Flashmemory safety system and method thereof
A security system, technology of flash memory, applied in the field of security systems, can solve problems such as inability to execute security systems, difficulties, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0055] The embodiments described in this paragraph are to illustrate the present invention, but not to limit the present invention. The invention is not limited to particular materials, processing steps or dimensions. The invention is defined by the appended claims.
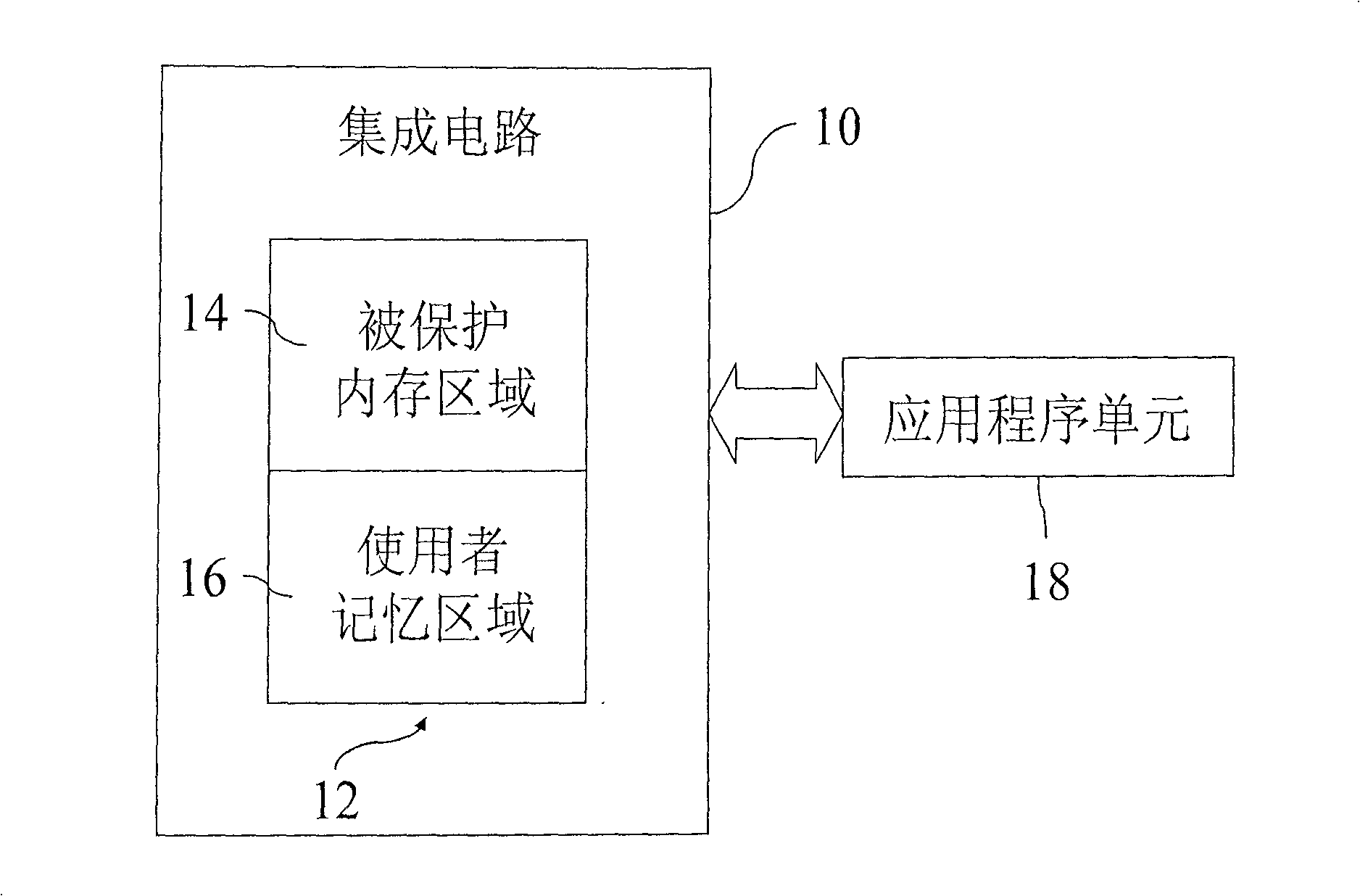
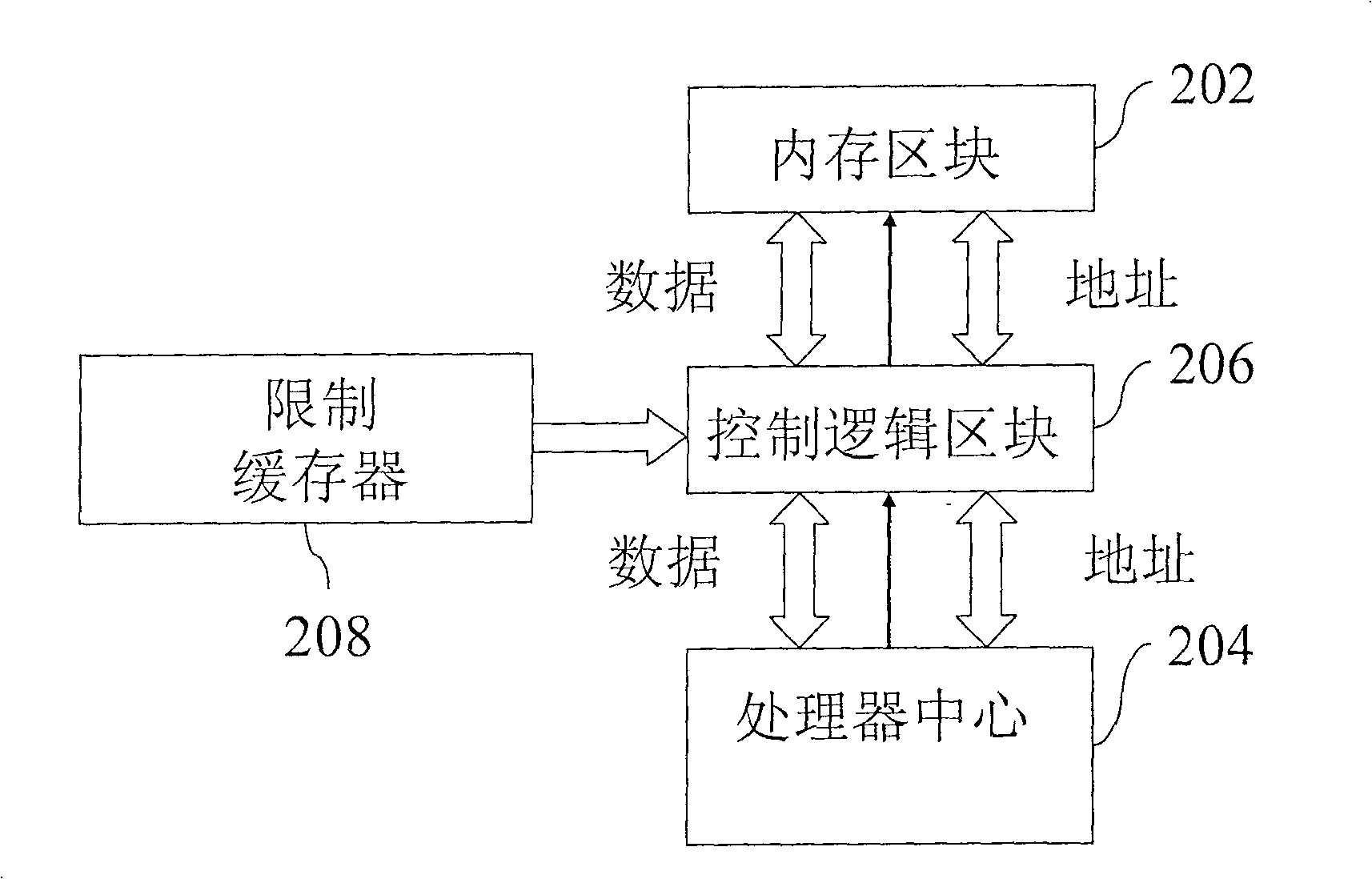
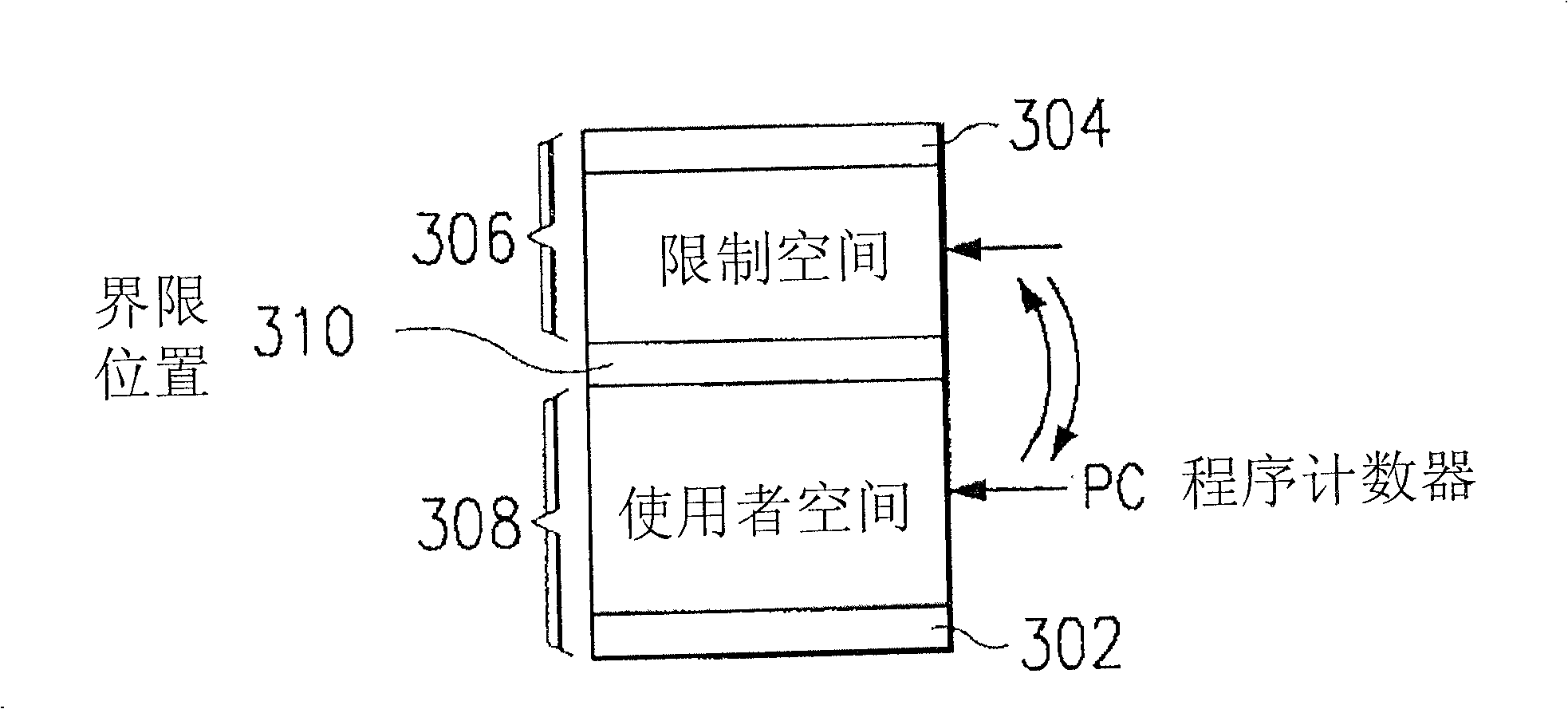
[0056] see Figure 4 , which is a schematic diagram disclosing a security system applied to a flash memory according to a preferred embodiment of the present invention. As shown in the figure, the module structure of the security system of the flash memory 40 includes a memory space 41, which is provided with an identification program 411; Space 41, is used for judging whether this specific signal 412 accords with the predetermined restriction signal 441 that is stored in external processor 44; When the limit signal 441 is predetermined and a negative decision is made, the identification program 411 in the memory space 41 is prohibited from being used.
[0057] In practical applications, the logic component 4...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com