A Linux operation system based voice communication method with CPK authentication
An operating system and voice communication technology, applied in the field of information security, can solve problems such as hidden dangers that are easily deciphered and cannot be changed, and achieve the effect of huge authentication capacity, ensuring security, and eliminating traces of operation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
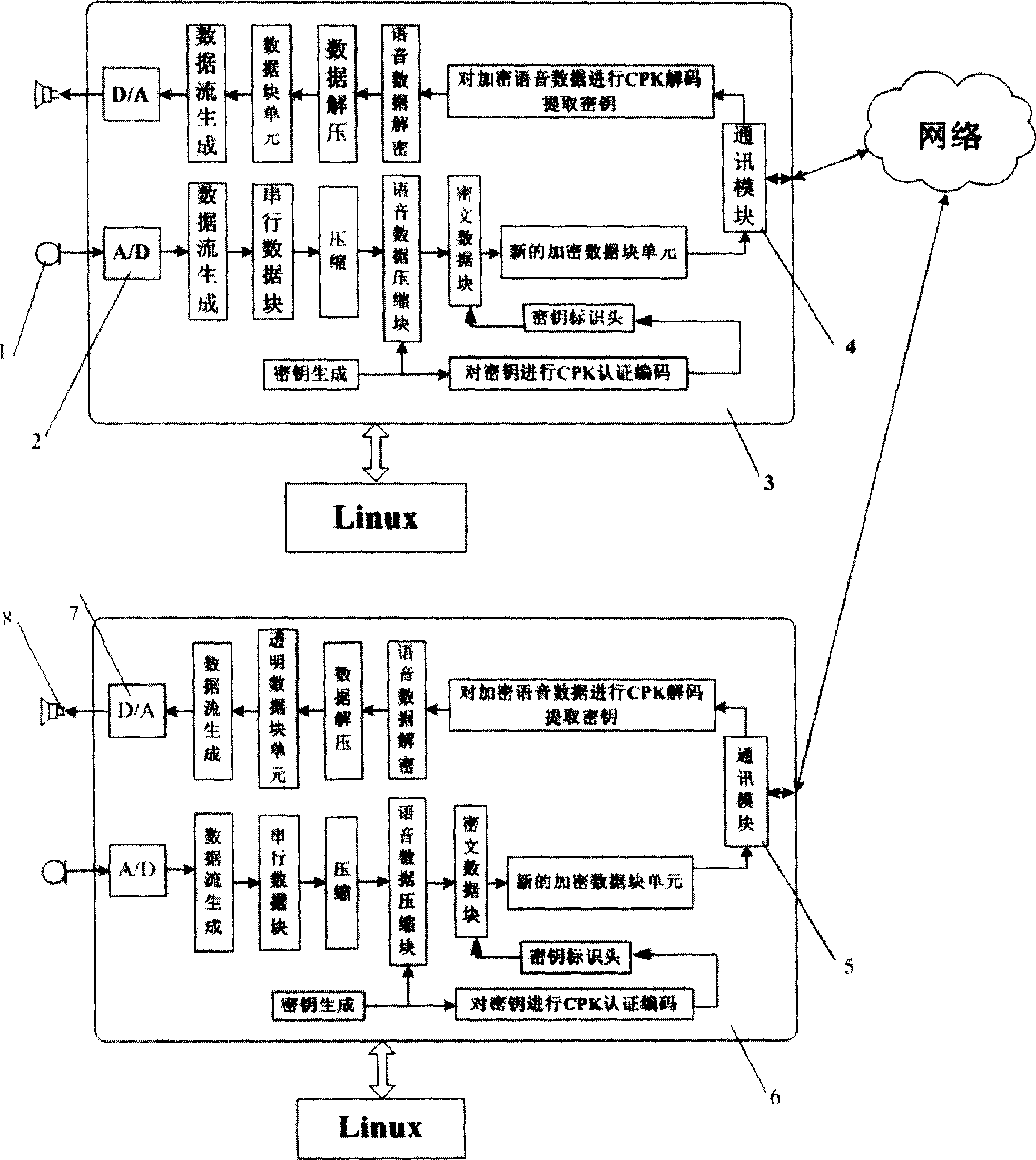
[0022] figure 1 Is the flow schematic block diagram of this method
[0023] see figure 1 , in this embodiment, a mobile phone is taken as an example. In the figure, 1 is a microphone, 2 is an analog-digital converter (A / D), 3 and 6 are ARM9 microprocessors, 4 and 5 are communication modules, 7 is a digital-analog converter (D / A), 8 for the receiver. Both are existing components of mobile phones. The method embeds a Linux operating system and a CPK trusted authentication system in a microprocessor.
[0024] The voice sending process is as follows:
[0025] 1. The microphone 1 at the sending end converts the sound signal into an analog electrical signal, and the voice analog electrical signal is continuously sampled at a rate of 44.1KHz and passed to the analog-to-digital converter 2 in the microprocessor 3, which is converted by analog-to-digital Device 2 continuously digitizes the analog voice to form a data stream, and the Linux operating system packs the data stream in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com