Method of implementing random access
An implementation method and random access technology, which are applied in code division multiplexing systems, data exchange through path configuration, electrical components, etc., can solve the problems of large system resource overhead and large complexity of Signature processing table, etc. Achieve the effect of less resource overhead, improved random access performance, and low network management complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
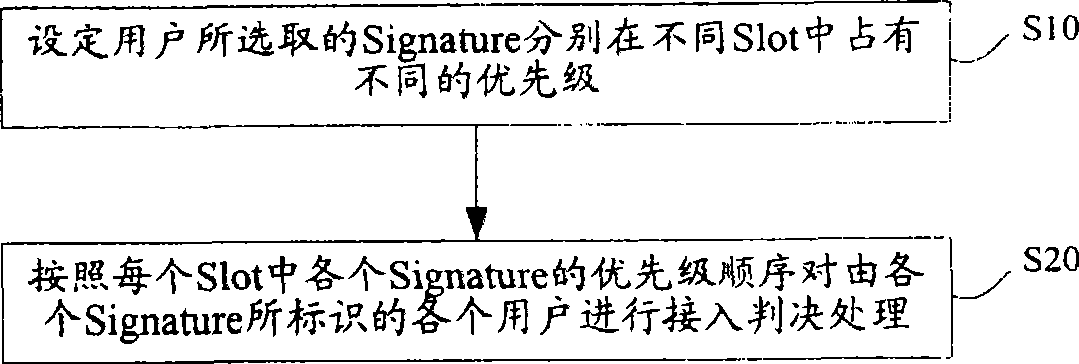
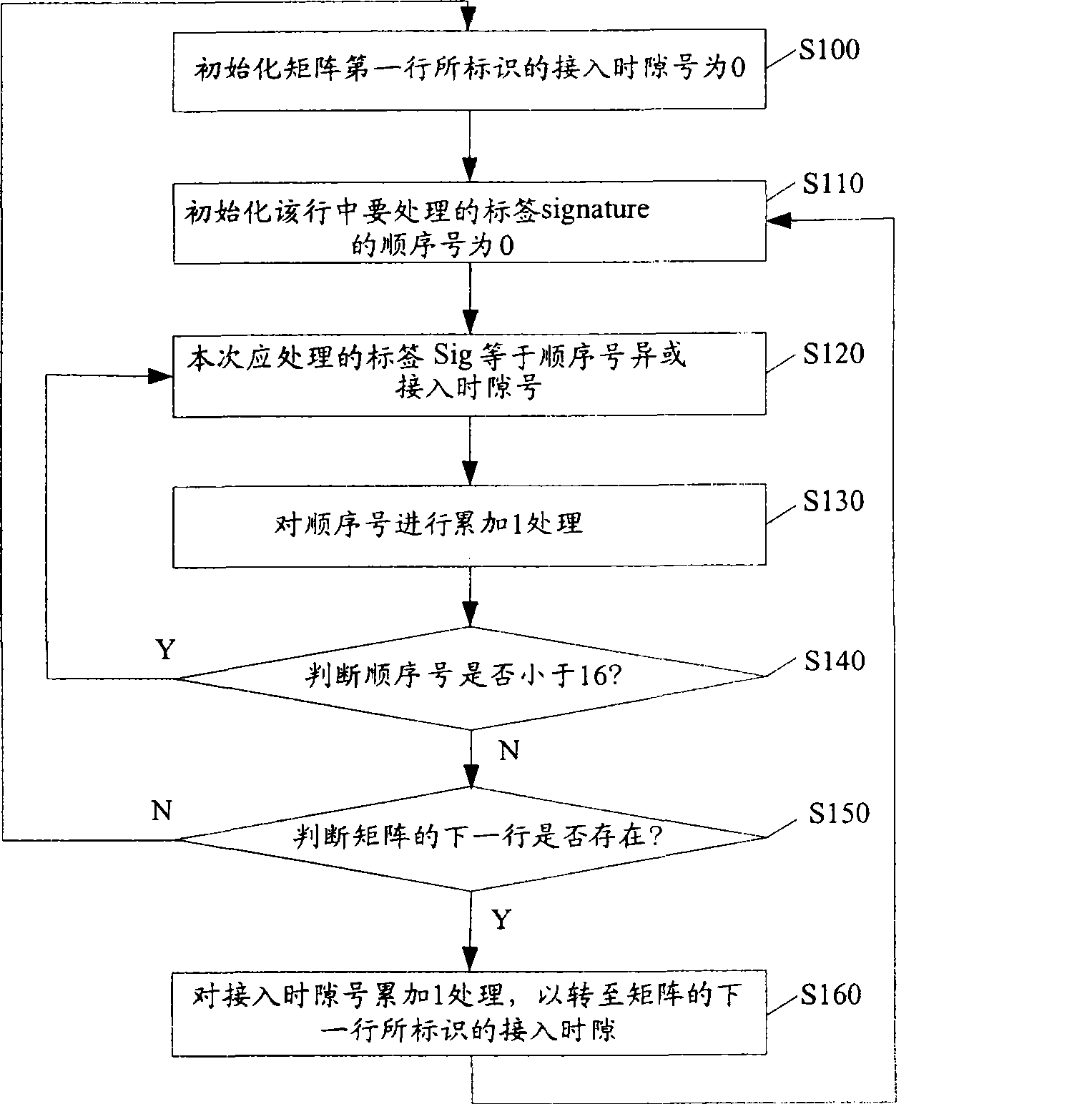
[0041]It has been discussed in the above prior art that on the base station side of the mobile communication network, due to the limitation of limited access resources, it is generally unable to support simultaneous data sent by 16 users identified by 16 different signatures in one access time slot. Demodulation; therefore, under the condition that system access resources allow, it is necessary to reflect the principle of fair access among users. The implementation method of random access in the present invention is based on the above principles, and provides a processing method based on table lookup, which can not only reduce the management complexity of the network side, but also occupy less overhead of system resources. On the basis of , the random access performance of the network system can be improved to a greater extent.
[0042] The specific implementation process of the method for realizing random access of the present invention will be described in detail below in co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com