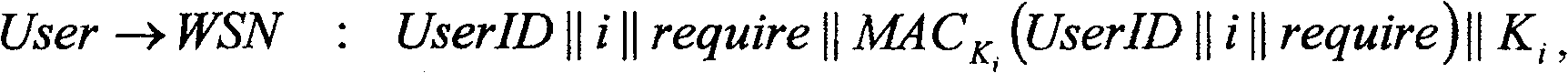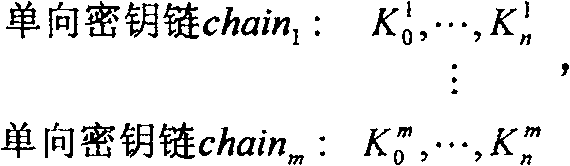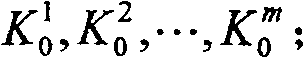Radio sensor access control method based on key chain
A wireless sensor and access control technology, applied to key distribution, to achieve the effect of speeding up the practical process, high security, and reducing storage overhead
Inactive Publication Date: 2011-01-05
XIDIAN UNIV
View PDF0 Cites 1 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
This access control method uses a one-way keychain
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
specific Embodiment approach
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
The invention is based on five highly-effective sensor network access control modes: which are one-way key chain access control, multi key chain access control, Merkle tree-based access control, expanded Merkle tree access control, and an mode of canceling the key chain of captured users with Merkle. The method uses said five access control modes to reduce the storage expense of sensor node and increase the flexibility and expandability of access control so as to support mass users to access network. The invention is compatible with current sensor network data broadcast protocol.
Description
Keychain-based access control method for wireless sensors technical field The invention belongs to the technical field of network communication, relates to wireless ad hoc network security technology, specifically utilizes the principle of a one-way key chain (the key chain is used in the following to replace the one-way key chain) and a Merkle tree, and proposes an energy-efficient The wireless sensor network (WSN) access control method based on the key chain solves the problem of user access control in the wireless sensor network, that is, users with legal identities can send requests to the sensor network, and get a response from the network, rejecting illegal user access. Background technique The sensor network is composed of a large number of small, cheap, battery-powered sensor nodes with wireless communication and monitoring capabilities. These nodes are densely deployed in the monitoring area to achieve the purpose of monitoring the physical world. Wireless sensor...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Patents(China)
IPC IPC(8): H04L12/56H04L9/08H04L9/32H04L12/28H04L29/06
Inventor 沈玉龙裴庆祺马建峰于全尹浩徐启建唐宏杨卫东张红斌
Owner XIDIAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com