Identification method of mobile terminal user legalness
A technology of a mobile terminal and a verification method, which is applied in the verification field of a wireless communication network, can solve the problems such as the mobile terminal being easily stolen and robbed, achieves the purpose of preventing thieves from robbing the mobile terminal, solves the problem of being easily stolen and has a simple and reliable implementation method. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
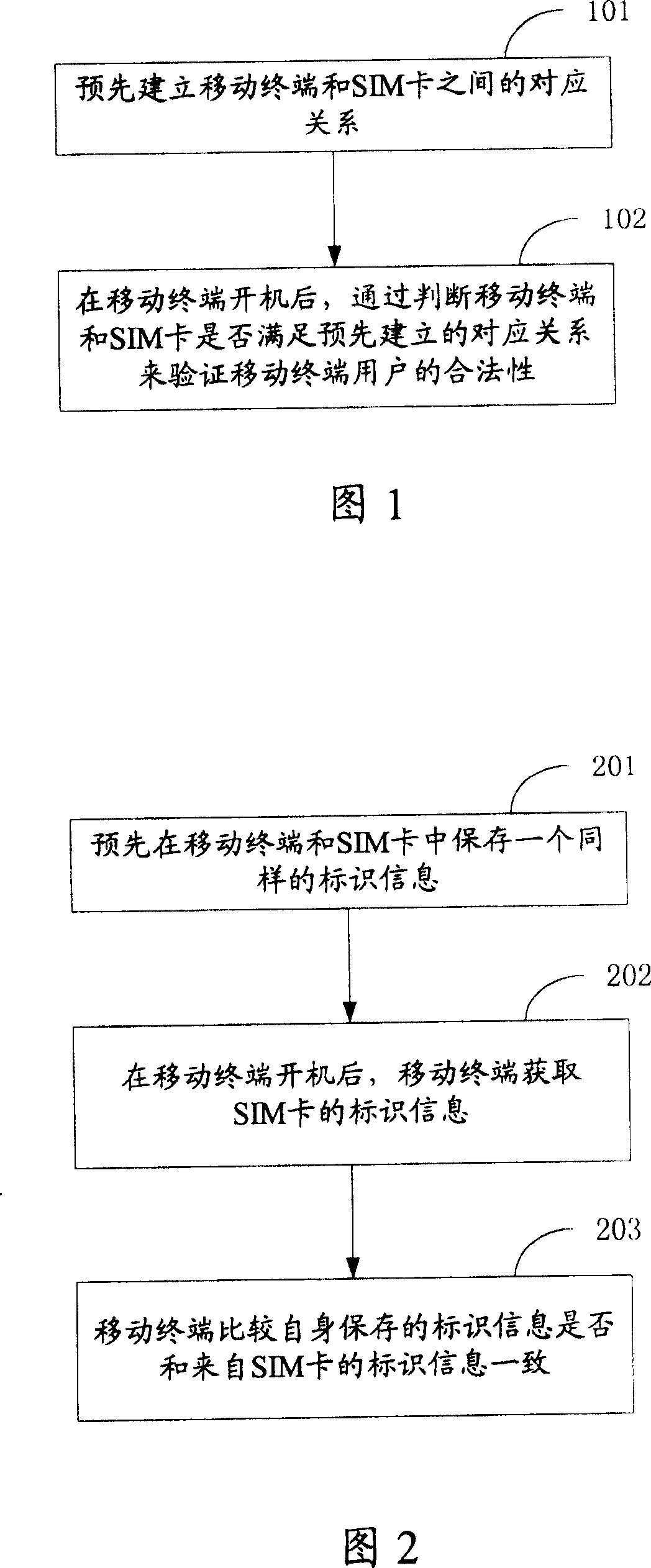
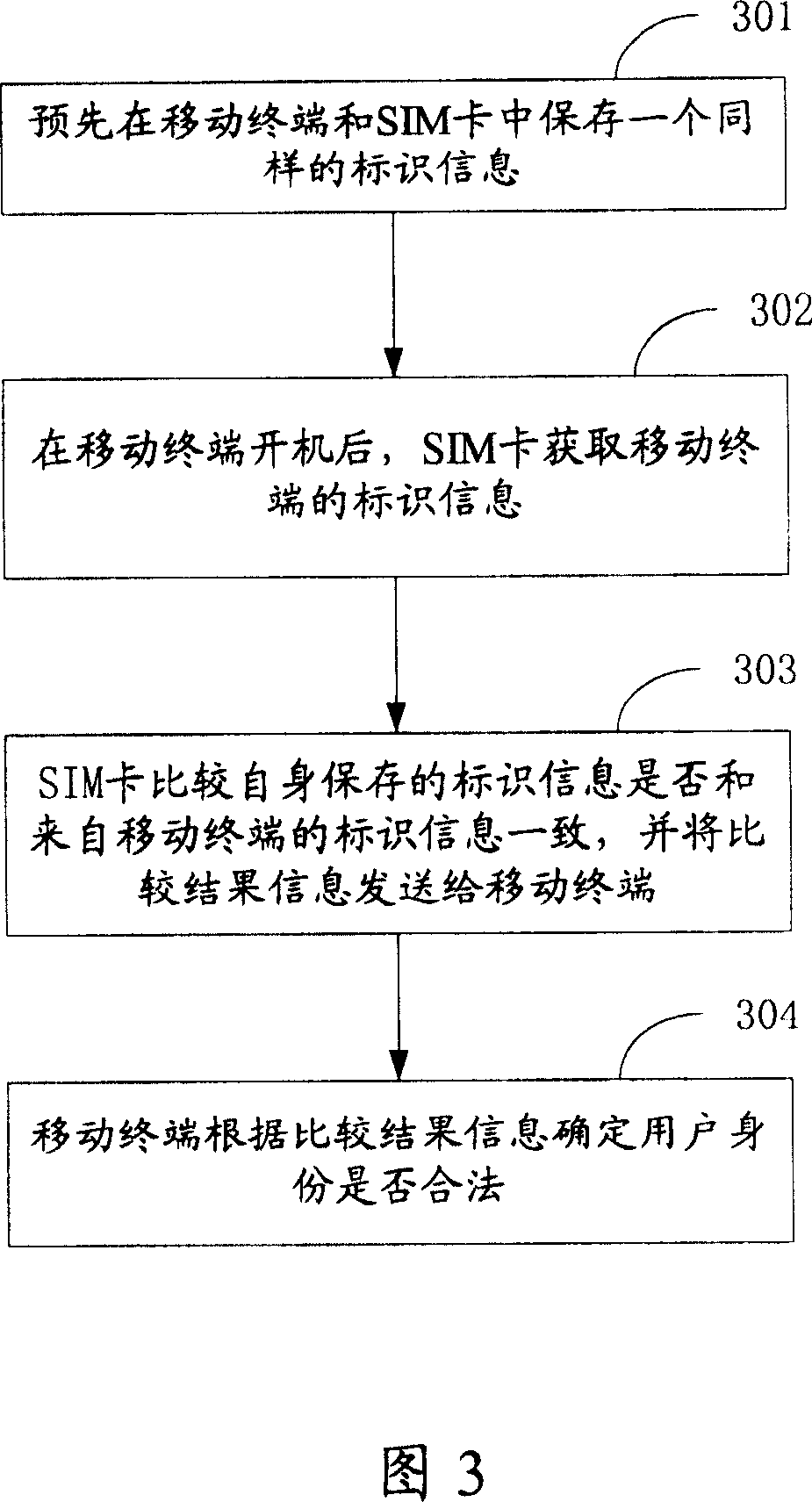
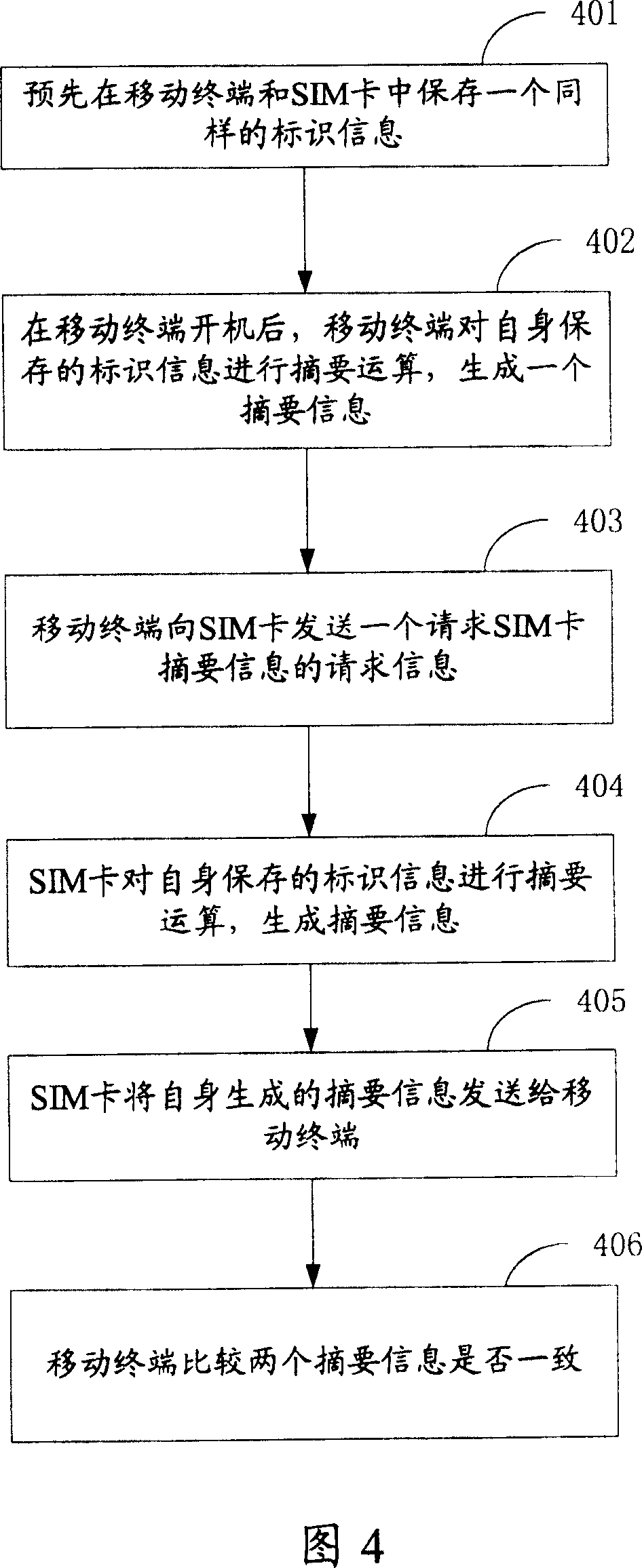
[0045] Fig. 1 shows the general flowchart of the present invention. As shown in FIG. 1 , first at step 101 , the corresponding relationship between the mobile terminal and the SIM card is established in advance.
[0046] In step 102, after the mobile terminal is turned on, it is judged whether the current mobile terminal and the SIM card meet the pre-established correspondence. If yes, it indicates that the identity of the mobile terminal user is legal. At this time, the mobile terminal can log in or connect to the network normally, and the user can use the mobile terminal to perform any operations; otherwise, it indicates that the identity of the mobile terminal user is illegal, and the mobile terminal can stop responding to user operations at this time , and exit the network and cease providing service.
[0047] The overall process of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com