Firewall access control method of object-orientation mode
An access control, object-oriented technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems such as system congestion, firewall performance degradation, and system resource occupation, and achieve the effect of reducing the number and avoiding repeated calls.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
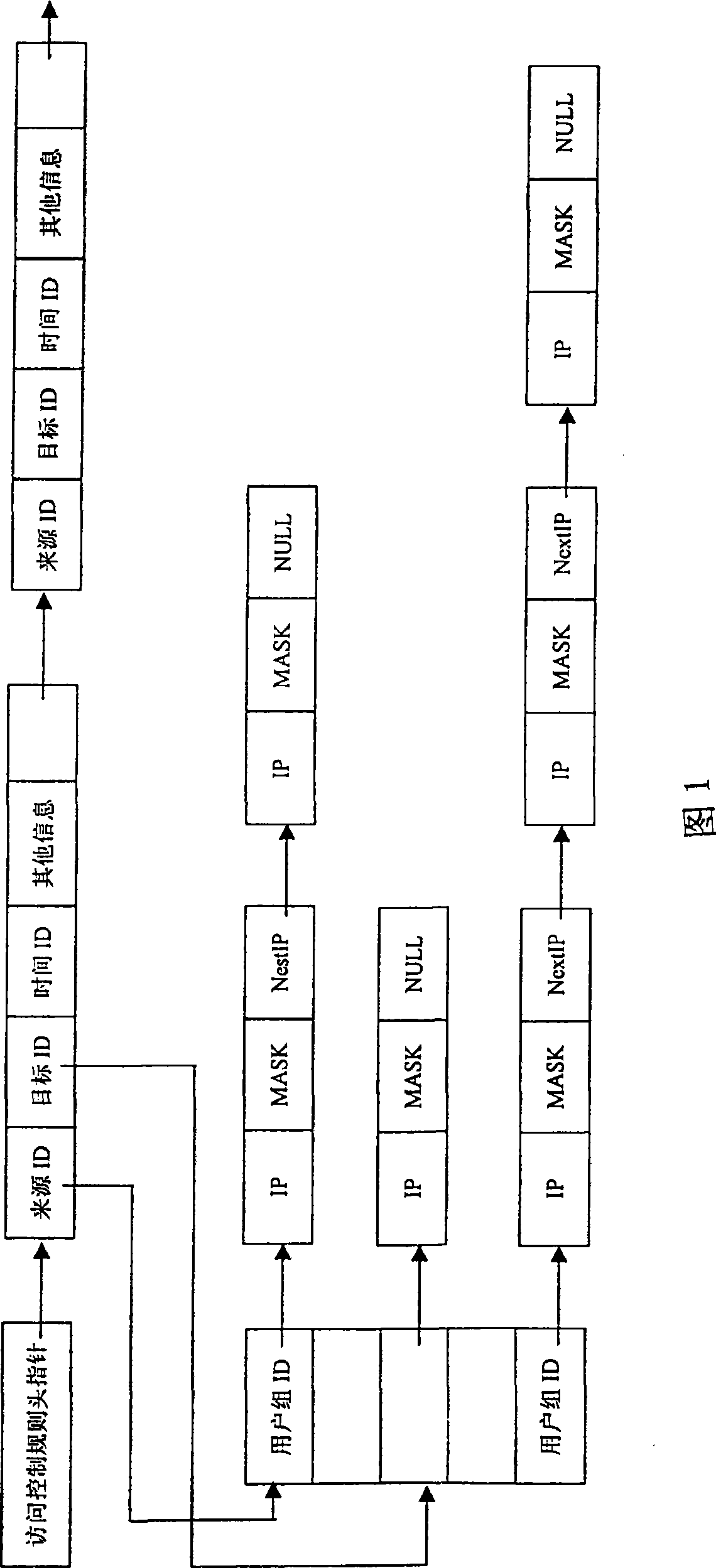
[0056] In conjunction with the data structure and interrelationships shown in Figure 1, the firewall access control in the object-oriented manner is implemented in this way:
[0057] The first step is to classify the access control objects of the firewall.
[0058] Define each object to be controlled by the firewall, including source address, destination address, protocol and port number that constitute a certain service, time, etc. including,
[0059] (1), address class definition structure:
[0060] Type (mask_type), used to identify whether the following address is ip-ip or ip / mask structure;
[0061] reserved bit (reserve);
[0062] User group ID (group_id);
[0063] IP address, expressed as a single IP address (ip-ip), or a network segment (ip / mask);
[0064] (2), service class definition structure:
[0065] service group ID (ser_id);
[0066] Protocol content (protocol);
[0067] source port number (scount);
[0068] Destination port number (dcount);
[0069] s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com