Automatic-installable information safety equipment and control method thereof
An information security and automatic installation technology, applied in the field of information security, can solve problems such as increased costs, reduced reliability, and user misunderstandings, and achieves cost-effective effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
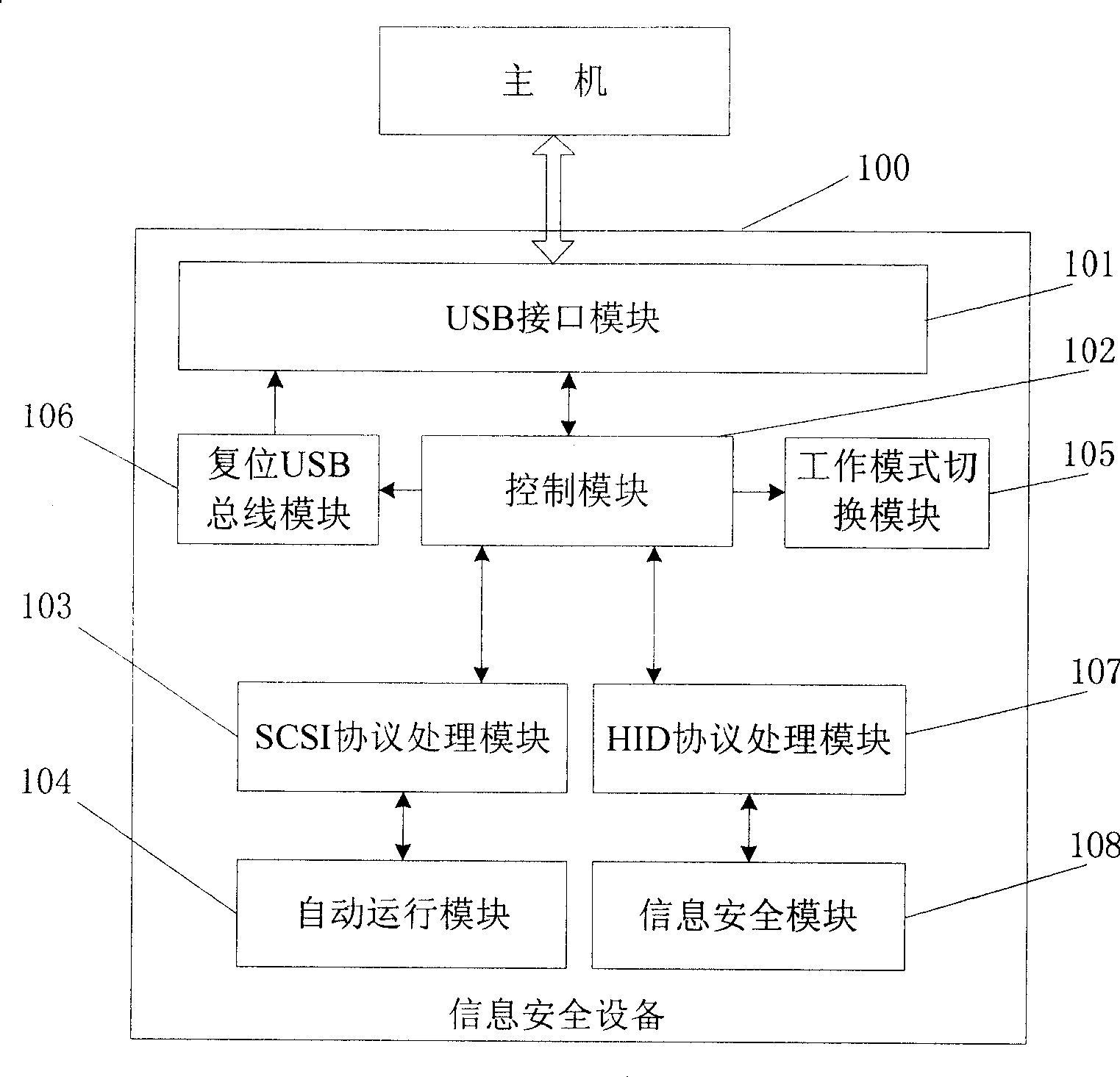
[0065] This embodiment provides an information security device 100 that can be installed automatically, such as figure 1 As shown, it includes a control module 102, a USB interface module 101, a working mode switching module 105, a SCSI protocol processing module 103, an automatic operation module 104, a HID protocol processing module 107, an information security module 108 and a reset USB bus module 106. The control module is connected with the USB interface module, the reset USB bus module, the working mode switching module, the SCSI protocol processing module, and the HID protocol processing module, the reset USB bus module is connected with the USB interface module, the automatic operation module is connected with the SCSI protocol processing module, and the information The security module is connected with the HID protocol processing module.
[0066] The USB interface module 101 is used to establish a connection between the information security device and the host through...
Embodiment 2
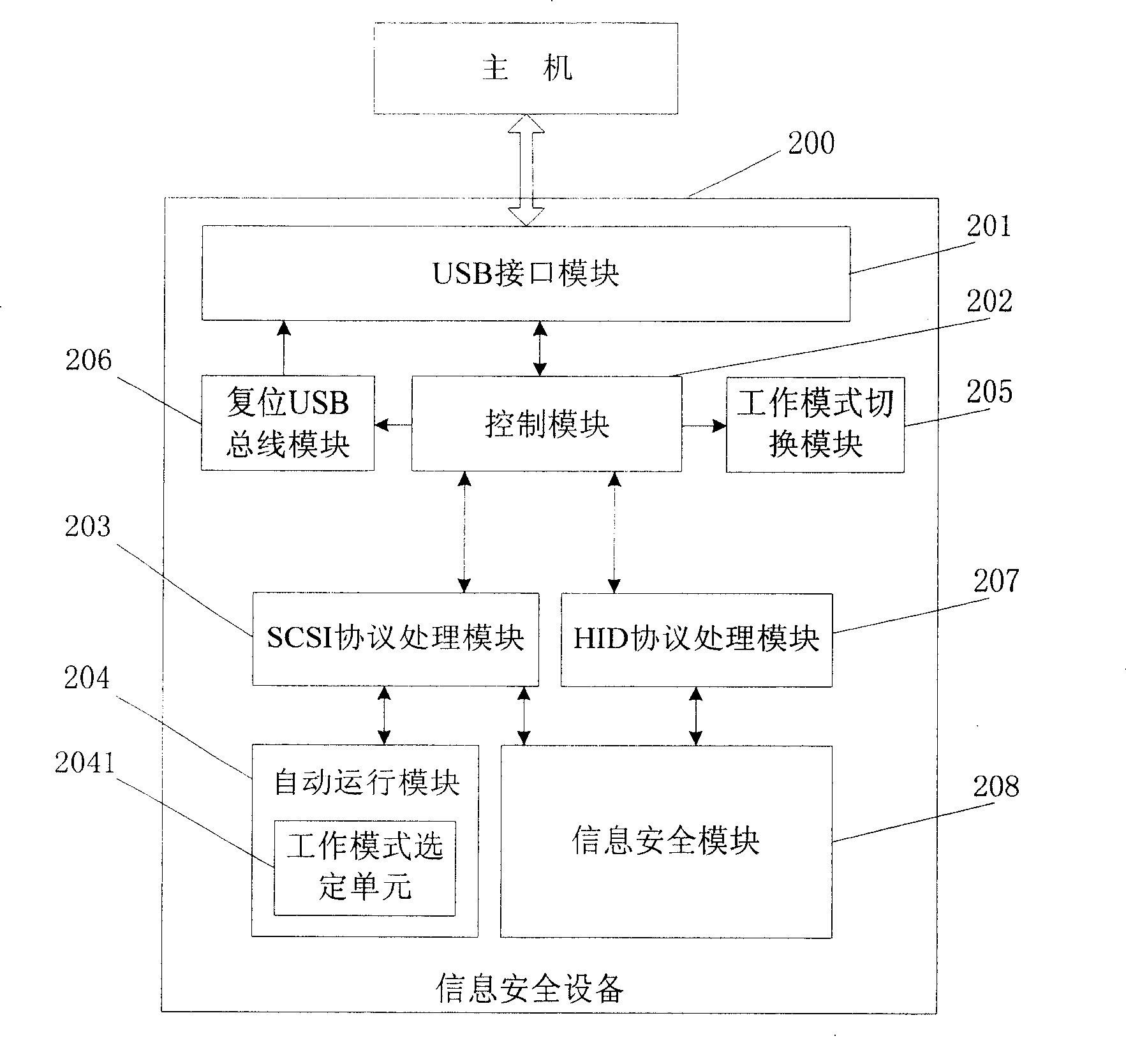
[0077] This embodiment provides an information security device 200 that can be installed automatically, such as figure 2 As shown, it includes a control module 202, a USB interface module 201, a working mode switching module 205, a SCSI protocol processing module 203, an automatic operation module 204, a reset USB bus module 206, a HID protocol processing module 207 and an information security module 208. The control module is connected with the USB interface module, the reset USB bus module, the working mode switching module, the SCSI protocol processing module, and the HID protocol processing module, the automatic operation module is connected with the SCSI protocol processing module, the reset USB bus module is connected with the USB interface module, and the information The security module is respectively connected with the SCSI protocol processing module and the HID protocol processing module.
[0078] The USB interface module 201 is used to establish a connection betwee...
Embodiment 3
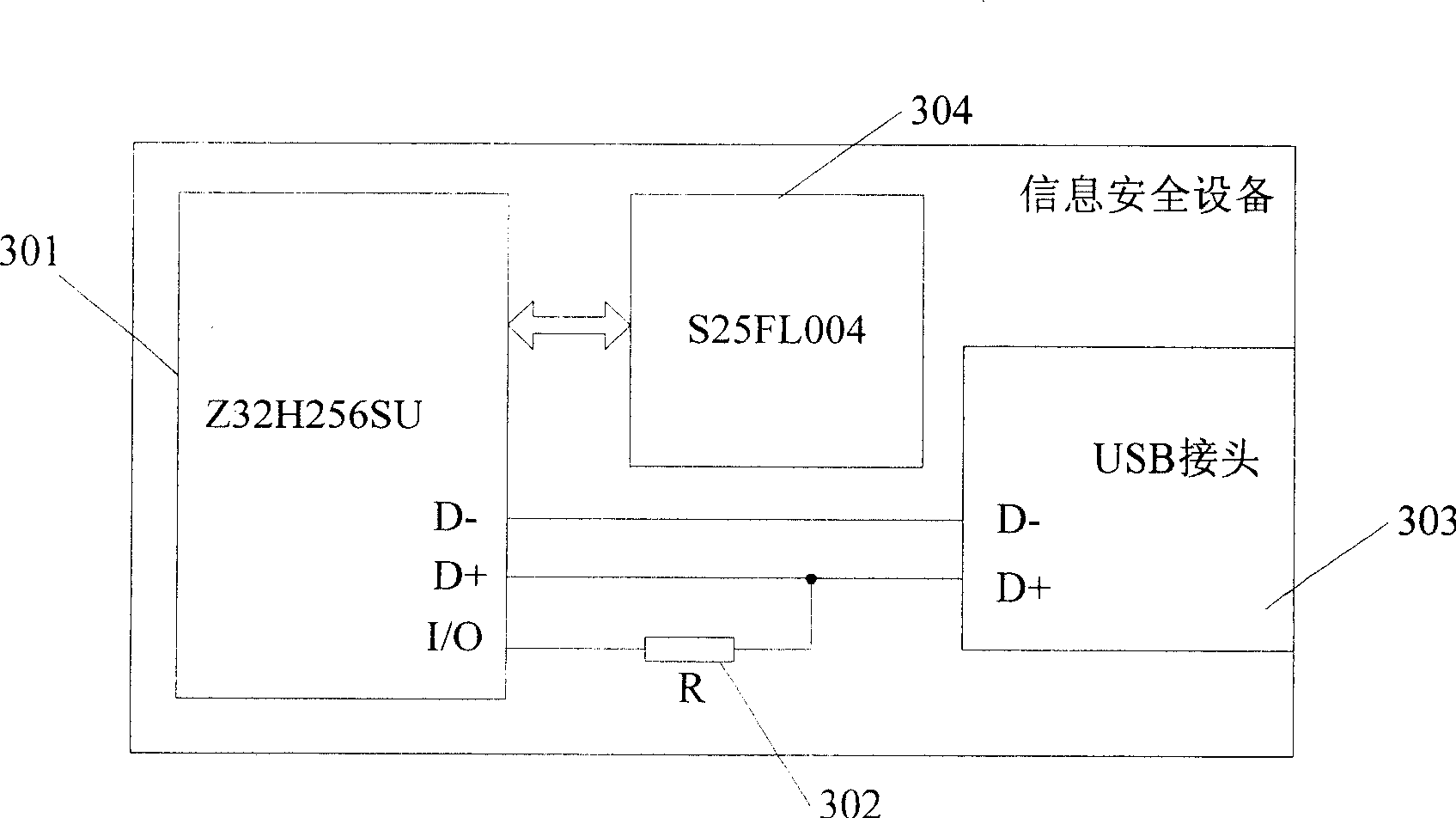
[0096] This embodiment proposes a control method for information security equipment that can be automatically installed, such as Figure 4 shown, including the following steps:
[0097] Step 401: Establish a connection between the information security device and the host through a USB interface.
[0098] Step 402: The information security device declares itself as a SCSI device type.
[0099] The host sends a request to obtain the device type to the information security device, and the information security device reports to the host that the device descriptor is a SCSI device descriptor, and declares itself to be a SCSI device type.
[0100] Step 403: Automatically start the Autorun program.
[0101] The Autorun program is pre-stored in the information security equipment and pre-written by the information security equipment manufacturer.
[0102] Step 404: The Autorun program detects whether the application program related to the information security device has been installed...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com