Method for binding/recovering key using fingerprint details
A technology of detailed feature points and keys, which is applied in the fields of information security and computer identification, and can solve problems that cannot be reflected and are unreasonable
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
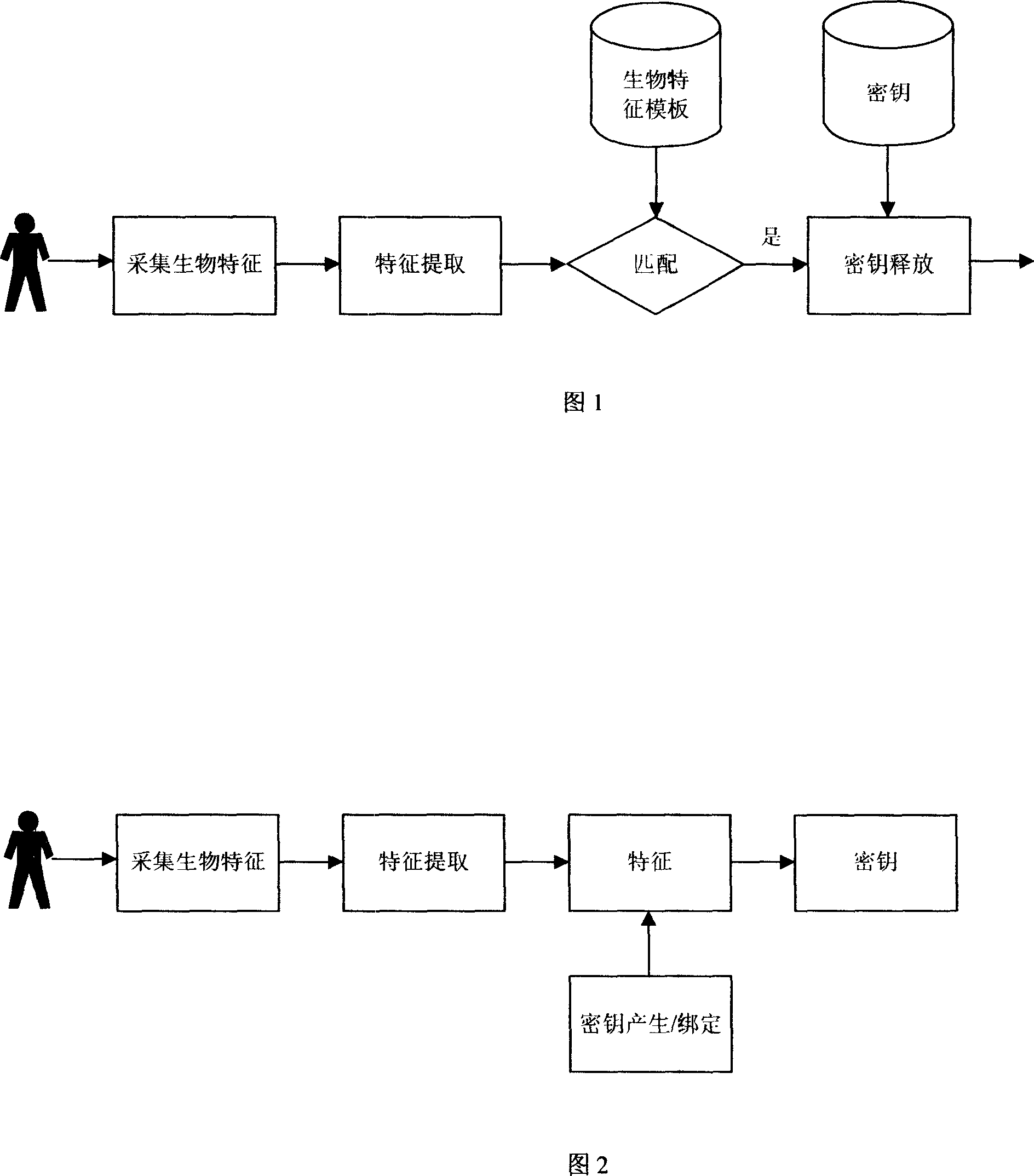
[0018]We bind / recover keys through fingerprint detail feature points. The detailed feature points of fingerprints are usually represented by ridge endings and ridge bifurcations, as shown in Figure 5. The general detail feature points are represented by (x, y, θ), where x and y represent the horizontal and vertical coordinates of the point respectively, and θ represents the tangent direction of the point line (we call it the direction of the detail point). The minutiae points mentioned in the present invention only use their planar coordinates (x, y). While unlocking with minutiae directions can be done better, it compromises security. Because the directions of the minutiae points in each part of the fingerprint image are basically regular, as shown in Figure 6, after the two fingerprint images are aligned, the direction distribution of the minutiae points on the upper, lower, left and right sides of the fingerprint has certain rules. If the direction of the minutiae point i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com