the validity of the RI certificate:
[0111] S41. The DRM Agent sends an RO request message to the RI;
[0112] The RO request message carries the DRM Agent certificate, the identification information and usage method of the digital information selected by the mobile terminal user, and the DRM Agent uses the user's private key and the complete RO request message to generate the user's digital signature.
[0113] S42. The RI sends an OCSP request (OCSP Request) message to the OCSP responder to request verification of the validity of the RI certificate;
[0114] After receiving the RO request message sent by the mobile terminal, RI first uses the user public key and user digital signature to verify whether the terminal identity is legal. The verification method...
Embodiment 2
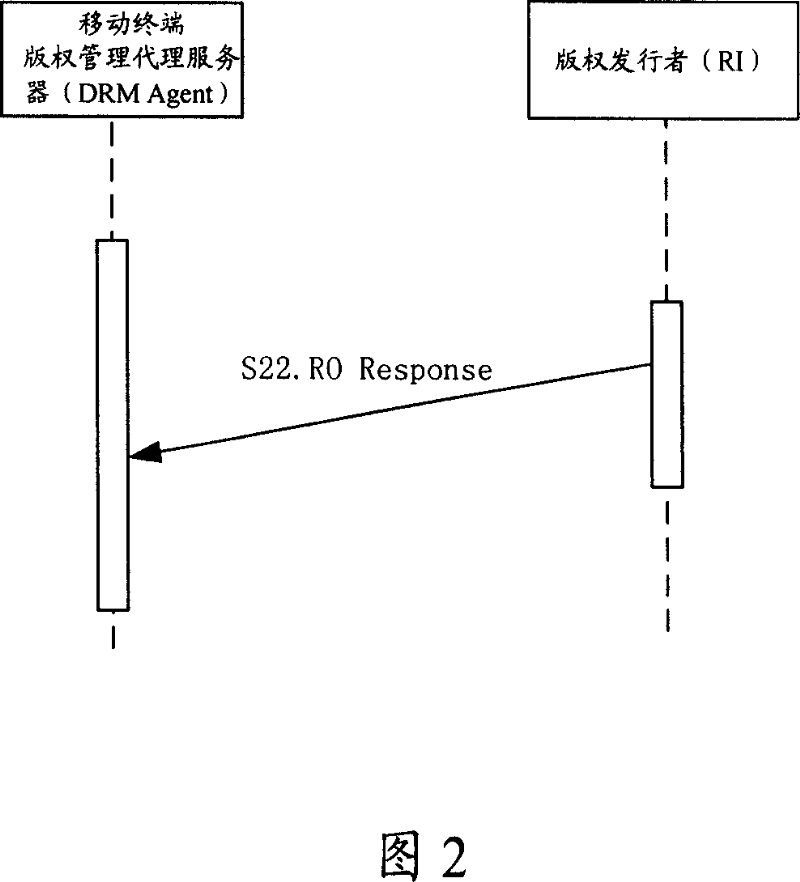
[0132] As shown in Figure 5, Embodiment 2 is based on the existing 1-pass protocol flow of RI distributing ROs to mobile terminals, and adds the step of verifying the validity of RI. Compared with Embodiment 1, DRM Agent does not need to send ROs to RIs. To send the RO request message, other steps are the same as in Embodiment 1, specifically:
[0133] S51. The RI sends an OCSP request message to the OCSP responder to request to verify the validity of the RI certificate;
[0134] The RI sends an OCSP request message to the OCSP responder, and the message carries the RI certificate and the RI digital signature generated by using the RI private key.
[0135] S52. The OCSP responder returns an OCSP Response authentication response message to the RI;
[0136] The OCSP responder first uses the RI public key and RI digital signature to authenticate the validity of the RI identity. If it is legal, it judges the validity of the RI certificate according to the RI certificate revocatio...
Embodiment 3
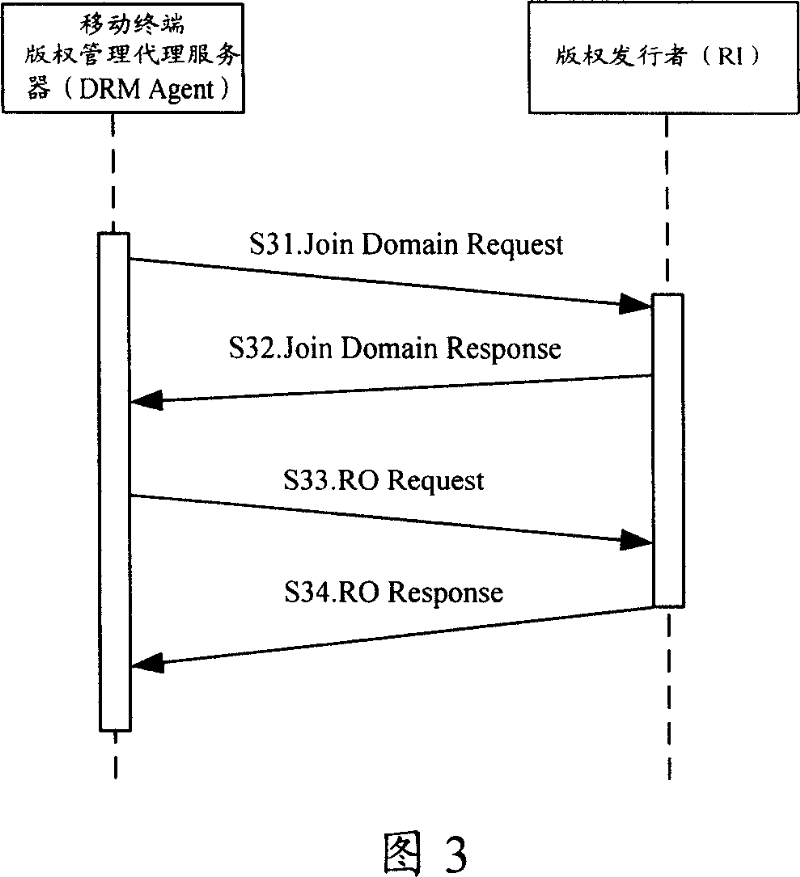
[0149] As shown in FIG. 6 , the third embodiment is based on the existing 2-pass protocol flow in which the mobile terminal requests the RI to join the domain, and adds an authentication step of the RI certificate, specifically including:
[0150] S61. The DRM Agent sends a domain join request message to the RI;
[0151]The mobile terminal user selects the operation of joining the domain through the DRM Agent and enters the domain joining ID according to the prompt, and the DRM Agent sends a domain joining request message to the RI. key and complete the user's digital signature generated from the domain join request message.
[0152] S62. The RI sends an OCSP request message to the OCSP responder, requesting to verify the validity of the RI certificate;
[0153] After receiving the request message to join the domain sent by the mobile terminal, RI uses the user public key and user digital signature to verify the legitimacy of the terminal user's identity, and refuses to reply...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com