A method and device for preventing from spam
An anti-spam and spam technology, applied in the direction of electrical components, digital transmission systems, transmission systems, etc., can solve the problems of denial of service attacks, the inability to limit the spread of worm emails, and the inability to limit the consumption of spam traffic, so as to increase the sending cost , reduce marginal benefit, fine control effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
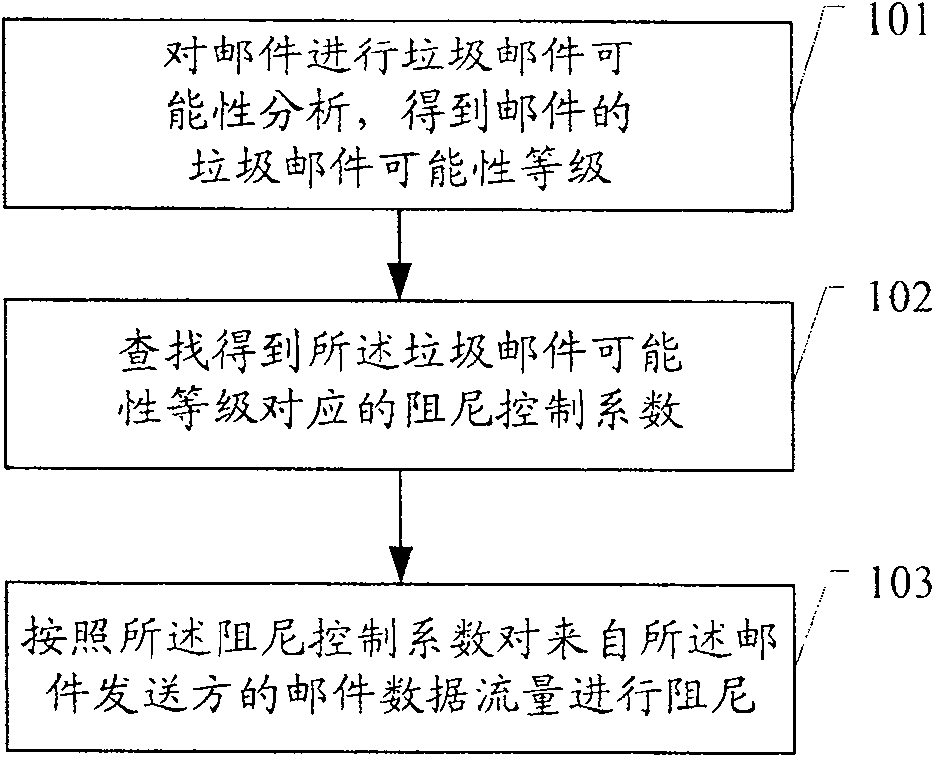
[0042] Embodiment 1. A method for anti-spam, the flow chart is as follows figure 1 shown, including:
[0043] 101. Perform spam possibility analysis on the email to obtain the spam possibility level of the email;
[0044] In this embodiment, after the email has been analyzed for the possibility of spam, after receiving the email, the conventional analysis methods in the existing spam filtering technology, such as whitelist, blacklist, content-based filtering, etc., can be used. This step It is emphasized that the spam possibility level of the email is obtained after analyzing the received email, and the specific analysis method does not constitute a limitation to the present invention.
[0045] 102. Find the damping control coefficient corresponding to the spam possibility level;
[0046] 103. Damping the mail data flow from the mail sender according to the damping control coefficient.
[0047] The present invention introduces the concepts of damping and damping control coe...
Embodiment 2
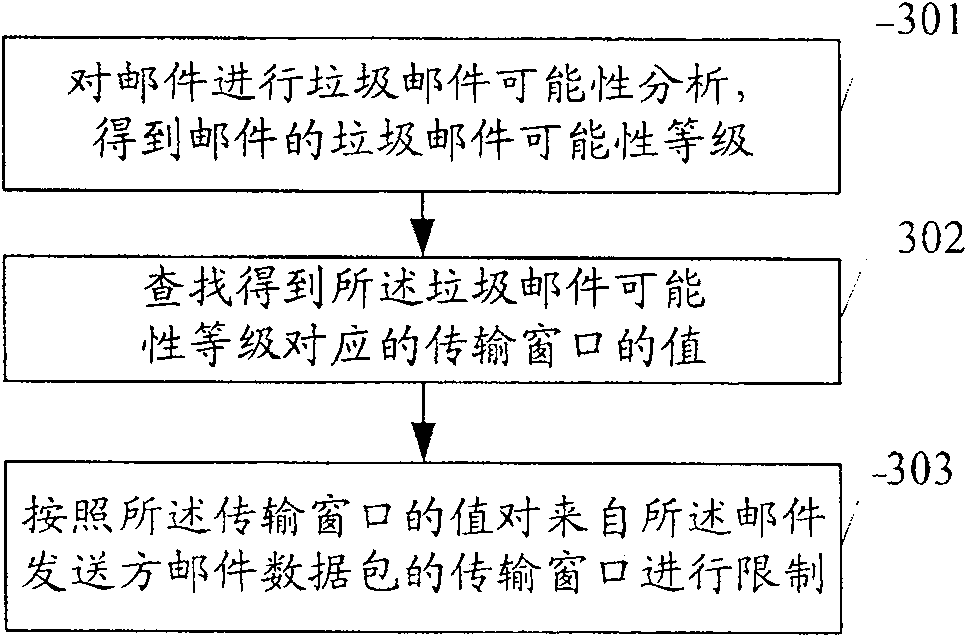
[0052] Embodiment 2, a method for anti-spam, the flow chart is as follows image 3 shown, including:
[0053] 301. Perform spam possibility analysis on the email to obtain the spam possibility level of the email;
[0054] 302. Find and obtain the value of the transmission window corresponding to the spam possibility level;
[0055] 303. Limit the transmission window of the mail data packet from the mail sender according to the value of the transmission window.
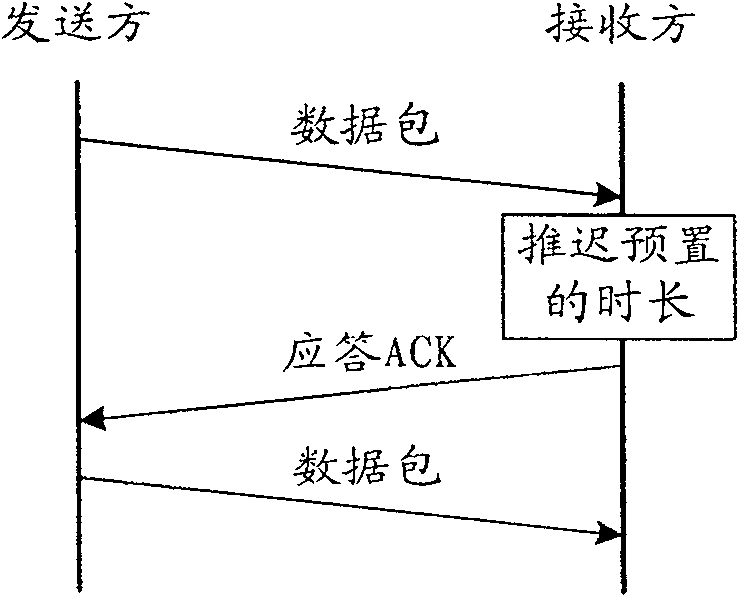
[0056] Please also refer to Figure 4 , which is a schematic diagram of the signaling flow for limiting the data packet transmission window in this embodiment, including:
[0057] The sender sends a connection request;
[0058] The receiver sends a response to the connection request to the sender, and the response includes notifying the sender of the value of the window; in the figure, the value of the window is m bytes.
[0059] After receiving the response, the sender sends a data packet to the receiver, and the...
Embodiment 3
[0061] Embodiment three, a kind of anti-spam method, flow chart such as Figure 5 shown, including:
[0062] 501. Perform spam possibility analysis on the email to obtain the spam possibility level of the email;
[0063] 502. Search and obtain the discarding period corresponding to the spam possibility level for discarding data packets preset by the email sender;
[0064] 503. Periodically discard a preset number of mail data packets for mail data traffic from the mail sender according to the discarding period.
[0065] The difference between Embodiment 3 and Embodiment 1 and Embodiment 2 is that the damping is to discard a preset number of mail data packets for the mail flow from the sender, and the damping control coefficient is to discard a preset number of mail data The discarding period of the packet; the damping mode adopted in this embodiment is based on the timeout retransmission mechanism of the TCP protocol, and the transmission of the mail data flow is hindered by...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com