Encryption method based on dual cycle queue shift and transposition rule
An encryption method and circular queue technology, applied in the traditional encryption field based on double circular queue shift rules and transposition rules, can solve the problems of low speed, low encryption strength, poor operability, etc., and achieve simple transformation, high encryption strength, The effect of fast encryption and decryption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] An encryption method based on double circular queue shift and transposition rules is as follows:
[0028] Step 1] Input the integers m and n, and fill in the plaintext information to be encrypted into the m×n matrix from left to right and from top to bottom to form the plaintext information matrix A;
[0029] Step 2] Create a sequence of random integers X = {r ∈ N, r ≤ max(m, n)};
[0030] Step 3] The user inputs an integer w as the number of matrix transformations according to the encryption strength requirements;
[0031] Step 4] random number k is randomly selected in random integer sequence X, and operation k=k mod 5;
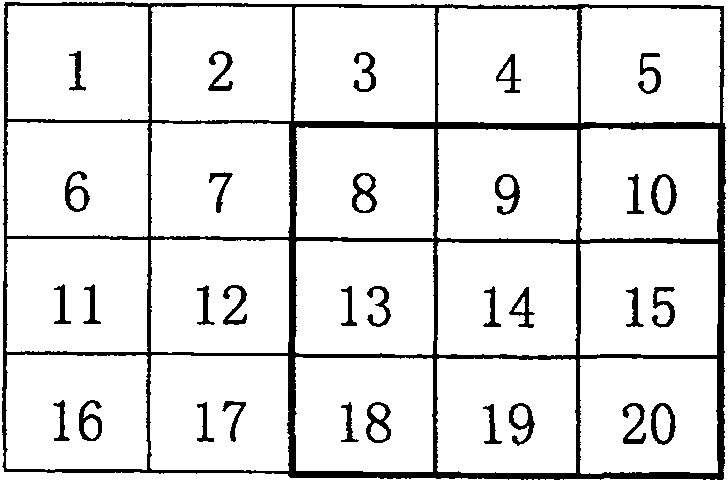
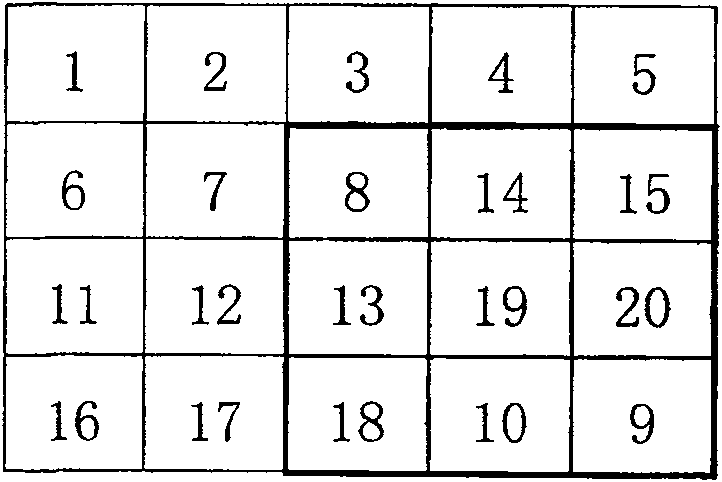
[0032] When k=0, take 4 random numbers L from the random integer sequence X 1 , L 2 , L 3 , L 4 , requiring L 1 3 ≤m,L 2 4 ≤n; then the Lth 1 line as the starting line, with the Lth 3 line as the end line, with the Lth 2 column as the starting column, with the Lth 4 column as the end column, construct the transformation matrix A', and reco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com