Method for detecting superlong signaling message based text code
A signaling message, super-long technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems such as inability to provide super-long malformed messages, network marginal security risks, and reduced network efficiency, and achieve malicious attacks. Significant, guaranteed uptime, protection against attack and sabotage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0061] For any feature separator in the received text, check whether the character directly adjacent to it is a feature separator, and if it is a feature separator, then judge whether the two feature separators belong to the feature separator. Adjacency is not allowed in the constraint relationship table If it is, it means that the current text is detected as an overlong message; for any feature delimiter in the received text, check whether the distance between another feature delimiter with the closest interval exceeds the maximum specified in the feature distance table If it is, it means that the current text is detected as an overlong message.
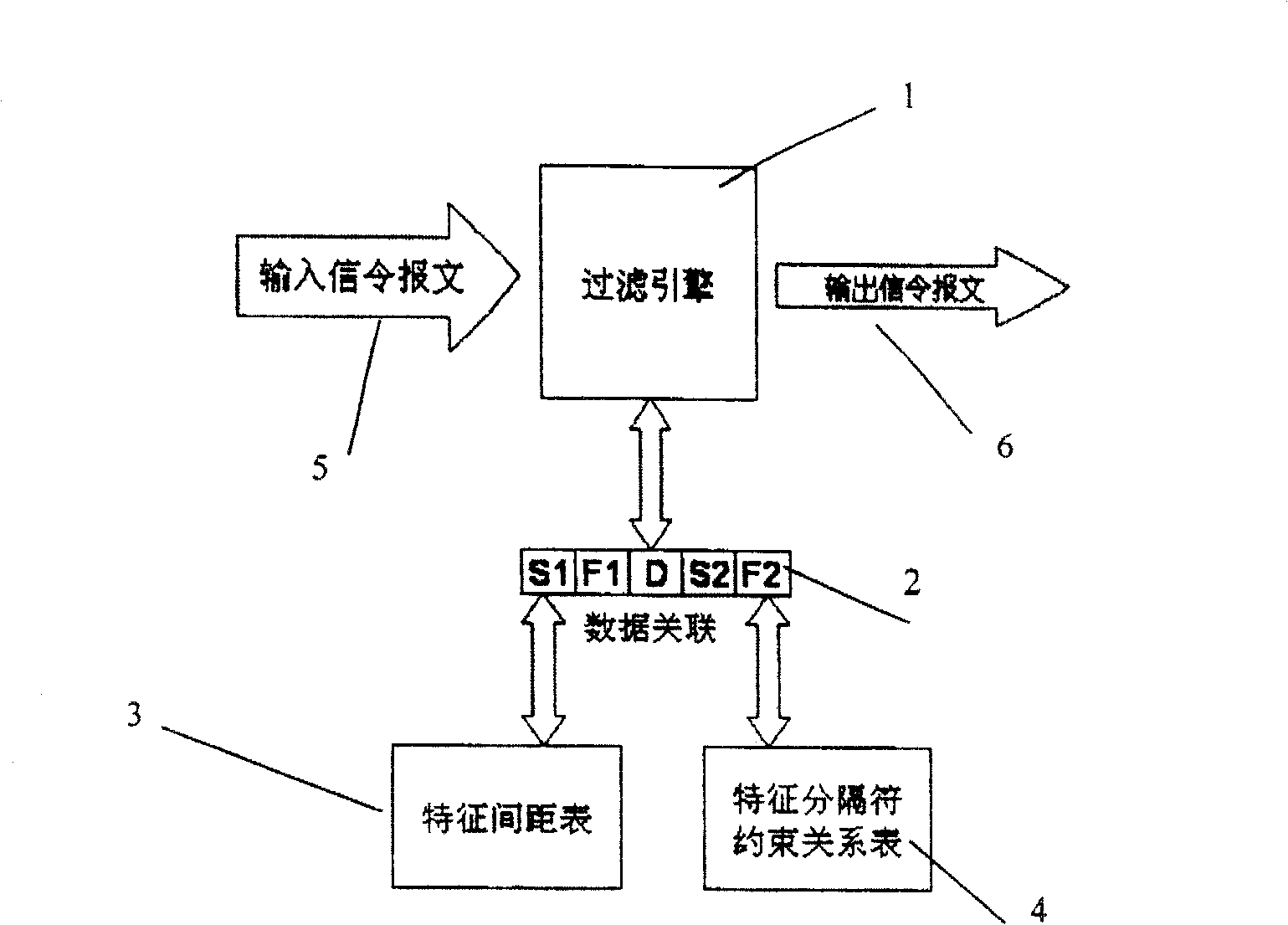
[0062] In order to realize the rapid detection of the input signaling message, the method of the present invention has utilized a five-tuple (S1, F1, D, S2, F2) as data association, and this five-tuple can be figure 1 The result of the preprocessing of the input data packet 5 by the middle filter engine 1 is the basis for quickly ju...
Embodiment 2
[0070] Each quintuple (S1, F1, D, S2, F2) formed according to the input signaling message is detected as follows: if F1 is a feature separator and whether S1 and F1 satisfy the prohibition of connection in the feature separator constraint relationship table For example, if F2 is a feature separator and whether S2 and f2 meet the prohibition of connection in the feature separator constraint relationship table; whether the feature distance D satisfies the feature distance between S1 and S2 defined in the feature distance table. If any point satisfies the condition of an overlong message, the message is filtered out.
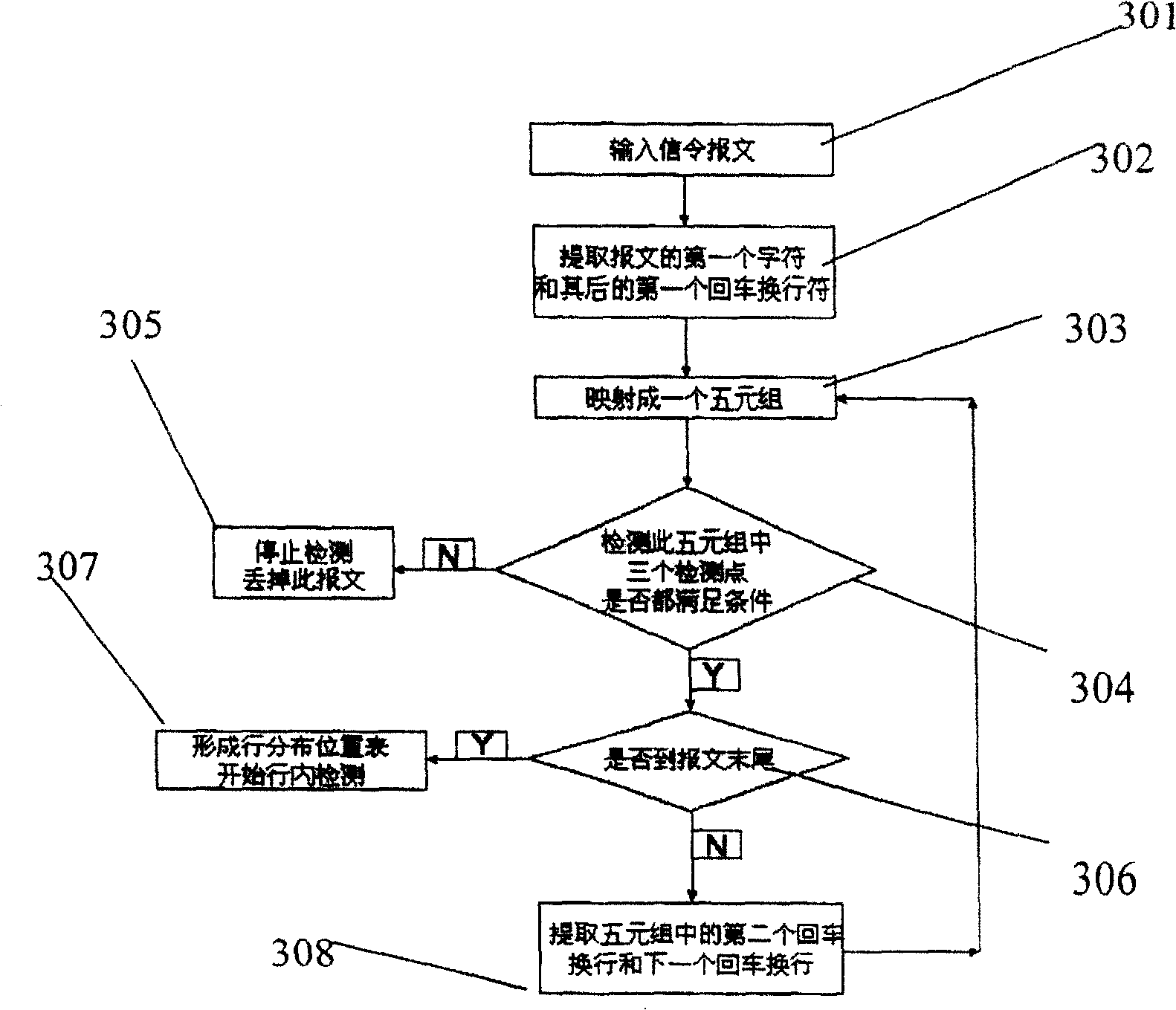
[0071] As mentioned above, the quintuple (S1, F1, D1, S2, F2) of any text segment has three detection points, and three points are detected at the same time during detection, if one point meets the condition of an ultra-long message, it is considered that the text segment contains an ultra-long message. Long messages can be filtered out. The above-mentioned detect...
Embodiment 3
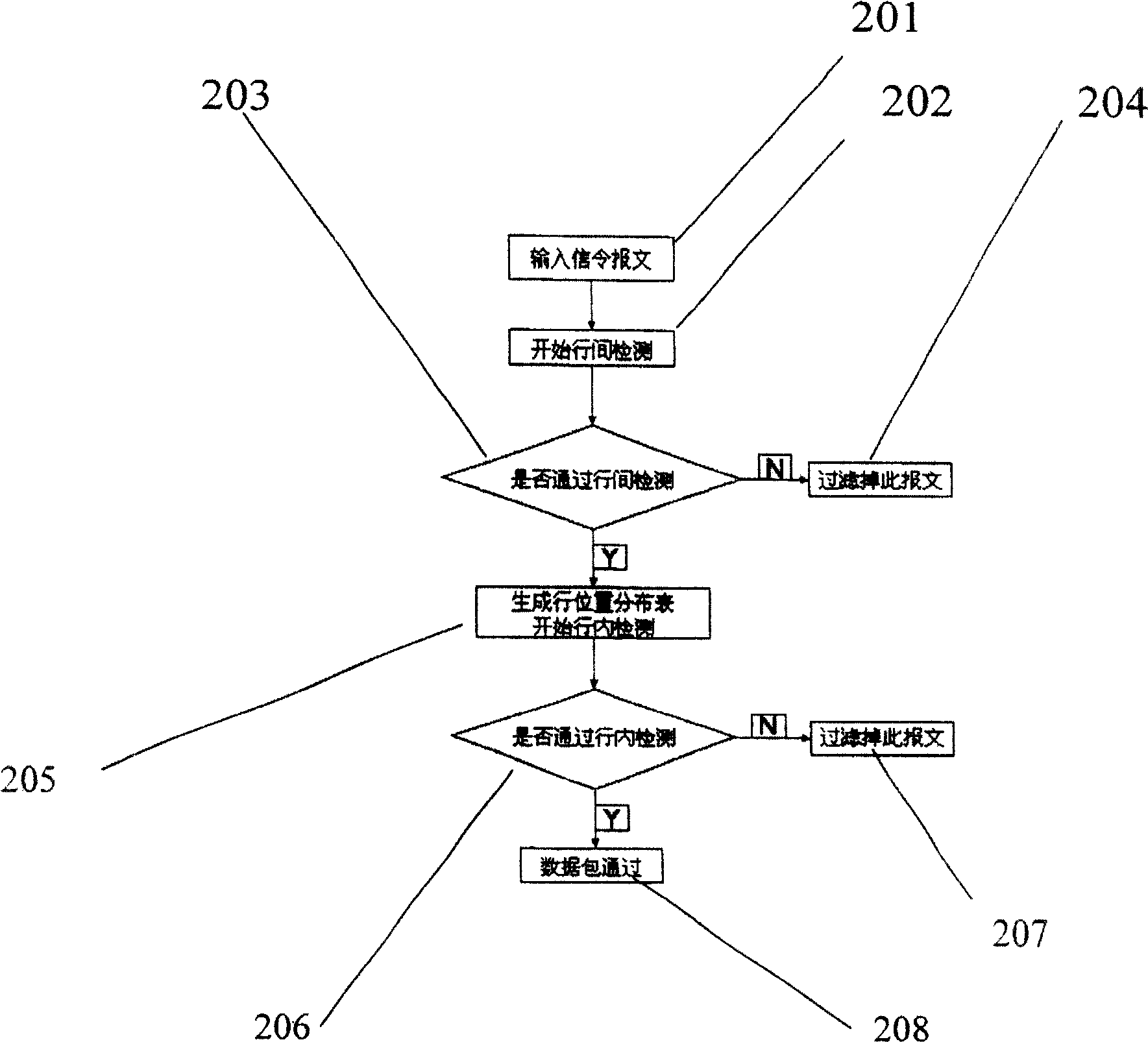
[0073] Utilize the method of the present invention to the detection of superlong signaling message, can adopt the detection method that inter-row detection and intra-row detection combine, namely, such as figure 2 As shown, first judge whether the length of each line in the signaling message is within the normal range, as long as one line is not satisfied, the message will be filtered out; if each line is satisfied, a line distribution position table will be generated to guide the in-line detection, Determine whether the feature spacing between each feature separator in each line meets the requirements.
[0074] combine figure 2 , look at the whole detection process, start to input signaling message in frame 201, start interline detection in frame 202, judge the interline detection result in frame 203, if it belongs to super long message, then filter it in frame 204 Otherwise, in frame 205, generate row position distribution table, start detection in row; In frame 206, dete...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com